Emerging cybersecurity threats that you should know about in 2025
It’s 2025, and cyberattackers are becoming smarter than ever. Outdated software is no longer their prime target. They’re making their way into the everyday rhythm of your business, particularly how you connect, communicate, and build trust with your audience.
If you haven’t guessed already, we’re talking about emails.
For you, email might be a tool to close deals, send invoices, share updates, or onboard new clients. But for attackers, it’s the easiest way to break in. Why? Because email depends on trust, and trust is easy to fake.

From AI-generated phishing emails to fake names and lookalike websites, attackers have already caused serious damage to companies around the world. And unfortunately, these attacks are only getting smarter.
Some of these threats are growing fast in 2025. The best way to protect yourself is to first understand what they are and how they work. In this article, we’ll walk you through a few of the key cybersecurity threats to watch out for this year.
Cryptocurrency scams
Cryptocurrency is the new way to invest, transact, and build digital wealth. But it is also becoming a lucrative target for cyber attackers to prey on.
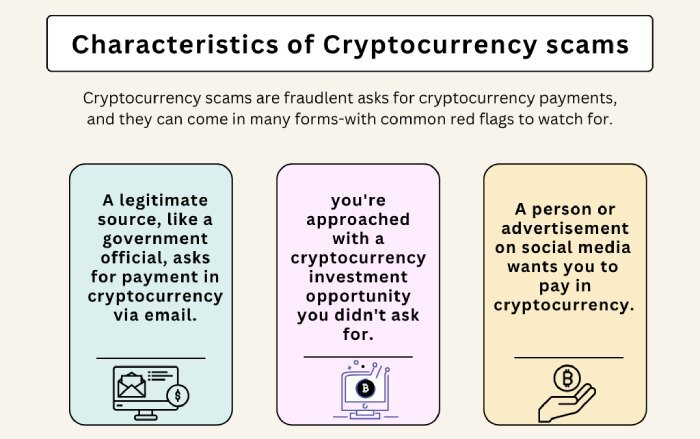
So, when attackers go after crypto users, it’s rarely random; it’s a strategic move. Like any other well-thought-out scam, here, they pretend to be from trusted crypto platforms and send messages that create panic.
For example, they might say, your account has been locked or there’s suspicious activity. Their goal is to prompt you to act quickly, without thinking, so you end up sharing private information, such as your recovery phrase or wallet password.
The danger here is that cryptocurrency payments are irreversible. Once you send money, there’s no way to get it back. There’s no bank to call, no dispute process. That’s exactly what scammers count on. And because most people don’t fully understand how cryptocurrency works, these scams often succeed.

File sharing phishing attacks
Now that most companies and teams are operating remotely or in a hybrid mode, file-sharing tools like Google Drive, Dropbox, and OneDrive have become integral to everyday work. These apps are used to share files, documents, collaborate on projects, and send updates among teams. They have become such an integral aspect of daily tasks that most people don’t think twice when they get a file-sharing notification.
And that’s exactly what these attackers leverage. They know that most people don’t double-check these notifications and often open them without a second thought. As soon as the user opens the file, they are taken to what looks like a normal login page. It might have the same logo and design as Google or Dropbox, but it’s fake. If the user enters their login details, those credentials are sent directly to the attacker.
This kind of phishing is hard to spot because the email itself doesn’t contain a suspicious link. The real danger is inside the shared file. Since it all looks routine, users often don’t realize something’s wrong until it’s too late.

Multi-channel phishing
As you might know, phishing usually starts with a fake email, but these days, attackers are not really stopping there. They’re now following up on other platforms too, like texting you, calling you, or messaging you on apps like WhatsApp. This makes it harder to spot a scam because it feels more real when it comes through multiple channels.
Imagine that you’re receiving multiple messages across various channels; you might as well drop your guard, especially if the message sounds urgent or helpful.
That’s why it’s important to be cautious across all forms of communication, not just email. If something feels off, slow down, double-check, and most importantly, don’t respond right away.
AI-based BEC attacks
No doubt, AI has brought about a revolution in terms of efficiency and creativity. Well, it’s doing the same for cybercriminals. In 2025, a lot of scam emails aren’t written by people anymore; they’re written by AI. And they’re really convincing.

To craft and launch these attacks, attackers use tools like ChatGPT, which do most of the heavy lifting. Specifically, they help plan the message, copy the tone of real people, and make the email sound natural and trustworthy. The result, then, is emails that do not look like a scam at all.
What makes these emails all the more convincing is the publicly available information that attackers can easily find, such as your job title, your team, or recent company news. They use this to make the message feel specific and real.
Email account takeover
This is one of the most dangerous types of email attacks. It’s not just someone pretending to be you; it’s someone actually getting into your email account and using it like they own it.
Usually, it starts when someone falls for a phishing email or uses a weak password that’s easy to guess. For instance, nonprofits, in particular, face heightened risks if cybersecurity practices aren’t clearly defined or implemented, especially as many operate with lean tech infrastructure and staff unfamiliar with digital threats. Donorbox offers practical guidance on cybersecurity for nonprofits to help reduce this exposure.
And with the growing sophistication of AI, attackers may even exploit AI voice cloning technology to impersonate individuals in support calls or internal communication—making human verification even harder. Once the attacker gets in, they can see everything: your emails, files, calendar, and even apps linked to your account. From there, they can steal data, send fake emails to your team or vendors, and cause a lot of damage without being noticed right away.

What can be done?
To stay ahead of ever-evolving cyberthreats, you also need to evolve your strategies and technologies. But as you adopt new approaches, remember, it’s not about technology alone.
What we mean to say is that it is important to use smart security tools and protocols like SPF, DKIM, and DMARC, as they help stop fake emails from reaching your inbox. But just as important is training your team. Your team should know how to spot red flags, pause before clicking, and always double-check anything that feels off.
In the end, the best protection is a mix of smart tools and people who know what to look out for.
If you’re not sure how to go about building a security strategy that makes a difference or configuring authentication protocols for your domain, we’re here to help! Get in touch with us today and let’s get started with your authentication journey!







