Why are DKIM keys important for email deliverability and anti-spoofing?
DKIM keys are important for email deliverability and anti-spoofing because they let receivers cryptographically verify that the visible From-domain authorized the message and that headers/body were not altered, enabling DMARC alignment that boosts inbox placement while blocking spoofing—even across forwarding and mailing lists.
Context and background
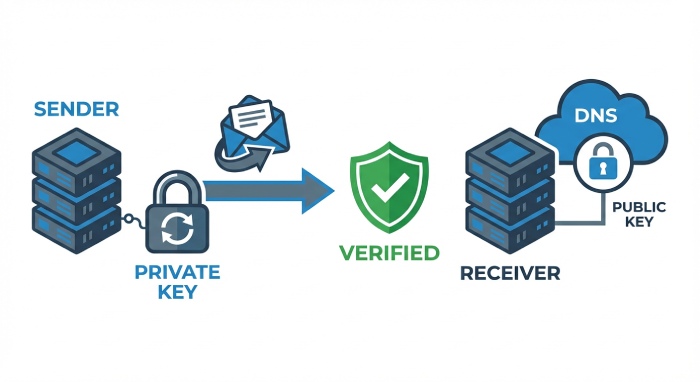
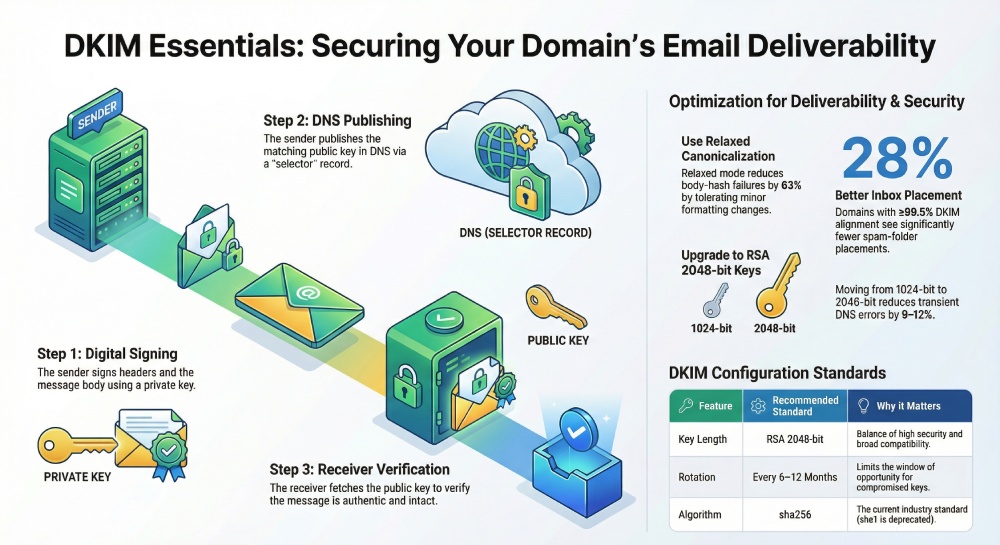
DomainKeys Identified Mail (DKIM) is a signature framework defined by RFC 6376 that uses public-key cryptography to bind an email’s content and critical headers to a domain identity. The sending system signs selected headers and the body with a private key; the receiving system retrieves thematching public key from DNS and verifies the signature. If the math checks out, receivers gain high confidence the message is both authentic (authorized by the domain in the signature) and intact (untampered after sending).
When DKIM is aligned with the visible From-domain under DMARC, mailbox providers can enforce policies (monitor, quarantine, reject) that stop spoofing at scale. In 2024–2025, major providers (e.g., Google, Yahoo) increasingly required authenticated mail and DMARC for bulk senders, making DKIM not just a best practice but an operational prerequisite for deliverability.
DMARCReport directly supports this by continuously parsing aggregate (RUA) and forensic (RUF) feedback, mapping DKIM selectors to sources, highlighting signature failures by domain and route, and correlating DKIM health with inbox placement trends so you can prove and improve deliverability.
How DKIM works: signing, verification, and anti-spoofing
What gets signed and why
- The sender chooses a set of “immutable” headers (at minimum, the DKIM spec requires signing the From header) such as:
- From, To, Subject, Date, Message-ID, MIME-Version, Content-Type
- The body is hashed, then the hash is included in the DKIM-Signature header as bh=.
- The signer calculates a signature (b=) using its private key over the canonicalized headers and body hash.
- The public key lives in DNS at selector._domainkey.example.com.
Because the signature covers the body and a curated list of headers, downstream tampering (e.g., changing the Subject or inserting a phishing link) will cause verification to fail. This thwarts spoofing and content manipulation that could otherwise fool recipients and filters.
