Sandworm Targets, Vehicle Hacks, Phishing Surge, Typo Impersonation

Here’s the fifth edition of the month. It revolves around the top cyber incidents that took place last week. Be it the Poland power grid cyberattack, or the “rn” typo trick used by hackers, the incidents hint towards one thing– increasing sophistication of the campaigns. The edition also talks about the Pwn2Own contest that revealed some serious threats in vehicle infotainment systems. Meanwhile, there’s a sudden upsurge in the multi-phishing attacks that target energy firms.
Poland’s power grid allegedly targeted by notorious, Russia-backed Sandworm group!

Last month was quite devastating for Poland’s power grid. A wiper attack, one of the strongest ones in recent times, targeted the energy grids across Poland. The cyber mishap took place on December 29 and 30 when threat actors managed to penetrate into the systems of two heat and power plants, as well as another system that used to take care of the “electricity generated from renewables (RES).
Poland’s Prime Minister Donald Tusk announced the cyber incident on his official website. The statement also mentioned that “there was no blackout or other negative consequences” because of the cyberattack.
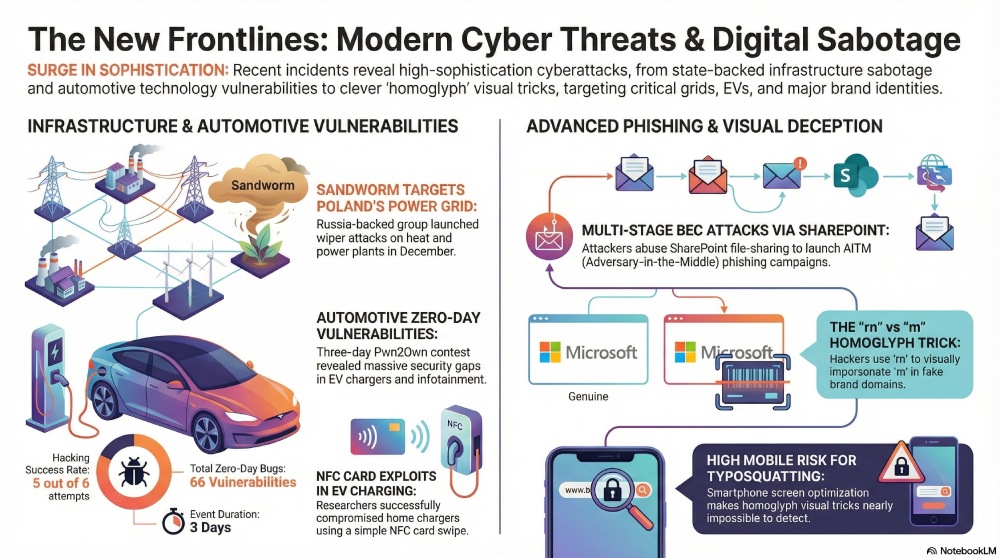
On January 23, a group of researchers from the security firm ESET revealed that the cyberattack was backed by the notorious Russian threat actors, who go by the name of Sandworm. ESET researchers have found great similarities between this attack and the previous campaigns run by Sandworm.
Sandworm has been involved in some of the worst cyberattacks. Back in 2015, the group managed to target the power grid in Ukraine by leveraging BlackEnergy malware. The attack devastated everyday lives by disrupting the electricity supply for several hours. What ESET does not wish to see as a coincidence is the fact that the recent attack on Poland’s power grid took place exactly on the 10th anniversary of the Ukraine BlackEnergy attack.
Pwn2Own contest revealed multiple tactics to hack vehicles!

Who knew that a simple card swipe near any vehicle charging point would help a cybercrook hack into your vehicle! The annual automobile-oriented Pwn2Own contest revealed multiple such vulnerabilities in EV charging and vehicle infotainment systems.
The event, organized in Tokyo, proved to be a game-changer as researchers realized that all it takes is an NFC card to compromise an Autel MaxiCharger AC Elite Home 40A.
The contest is all about the existing vulnerabilities in the IT and operational technology landscape of automobile systems.
It was a three-day contest, and the first two days revealed as many as 66 zero-day vulnerabilities. Jaws dropped as 5 out of every 6 attempts succeeded.

EV chargers seemed to have boosted security systems, and yet they were highly vulnerable to cyberattacks. Similarly, infotainment systems were also highly prone to threat attacks through unpatched bugs.
Multi-stage BEC and phishing campaigns are doing the rounds as they target energy firms
Microsoft has recently warned energy sector firms against a multi-stage phishing campaign. The threat actors have been abusing SharepOint file sharing feature to send phishing links. They have also successfully managed to camouflage their malicious approaches.
After phase one of the attack, the threat actors proceed to launch AiTM attacks, thereby leading to business email compromise (BEC) attacks. Next, the cybercrooks misuse trusted internal accounts to send phishing content both internally and externally. This significantly expands the reach of the campaign.

The campaign was detected by Microsoft Defender XDR as it noticed multiple suspicious sign-ins and fake inbox rules. The experts managed to limit the extent of the attack by effectively disrupting AiTM activity. They also assisted with auto-purging the malicious emails and helped people recover all the impacted identities. The remediation process involved resetting passwords, revoking the session cookies, altering the MFA changes, and eliminating false inbox rules.
“rn” typo used for impersonating biggies like Marriott and Microsoft
Microsoft and Marriott International customers are being targeted by a “homoglyph” phishing campaign. Domains are being registered to impersonate Marriott and Microsoft by combining “rn” that would replace the letter “m.”
This technique is called a homoglyph attack or typosquatting. Such attacks involve visual tricks so that victims cannot spot errors easily.
Netcraft, a security firm, detected multiple such fake domains that are targeting popular hotel brands.The threat actors aim at gaining access to guest data or loyalty account credentials with the help of these malicious websites.

Experts at Anagram also revealed a similar campaign that has been targeting Microsoft for some time. The cybercrooks have been sending phishing emails from fake websites. These websites try to mimic the layouts, logo, and tone of Microsoft. The campaign gets extremely dangerous on smartphones as the optimization makes it almost impossible to detect the difference between “rn” and “m.”
Cybersecurity teams rely on DMARC, DKIM, and SPF to authenticate email, prevent spoofing attacks, and protect organizations from phishing and domain abuse.







