Tools Used During a DDoS Attack — A Comprehensive Guide
In today’s digitally connected landscape, Distributed Denial of Service (DDoS) attacks represent one of the most disruptive and persistent threats to online infrastructure. Whether the target is a global e-commerce platform, a government portal, a small business website, or a cloud-based application, DDoS attacks aim to drain resources, block legitimate traffic, and render services unavailable — often with devastating business impact.
In this comprehensive guide, DMARCReport explores what DDoS attacks are, how they function, the different tools threat actors use to launch them, and the essential knowledge security professionals need to defend against these attacks.
What Is a DDoS Attack and Why Does It Matter?
At its core, a Distributed Denial of Service (DDoS) attack seeks to overwhelm a target system — such as a web server, API endpoint, or network device — with an enormous volume of traffic or resource requests. When the attack traffic exceeds what the target can handle, legitimate user traffic slows down or stops completely. The result? Downtime, service disruption, loss of revenue, and reputational damage.
DDoS attacks matter because they can:
- Crash e-commerce and business systems at critical moments (e.g., Black Friday sales).
- Impact public sector services, leading to citizen frustration and potential safety risks.
- Exacerbate security threats, since attackers may use DDoS as a distraction from other malicious activity.
To truly understand the mechanics behind these attacks, we must first examine how they are executed and what tools enable them.
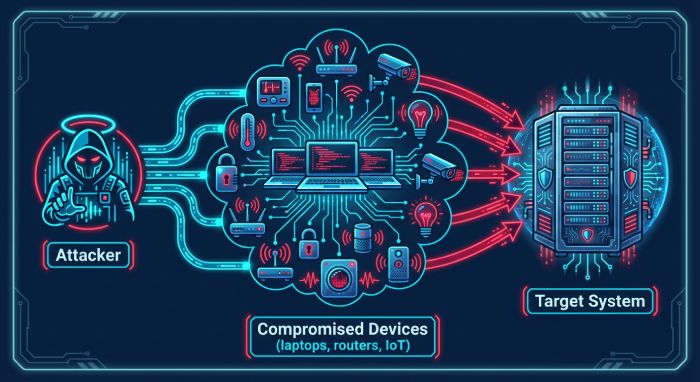
DDoS Fundamentals: How It Works
Unlike a typical blockage caused by an individual device, a DDoS attack generates incoming traffic from many different sources — making it difficult to stop by simply blocking one IP address.
Usually an attacker gains control of many internet-connected devices (computers, routers, IoT devices, etc.) through malware or misconfiguration. Once compromised, these devices become part of a botnet — a large network of “zombie” systems that can be remotely coordinated.
When the attacker triggers the botnet, each device begins to send malformed or high-volume requests to the target simultaneously. The target’s capacity is overwhelmed and services are rendered unavailable.
This distributed nature is what gives DDoS attacks their power and complexity. It means defense strategies need to be proactive, scalable, and adaptive.
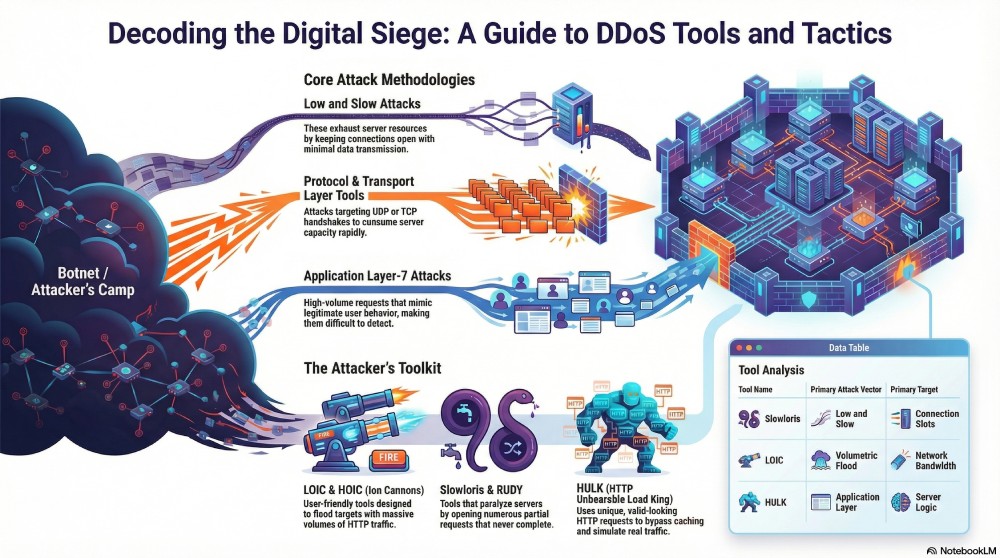
Categories of DDoS Attack Tools
DDoS attack tools vary broadly in design, complexity, and purpose. While some were created for legitimate testing by network engineers, many have found misuse by bad actors. Below are the major categories of tools used in DDoS attacks:
1. Low and Slow Attack Tools
These tools send small amounts of data very slowly over many connections. The intention isn’t to flood the system with high traffic volume, but to exhaust connection resources by keeping sessions open for a long time.
Low and slow tools are particularly dangerous because:
- They can bypass basic rate limits.
- The traffic often looks legitimate.
- They remain under common detection thresholds for longer.
2. Protocol and Transport Layer Tools
These attack tools target weaknesses in networking protocols such as UDP (User Datagram Protocol), TCP, or ICMP. The volume can be high, or they may exploit protocol behavior to consume server resources rapidly.
Examples include UDP flood tools or SYN flood generators that exploit the initial handshake processes of network communications.