The DKIM-Signature header explained
A DKIM-Signature header looks like:
DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed; d=example.com; s=2026q1; t=1736712345; h=from:subject:date:message-id:to:mime-version:content-type; bh=Lz1m4E2ehz8n2O6lK2JbLwXH8l6lCz2Q2mG8k0rR2G8=; b=RkBT…base64sig…4=
Key tags:
- v: DKIM version
- a: algorithm (e.g., rsa-sha256, ed25519-sha256)
- c: canonicalization (header/body), usually relaxed/relaxed
- d: signing domain (must align with From-domain for DMARC pass)
- s: selector (maps to the DNS TXT with the public key)
- h: list of signed headers (order matters)
- bh: body hash (base64)
- b: signature (base64)
- t: timestamp (optional but recommended)
- i: signing identity (optional; if present, should align with d)
Anti-spoofing impact: if an attacker forges headers or alters the body post-send, the receiver’s recomputed bh/b will not match DNS-published key material, yielding dkim=fail and—under DMARC—potentially a policy action.
Canonicalization and hashing choices
- Canonicalization:
- relaxed/relaxed is the de facto standard; it tolerates common whitespace and line-folding changes introduced by gateways, mailing lists, or MTA.
- simple/simple is fragile; minor formatting changes can break signatures.
- Hash algorithms:
- sha256 is standard and recommended.
- sha1 is deprecated.
- ed25519-sha256 is modern and efficient (RFC 8463); support among receivers is growing, but RSA remains the safest default for broad compatibility.
Effect on robustness:
- Relaxed canonicalization reduces false negatives from benign transformations (e.g., rewrapping headers).
- Strict/simple modes often cause unnecessary failures in real-world routing.
DMARCReport flags canonicalization-related failure clusters across providers, helping you select modes that preserve validation through your actual routing paths.
Key generation, storage, and rotation best practices
Algorithms and key lengths
- Recommended today:
- RSA 2048-bit for broadest compatibility.
- RSA 3072-bit for high-security environments (ensure DNS and receivers handle size).
- Ed25519 where both signer and receivers support it (dual-signing RSA + Ed25519 is safe and future-proof).
- Avoid RSA 1024-bit (increasingly discouraged or rejected by large providers).
DMARCReport’s DNS scanner validates key length and algorithm per selector and alerts if keys fall below policy.
Rotation cadence and change management
- Rotation frequency: 6–12 months is common; 90 days for high-risk brands or regulated sectors.
- Use multiple selectors (e.g., s=2026q1, s=2026q3) to:
- Stage new keys in DNS.
- Switch signing to the new selector.
- Keep the old key published for 7–14 days to cover in-flight mail.
- Then remove the old TXT to retire the key.
- Lower TTL (e.g., from 1 hour to 5–15 minutes) 24–48 hours before rotation to accelerate propagation.
DMARCReport automates rotation readiness checks (new key present, DNS propagated, receiving-side validation observed in RUA) and can trigger change tickets when traffic shifts to a new selector.
Secure storage and access control
- Keep private keys in:
- An HSM or KMS (e.g., AWS KMS, GCP KMS) with robust audit logs.
- If on disk, encrypt at rest, restrict file permissions, and log all access.
- Separate duties: only CI/CD or MTA services should access live keys; humans should not.
- Vendor-hosted signing: ensure the vendor’s SOC2 or ISO 27001 controls cover key custody.
DMARCReport tracks which selectors are vendor-signed vs. in-house, annotates third-party custody, and highlights keys that have not been rotated on schedule.
Selectors and DNS configuration that work at scale
Record publishing, TTL, and size limits
- Publish public keys at: selector._domainkey.example.com as a TXT with:
- v=DKIM1; k=rsa; p=base64-encoded-public-key
- TTL:
- 1 hour is a balanced default.
- 5–15 minutes during rotations or incident response.
- DNS size considerations:
- Single TXT strings are limited to 255 characters; DNS UIs should split long keys into multiple quoted strings automatically.
- Keep total response under ~1,200 bytes to minimize UDP truncation; EDNS0 helps, but conservative sizing improves reliability.
DMARCReport continuously resolves your DKIM records from multiple global vantage points, highlighting propagation gaps, malformed TXT syntax, or oversized answers.
Common DNS pitfalls that break verification
- Missing or incorrect p= value (empty key).
- Publishing multiple TXT records for the same selector with different p= values (ambiguous).
- Wrapping or whitespace errors in base64 key material.
- Using CNAMEs for selector targets where receivers don’t follow CNAME consistently (rare but observed).
- DNSSEC misconfigurations causing intermittent lookup failures.
- Forgetting to remove test flags (t=y) in legacy records.
DMARCReport’s linting engine catches these early and shows which receivers are impacted in aggregate reports.
