Commission MDM Breach, Singapore Cyber Alliance, Senegal DAF Breach

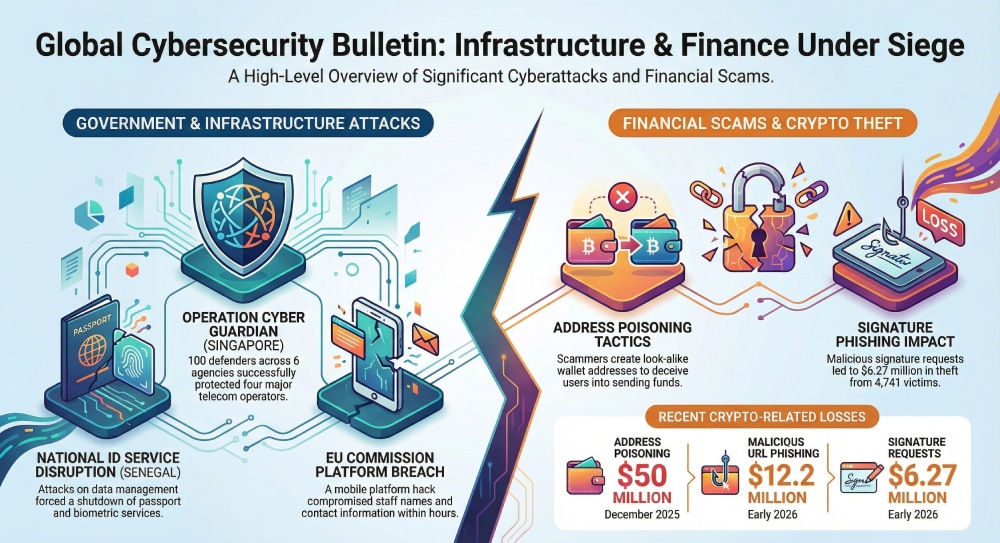
Here’s the bulletin for week 2 in February. Last week focused on cyberattacks targeting critical infrastructure, including the European Commission and Singapore’s telecommunications sector. Meanwhile, multiple crypto users have fallen prey to address poison scams. Also, the Senegal threat attack managed to disrupt crucial government services, leading to panic and confusion.
European Commission’s mobile device management platform got hacked!
Cybercrooks managed to break into the mobile device management platform of the European Commission on 30th January. The European Commission jumped into action immediately and discovered that the threat actors were unable to access the mobile devices. They managed to limit the extent of damage. The entire system was cleaned to remove any traces of the cyberattack, all within 9 hours. As of now, the European Commission is strictly monitoring the security setup, bolstering cybersecurity, and evaluating the cyber mishap to further boost protective measures

The Commission issued an advisory stating that data for some staff members (names and contact numbers) has been compromised.
The cyber incident is being investigated by the European Computer Emergency Response Team (CERT-EU). Experts believe the stolen data can be misused by cybercriminals to attempt to access login credentials. The same data can be easily used by threat actors to carry out manual targeting on users or spear phishing attacks.
This is not the first time that the Commission has been targeted by hackers. Something similar happened back in 2021 when this Commission and a few other European Union organizations were targeted by threat actors. There is still no information available as to who attacked the Commission around that time and what kind of attack it actually was.
The biggest ever coordinated cyber defence organization in Singapore to combat a massive cyberattack against mobile operators!

Back in 2025, Singapore’s state security agencies managed to circumvent a massive cyberattack on the four major mobile operators, namely, M1, Singtel, StarHub, and Simba Telecom. It was an advanced persistent threat (APT) actor, also known as UNC3886, which managed to target all four telecom operators in July 2025. The security agencies carried out an operation called Operation Cyber Guardian to thwart the malicious intentions of the threat actor.
UNC3886 used intricate tactics to penetrate the networks of these four mobile operators. The hacker also abused a zero-day exploit to successfully bypass firewalls so as to operate without being detected.
Soon, the telecom operators were able to detect the threat attempts. UNC3886 did manage to access “a few critical systems” of the telecom operators, but because of their proactive approach and swift response, the cybercrooks could not access any sensitive data.
IMDA, CSA, and a couple of other concerned authorities joined hands to investigate this threat attack. This is apparently the largest ever coordinated cyber defence operation organized in Singapore, and it involved a team of 100 defenders representing six different government agencies.
A surge in email-based cyberattacks highlights the critical importance of implementing DMARC, SPF, and DKIM protocols to protect organizations from phishing and spoofing threats.
Senegal’s cyberattack on DAF led to disrupted government operations

The Directorate of File Automation (DAF) was recently targeted by threat actors. The cyber incident served as a stark reminder of how fragile the nation’s most sensitive data systems are.
DAF is a government agency responsible for sensitive data management, including national ID cards, biometric records, passports, and electoral data. Due to the cyberattack, DAF briefly shut down critical operations. The service disruption affected the lives of millions of Senegalese citizens. They could not access essential identity services for a temporary period.
DAF issued an official public notice to inform the public of the decline in production capacity for national ID cards due to a cyber incident. A great sign of relief is that no personal data was compromised in this cyber incident.
Steep rise in crypto attacks due to address poisoning scams
Crypto users lost millions of dollars at the beginning of 2026 because of an address poisoning scam. Signature phishing scams are also adding fuel to the fire. A victim lost a whopping $12.2 million after he copied a malicious URL.
A similar address poisoning scam targeted people back in December 2025, which resulted in losses worth $50 million.
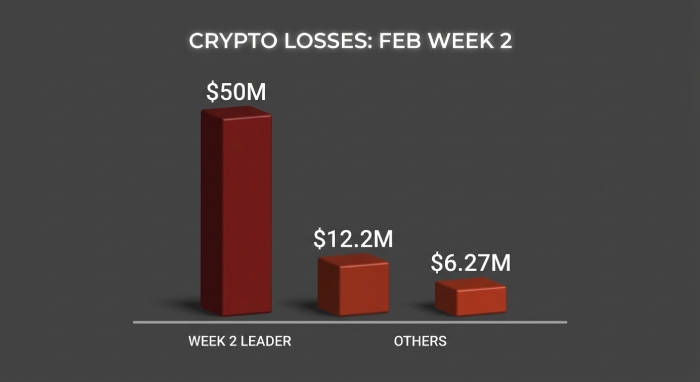
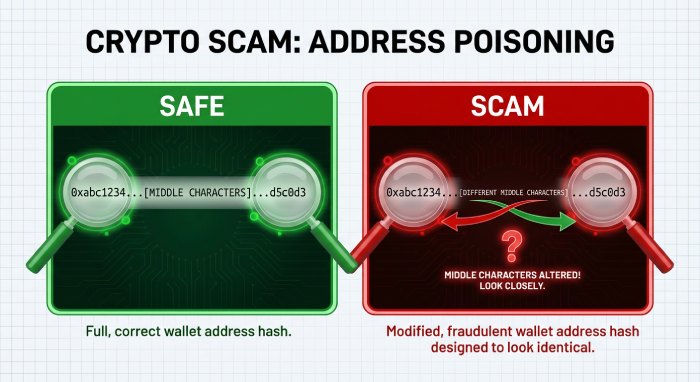
According to the Scam Sniffer, the address poisoning tactic is quite popular among cybercrooks to wipe out huge amounts from crypto wallets. Threat actors create addresses that resemble the first and last characters of a trusted wallet. They make subtle changes to the middle section. This creates a sort of visual illusion and makes it almost impossible to detect the malicious changes. Signature phishing attacks have also led to theft worth $6.27 million from around 4741 victims. They did so using malicious signature requests.