3. Application Layer-7 Tools
Application layer tools attack the highest layer in the OSI networking model — the layer responsible for actual user requests and application interaction. Because this traffic mimics normal user behavior, it’s much harder to detect and block.

Application layer attacks often resemble high volumes of HTTP requests or form submissions that appear legitimate on the surface.
Most Commonly Used DDoS Attack Tools (with Context)
Below is a detailed look at some of the most well-known and widely misused tools in the world of DDoS attacks. Many of these began as stress-testing programs for developers, but in the wrong hands — they become potent weapons.
1. LOIC (Low Orbit Ion Cannon)
One of the oldest and most widely recognized DDoS tools, LOIC is simple to use and designed to send massive volumes of UDP, TCP, or HTTP traffic to a target.
LOIC became infamous during high-profile hacktivist campaigns such as Operation Payback, where volunteers used it collectively to target anti-piracy organizations.
Although simple in design, LOIC is powerful in coordination and can bring down poorly protected servers.
2. HOIC (High Orbit Ion Cannon)
HOIC is essentially an evolution of LOIC — with additional capabilities that make it more capable of overwhelming targets with higher volumes of HTTP requests.
It can target multiple URLs simultaneously and offers options for boosters — script files that enhance attack potency.
3. HULK (HTTP Unbearable Load King)
HULK specializes in simulating legitimate web traffic, making detection more difficult. Unlike brute-force floods, the traffic appears as valid HTTP requests that require server processing.
This method targets application logic rather than raw bandwidth.
4. Slowloris
As the name suggests, Slowloris takes advantage of how web servers handle multiple connections. It opens numerous partial HTTP requests and keeps them alive without completing them.
Each incomplete request continues to consume server resources until no slots remain available — blocking legitimate users.
5. Tor’s Hammer
Operating inside the Tor network, this tool sends continuous, slow, legitimate-looking HTTP connections that can bypass some firewall restrictions.
Although slower than other tools, it benefits from Tor’s anonymity and difficulty of source tracing.
6. RUDY (R U Dead Yet?)
RUDY focuses on sending slow, long-form POST requests that mimic legitimate form submissions.
Servers treat these as valid operations, and the continuous open connections add up to a denial-of-service condition.

7. DDoSISM
Originally developed for testing server resilience, DDoSISM can simulate attacks with random IP spawns and varied techniques to evaluate infrastructure responses.
In malicious contexts, it’s leveraged to generate chaotic, unpredictable traffic patterns.
8. Golden Eye
Golden Eye works by sending persistent HTTP requests and keeping connections alive, bypassing some caching and CDN systems in the process.
Its dual role in both testing and exploitation has made it a frequent tool in real-world DDoS events.
9. PyLoris
PyLoris brings SSL support, SOCKS proxies, and multiple protocol options to the table. It can operate across Windows, Linux, and Mac, making it flexible yet stealthy.
The ability to mix protocols increases its adaptability against varying targets.
The Reality of DDoS Tools Today
Modern DDoS incidents don’t always involve these classic tools. Many attackers now leverage botnets of compromised devices, exploit misconfigured services for amplification (e.g., DNS amplification), or rent DDoS-for-hire services that offer easy attack launches anywhere.
Additionally, advanced threat groups have developed platforms that dynamically alter attack patterns, blending attack vectors and avoiding signature-based detection.
Defending Against DDoS Attacks — Tools You ShouldUse
Understanding offensive tools gives defenders a huge advantage — but knowing how to defend is equally important. Organizations should deploy:
Network Traffic Analysis Tools
These monitor real-time traffic and detect anomalies that signal a DDoS ramp-up.
Web Application Firewalls (WAFs)
WAFs inspect application traffic and block suspicious requests — especially helpful against Layer-7 floods.
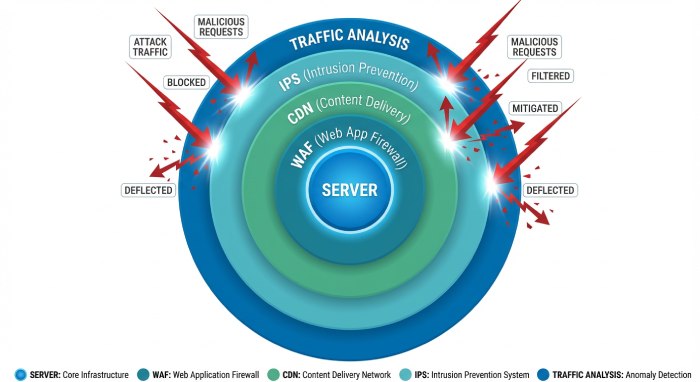
Intrusion Detection & Prevention Systems
By identifying malicious traffic patterns early, IDS/IPS tools can stop attacks closer to their source.
Content Delivery Networks (CDNs)
CDNs distribute requests across global points of presence, reducing the impact of large-scale attacks.
Rate Limiting & Filter Rules
Limiting request rates per IP or region can blunt the impact of volumetric attacks.
Final Thoughts
DDoS attacks are no longer simple “internet noise” — they are sophisticated threats backed by evolving tools and tactics. From classic tools like LOIC and Slowloris to modern attack services and botnet-driven assaults, the landscape is constantly shifting.
Security professionals must stay educated about both offensive and defensive tools, including email authentication mechanisms such as SPF, DKIM, and DMARC. Regular testing, layered defenses, real-time traffic monitoring, and partnership with experienced DDoS mitigation services are now essential components of any comprehensive cyber defense strategy.
Understanding how attackers operate — and the tools they use — isn’t just academic. It’s a prerequisite for building systems that remain secure, resilient, and available when it matters most.