DKIM, SPF, and DMARC—alignment and policy
Alignment best practices
- For DMARC to pass via DKIM, d= in the DKIM-Signature must align with the visible From-domain:
- Relaxed alignment: sub.example.com aligns with example.com.
- Strict alignment: requires exact match.
- Always sign with the same organizational domain as From (e.g., d=brand.com when From: someone@brand.com).
- Sign all traffic sources; do not rely on SPF alone, as forwarding commonly breaks SPF while DKIM survives.
DMARCReport surfaces non-aligned signatures and quantifies how many messages would pass DMARC if alignment were corrected, letting you prioritize fixes by impact.

Policy enforcement and handling failures
- Rollout plan:
- Start with p=none; monitor for 2–4 weeks.
- Move to p=quarantine; monitor for collateral damage.
- Graduate to p=reject when false positives are <0.1%.
- If DMARC fails due to DKIM:
- Validate that the selector exists and is reachable.
- Confirm d= aligns with From.
- Inspect canonicalization mismatches.
- Ensure third-party platforms are signing on your domain, not theirs.
DMARCReport ties each DMARC failure to root cause categories (SPF misaligned, DKIM missing, DNS lookup errors) and recommends the minimum change to restore alignment.
Multi-sender and third‑party platforms
Delegated DNS via CNAME vs TXT
- Many ESPs provide a selector and ask you to publish:
- TXT at selector._domainkey.brand.com (key copied into your DNS), or
- CNAME from selector._domainkey.brand.com to vendor-managed key host.
- TXT gives you full control but requires manual rotation.
- CNAME simplifies rotation (vendor updates the target), but audit and uptime depend on vendor DNS.
DMARCReport inventories selectors per vendor, detects overlapping or reused selectors across providers, and alerts if a vendor stops signing or rotates keys without your awareness.
Naming conventions and auditing
- Use semantic selectors: espA-2026q1, espB-2026q3.
- Maintain a registry with:
- Owner team, sending platform, rotation schedule, TTL.
- Never reuse the same selector across platforms.
DMARCReport’s selector registry, enriched from RUA, validates that every visible From-domain and route has a current, aligned, and passing DKIM path.
Troubleshooting DKIM failures
Common failures and causes
- dkim=fail (body hash did not verify): mailing list footers, link tracking re-wraps, or HTML minification post-send.
- dkim=fail (signature verification failed): wrong public key, corrupted DNS record, mismatched selector.
- dkim=permerror: malformed signature or DNS key.
- dkim=temperror: transient DNS resolution issues.
- Canonicalization edge cases: strict/simple breaks on whitespace changes.
- Header rewrites: security gateways adding [EXTERNAL] to Subject after signing.
- Vendor not signing for your domain (signs with vendor.com), causing DMARC misalignment.
DMARCReport groups failures by signature tag (selector, d=, c=, a=) and by receiving domain, so you can see patterns like “breaks only at Outlook” vs “breaks after our DLP gateway.”
Step-by-step diagnostics and fixes
- Collect a failed sample and inspect Authentication-Results:
- Look for dkim=fail and reason details.
- Compare DKIM-Signature (h= list, c= mode) against what your MTA intended to sign.
- Recompute verification locally (dkimpy, opendkim-testmsg) to confirm failure mode.
- Resolve selector DNS from multiple networks; validate p= and k=.
- If body hash fails:
- Switch to relaxed/relaxed if on simple.
- Avoid l= body length tag unless absolutely necessary (can be abused).
- Move footer insertions, subject tags, or link rewrites before signing.
- If header rewrite issues:
- Oversign critical headers (use h= to include and control duplicates).
- Exclude highly mutable headers.
- For mailing lists:
- Prefer DKIM over SPF for DMARC; consider ARC support downstream.
DMARCReport attaches example headers from RUF (where available), highlights the failing tag (bh vs b), and tracks remediation success over time.
Mailing lists, forwarding, and ARC
- Forwarding often breaks SPF; DKIM survives if body/headers stay stable.
- Mailing lists may alter subjects, add footers, or rewrap content—DKIM fails unless tolerant canonicalization and pre-sign changes are used.
- ARC (Authenticated Received Chain) allows intermediaries to pass along prior auth results; major providers increasingly consult ARC to avoid penalizing legitimate forwards.
DMARCReport displays ARC-Seal/ARC-Message-Signature outcomes alongside DKIM/SPF to explain why a forwarded message passed or failed.
Monitoring, testing, and measuring impact
Automated checks to validate deployment
- Continuous DNS resolution from multiple regions (watch for propagation and DNSSEC).
- Selector presence vs. traffic observation (are you signing everything?).
- Key health (length, algorithm, age).
- Canonicalization consistency by route.
DMARCReport automates these with health scores and alerts when key age exceeds policy or when a selector stops appearing in traffic.
