A guide on securing your subscription business from cyber threats in 2025?

Imagine data breaches, payment fraud, or account takeovers hitting your business — sounds scary, right? Unfortunately, these threats are very real if your subscription-based business isn’t protected against cyberattacks.
This is why securing your subscription businesses is of paramount importance today. Since subscription businesses store customer data and manage recurring payments, they have become a prime target for cybercriminals to exploit.
For that matter, it is essential to be proactive in cybersecurity to protect your business. All you need to do is take steps that significantly help protect revenue, maintain seamless working, and secure the trust of your customers.
This blog covers some of the measures that can keep you ahead of the threat actors.
Common online threats to subscription businesses
Online attacks are expensive and can damage your business reputation. These attacks can lead to fraud, stolen accounts, or even misuse of credit card information. This section outlines the most common online threats that your subscription business may encounter:
1. Payment fraud
Payment fraud is among the most prevalent and often unnoticed cyberattacks targeting subscription businesses. It is one of the easiest ways to penetrate automatic payment processes and leave them vulnerable to exploitation. Fraudsters can effortlessly use your customers’ cards to sign up for services. Thus, causing unpredictable account loss, revenue deduction, and chargebacks to them.
Chargeback fraud
It occurs when a real consumer pays but faces challenges with the bank to justify falsely claiming their consent for the payment/transaction made.
Identity theft
Signing up for paid services using stolen personal details can result in mishaps or harm through unauthorized access.
Card testing fraud
In identifying active card details, fraudsters attempt to use multiple stolen cards. They begin with minor or unnoticeable transactions to avoid detection and initially minimize large transactions.
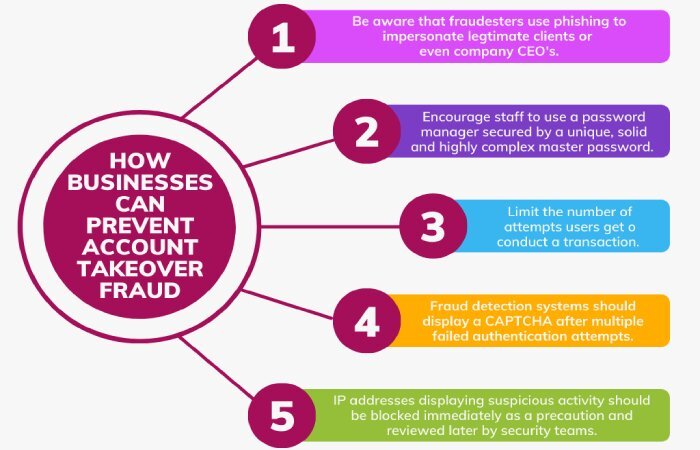
2. ATO- Account Takeover Attacks
Cybercriminals love account takeover attacks because they allow them to store essential payment details, making them a core target. Also, as per a report, as many as 60% of the merchants have witnessed an increase in account takeover attacks.
The unauthorized access to the customer accounts can be taken in three significant ways:
Credential stuffing
Hackers use username-password combinations from previous data breaches, assuming the users will reuse them on other accounts. These websites are not restricted to e-commerce websites or financial institutions, but also social media, gaming, and other such streaming services.
Phishing scams
They occur when hackers use fake emails or websites to deceive people into disclosing their login credentials.
Brute-force attacks
In this attack, bots quickly try various password combinations until they successfully breach an account.
3. Data breach attacks
Data breaches are most definitely a nightmare for subscription businesses. It occurs when an authorized element has access to sensitive business information, such as customer data, names, personal details, and subscription history.
Poor data encryption can even lead to devastating breaches. Here, sensitive information is captured in plain text, exposing it to hackers.
This data breach will result in:
- Lost customer trust.
- Legal repercussions for violating data protection regulations (GDPR, CCPA, PCI DSS).
- Loss of money due to litigation, penalties, and mitigation expenses in breach.
4. Phishing attacks
Here, the attackers create emails and false login pages that are nearly identical to the real ones, and hence convincing enough to deceive customers or employees into disclosing their sensitive information, card details, and login credentials.
Commonly witnessed phishing attacks include:
Email spoofing
Con artists send phony emails purporting to be from your business. They deceive clients into changing their payment information by sending them fake links.
Spear phishing
The hackers use customized communications to target specific executives or staff, making them appear more realistic.
Clone phishing
When cybercriminals replicate emails from your company that appear credible, they replace the original link with a fake one.
5. Insider threats
Sometimes, threats can emerge from within your own company. Insider threats originate from business partners, contractors, and employees accessing sensitive information systems. To avoid any legal threats, you should settle and manage disputes with the parties within.
