5 situations in which your DMARC policy should be ‘p=quarantine’
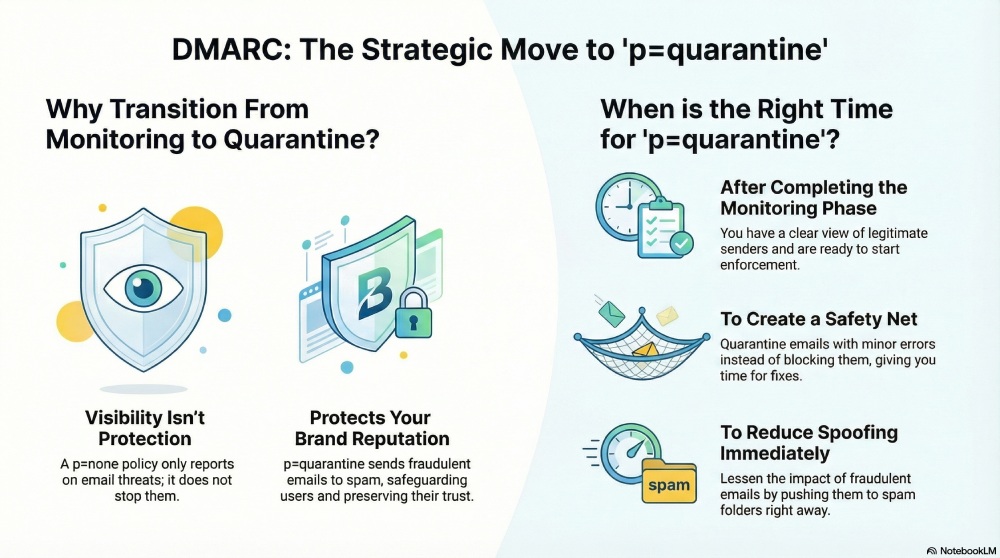
DMARC in monitoring mode provides visibility, but it is not sufficient. After all, visibility alone does not stop abuse. Once you know that there are unauthorized senders sending emails on behalf of your domain, continuing to monitor them without taking any preventive steps serves little purpose.
At this stage, it is important that you start acting on those insights and move to a stricter DMARC policy like ‘p=quarantine.’ The policy instructs the receiving server to send suspicious emails to the spam folder rather than delivering them to the recipient’s inbox. This reduces the risk that your recipients will fall victim to phishing or fraudulent tactics.
In this article, we will walk through five situations where keeping your DMARC policy at ‘p=quarantine’ can help safeguard your email ecosystem while ensuring seamless delivery of legitimate email.

Why you should transition from “p=none” to “p=quarantine”?
There comes a point in your authentication journey when simply observing email activity does nothing to protect your email ecosystem. The insights are redundant if you don’t act upon them.
Keeping your DMARC policy set to “p=none” allows even spoofed and phishing emails to be delivered, ultimately affecting your brand’s credibility and reputation. When recipients receive fraudulent emails that appear to come from your domain, their trust in your brand starts to erode.
Moving to “p=quarantine” helps mitigate this damage by telling the recipient’s server to treat unauthorized emails with suspicion and push them to the spam folder. This way, your users are less likely to interact with those messages and still get a chance to monitor and fix any authentication issues, if they still exist.

So, once you have a comprehensive understanding of who is sending emails on your behalf, which sending sources are legitimate, and which ones are not, the next step is to gradually move to enforcement mode with “p=quarantine.”
When exactly should you configure DMARC with “p=quarantine”?
Your transition from “p=none” to “p=quarantine” should be gradual and strategic. If you stay in the monitoring mode for too long, you continue to keep your domain vulnerable to abuse, and if you directly jump to a stricter policy, chances are that the delivery of even your legitimate emails might be affected.

The right time to configure “p=quarantine” is when you have reasonable clarity over your sending sources, but still want a safety net before moving to full rejection.
Here are a few situations in which you should implement DMARC in “p=quarantine” mode.
After completing the monitoring phase
After completing the monitoring phase, you should have a clear view of all the services and systems that send emails on behalf of your domain. Most of your legitimate email sources should already be authenticated and aligned, with only a few exceptions remaining. Moving to “p=quarantine” at this stage helps you start enforcing DMARC without risking major delivery issues, while still giving you enough room to identify and fix any missed or misconfigured senders.
When minor authentication failures persist

Even after carefully analyzing your DMARC reports, there might still be a chance that some configuration errors persist and a few legitimate emails continue to fail DMARC. This might be due to misaligned DKIM signatures or outdated SPF records. In such cases, it is recommended that you transition to “p=quarantine” instead of switching to “p=reject” as the former allows you to limit the impact of these failures while you work on fixing them.
To safely test mailbox filtering behavior
Not all email service providers treat DMARC failures the same way. Some might send these emails to spam, while others may apply additional filtering or warnings. Either way, these emails are still handled with caution, rather than being trusted right away. This can be a real problem if your domain is configured at “p=none” for an extended period.
But by using “p=quarantine” policy, you can safely observe how different mailbox providers respond to unauthenticated emails, understand the impact on deliverability, and make adjustments before moving to a stricter enforcement policy.
During the gradual enforcement rollout
As we established earlier, if you implement the strictest DMARC policy (“p=reject”), even your legitimate emails might not be delivered to the recipient’s inbox. During gradual enforcement rollout, “p=quarantine” gives you a safer way to move forward. It lets you start enforcing DMARC without immediately blocking emails. This helps you spot any missed or misconfigured sending sources and fix them, while ensuring your legitimate emails continue to be delivered properly.
To reduce spoofing without full rejection
If your DMARC reports show some spoofing attempts, but it’s too soon to completely block unauthenticated emails just yet, “p=quarantine” is the most appropriate middle ground. This policy helps reduce spoofing by pushing unauthenticated emails to spam, making them less effective, while still avoiding the risk of blocking legitimate emails that may be misconfigured.
To sum up
When it comes to protecting your domain with DMARC, taking small yet strategic steps is the right approach.
Monitoring helps you understand your email traffic, like who is sending emails on your behalf, if there are any spoofing attempts, and how the receiving servers are treating your emails, but it does not actively prevent abuse. To truly protect your domain, you need to act on these insights.

Gradually moving to “p=quarantine” policy actually helps you bridge the gap between monitoring and full enforcement. It allows you to limit the impact of spoofed and unauthenticated emails while giving you time to fix any remaining issues in your email setup.
If you are struggling to strike that balance between security and control, “p=quarantine” policy is the way forward. It lets you mitigate the risk of phishing and spoofing while still leaving room for improvement, so that your email delivery stays seamless and secure.
To know more about DMARC enforcement and how to go about it, reach out to us.