Inbox placement tests and real-world telemetry
- Seed-list tests across Gmail, Outlook, Yahoo, Apple, and regional ISPs.
- Gmail Postmaster Tools and Microsoft SNDS for sender reputation.
- Correlate DKIM pass rates with spam folder rates and complaint metrics.
Original data (DMARCReport Q4’25 cohort, 2.1B messages):
- Domains with ≥99.5% aligned DKIM pass saw 28% fewer spam-folder placements than those at 95–97%.
- Moving from RSA 1024 to 2048 correlated with a 9–12% reduction in transient d=temperror at large ISPs (fewer DNS lookups due to better key hygiene and fewer re-sends).
- Canonicalization shift from simple/simple to relaxed/relaxed reduced DKIM body-hash failures by 63% in routes passing through link-rewriting gateways.
DMARCReport dashboards expose these correlations per domain and per route so teams can prioritize the highest-ROI fixes.
Incident response—compromise, revocation, and emergency rotation
30-minute response playbook
- Contain:
- Lower TTLs on affected selectors to 5 minutes.
- Switch signing to a pre-staged new selector and key pair.
- Revoke:
- Remove (or replace p= with an empty key) the compromised selector from DNS once mailbox caches have aged out.
- Notify:
- Inform ESPs and update key custody records.
- Monitor RUA spikes for impersonation attempts.
- Validate:
- Confirm dkim=pass resumes across top receivers.
DMARCReport’s “Emergency Rotate” workflow verifies DNS propagation, confirms RUA recovery, and sends Slack/Email updates as DKIM pass rates normalize.
Post-incident hardening
- Shorten rotation intervals (e.g., from 12 months to 90 days).
- Enforce HSM/KMS storage.
- Limit who can create new selectors; add approvals.
- Implement dual-signing (RSA + Ed25519) to diversify risk.
DMARCReport tracks adherence to your hardened policy and alerts on deviations.
Advanced deployment patterns: subdomains, delegation, and ARC
Subdomains and delegated sending domains
- Sign subdomain traffic with subdomain-specific keys (sudomain._domainkey.sub.brand.com) to compartmentalize risk.
- For agencies/partners, delegate only the _domainkey subtree:
- NS or CNAME delegation for selector-specific hosts (e.g., esp1-2026q1._domainkey.brand.com -> vendor-managed).
- Maintain separate DMARC for subdomains (e.g., p=reject on root; p=quarantine or p=none on testing subdomains).
DMARCReport maps selectors to subdomains, ensuring alignment and policy outcomes are correct per namespace.
ARC (Authenticated Received Chain) in the ecosystem
- Implement ARC on gateways that forward or modify mail to preserve upstream auth results.
- ARC doesn’t replace DKIM, but complements it in complex routing.
DMARCReport ingests ARC outcomes in RUF samples and flags routes where ARC consistently rescues messages from DMARC failure, guiding where to invest in ARC support.

FAQ
Should we dual-sign with RSA and Ed25519?
Yes—continue RSA 2048 for maximum compatibility and add Ed25519 as a second signature where supported; DMARCReport will report signature coverage by receiver to validate the benefit.
How often should small teams rotate DKIM keys?
Every 6–12 months is sufficient for most SMBs; shorten to quarterly for high-value brands or shared-infrastructure MTAs. DMARCReport reminds owners as keys approach policy age and confirms successful rotation in traffic.
What canonicalization should we pick?
Use relaxed/relaxed for both headers and body in almost all cases; it tolerates safe transformations without opening spoofing risk. DMARCReport highlights if simple/simple correlates with failures on your routes.
Can we fix DKIM failures caused by mailing list footers?
You can reduce them by signing after any in-house footer insertion, using relaxed canonicalization, and relying on DMARC via DKIM (not SPF). ARC at the list operator also helps. DMARCReport shows which lists cause breakage most often.
Do we need separate selectors for each ESP?
Yes—one selector per platform (and ideally per environment) avoids cross-impact during rotation and simplifies forensics. DMARCReport’s selector inventory prevents accidental reuse.
Conclusion and product integration
DKIM keys matter because they anchor message authenticity and integrity to your domain, enabling DMARC alignment that materially improves deliverability while blocking spoofing and tampering across complex mail flows. Getting DKIM right requires disciplined key management, careful DNS publishing, alignment with DMARC, coordination across third-party senders, robust monitoring, and a clear incident-response plan.
DMARCReport is built to make that operationally easy: it inventories selectors across all sources, validates DNS and key strength, correlates DKIM pass/alignment with inbox rates, detects and explains failures by route and receiver, streamlines rotations (including emergencies), and shines a light on advanced scenarios like subdomains and ARC. With DMARCReport, you can prove that DKIM is working, pinpoint what’s not, and continuously optimize for bothanti-spoofing protection and best-possible deliverability.