Common insider threats include:
Malicious insiders
These are the ones who intentionally leak, steal, and misuse your critical business data.
Negligent insiders
They unknowingly expose the data primarily because of weak data protection.
Compromised insiders
Those whose accounts are misused and hacked for fraudulent practices.
You should always be aware of user permissions to avoid malicious activities.
How to secure your subscription business from online attacks?
A well-protected subscription business requires a secure platform that not only enhances security but also supports overall sales success.
This section caters to protecting subscription businesses from online threats, covering everything from payment security to phishing prevention.
1. Measures to strengthen payment security
One of the essential ways to protect your subscription business from payment threats and online attacks is by investing in consistent billing software with built-in security measures. It’s also an optimal choice for escalating customer experience.
Other ways to protect payments from online fraud are:
Embed secure payment gateways
Stripe, Adyen, and others are secure payment tools that utilize automated fraud detection.
Enable 3DS2
3D Secure 2.0 is an additional authentication layer for online transactions, such as biometric verification or one-time password confirmation.
Check on unusual payment patterns
Constant subscription attempts from the same IP address within a short time frame, or an account abruptly using different credit cards, are considered an alert.
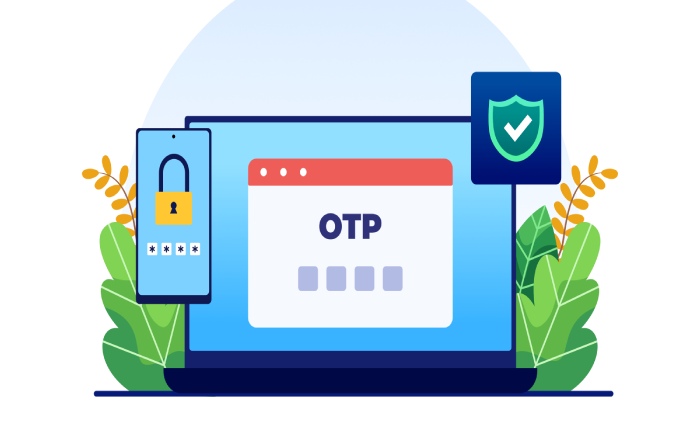
2. Reinforced authentication and access controls
Consider these key security measures to prevent unauthorized access and secure user accounts:
Multi-factor authentication
Biometric verification or one-time passwords (OTPs) are used to prevent unauthorized logins.
Bot protection and CAPTCHA inclusion
Verify real users through CAPTCHA and block credential-stuffing bots to prevent automated online attacks.
Strong password for protection
Unguessable and unique passwords prevent cybercriminals from gaining access to your logins.
3. Protect your APIs
Sometimes, subscription businesses depend on application programming interfaces (APIs) to connect with third-party platforms and tools.
APIs enable seamless processing and integration between services, allowing you to transact, manage data, and automate workflows with ease.
The following measures help you protect your APIs in subscription businesses:
Implement API gateways
These manage, filter, and monitor API traffic while forbidding malicious requests and preventing rate-limiting abuse.
Abide by regular penetration testing
This will find and fix insecurities before an online threat can disrupt your system.
Usage of OAuth 2.0 authentication
This makes sure that only the right people and apps can use your APIs, keeping out anyone who shouldn’t have access.
4. Protect against DDoS attacks.
You should be aware of DDoS (Distributed Denial-of-Service) attacks to discover how to protect your subscription business from online dangers.
Think about the following to defend your service from these attacks:
- Absorbing traffic spikes using a content delivery network (CDN) such as Akamai or Cloudflare.
- Using traffic filtering and rate limitation to stop questionable behavior before it reaches your servers.
- Collaborating with a DDoS protection company to reduce service interruptions and defend against extensive attacks.
5. Make customers and employees aware of phishing.
To protect your subscription business and maintain a credible reputation, it is important to educate customers and employees.
Here are the ways to educate your employees and customers about phishing:
- Abide by proactive email protection protocols such as SPF, DKIM, and DMARC to prevent spoofing emails to your business.
- Timely and regularly train employees to find phishing attempts by spotting suspicious email addresses, unexpected attachments, or unverified links.
- Provide your customers with clear guidelines to help them identify and avoid malicious emails.
The bottom line
Knowledge for protecting your subscription business today is essential for achieving longer-term success.
Cybersecurity isn’t just about breaches; it’s also about establishing your business’s credibility and authenticity. Follow the above measures and best practices to sense, protect, and manage cyberattacks online.
If you need our help in setting up email authentication protocols for your subscription business, then contact us or book a demo.







