Dell Laptop Vulnerable, Zero-Trust Migration Pending, WSU Threat Surge
Hola people! August is here, and so are we! Once again, we bring to you a fresh dose of cybersecurity news to help you combat the increasing threat of cyberattacks. Our ultimate goal is to make you aware of the cyber threats that are currently circulating. The only way you can safeguard your sensitive data from these sophisticated cybercrooks is to educate yourself about the latest cybersecurity trends.
This week, we are going to discuss the Dell laptop vulnerabilities, the zero-trust initiative being pushed by the US government, and the increased instances of cyberattacks at WSU.
So stay with us and keep reading to secure your data!

Your Dell laptop can be prone to cybersecurity attacks!
If you are a government official, working professional, or cybersecurity expert and own a Dell laptop, here’s something you must know! Millions of Dell laptops, especially those from the Latitude and Precision series, are prone to serious cyber threats.
Cybercrooks target the Broadcom BCM5820X security chip, which is embedded in Dell’s ControlVault3 firmware. The vulnerabilities, also known as ReVault, enable the threat actors to gain easy access to your biometric data, passwords, and other sensitive details.

Experts believe that the consequence of the ReVault attack on Dell laptops can be severe. The most concerning part about ReVault vulnerabilities is that the device tends to stay compromised even after a complete reinstallation of Windows.
ReVault also enables threat actors to cause physical attacks on the compromised device. If a threat actor manages to gain physical access to your Dell laptop for a brief period of time, they can conveniently open the chassis and then access the USH board with the help of a custom connector.
A compromised Dell laptop with tampered ControlVault firmware can also be configured in a way that it accepts faulty fingerprint authentications. Researchers have literally used spring onions to unlock a compromised laptop.
Dell has taken cognizance of the sensitive issue and is working actively with Broadcom to develop firmware updates soon. Dell has already notified its customers about the security concerns. It has also been releasing security patches regularly to keep the users safe.

Zero-trust migration is still under consideration to limit threat attack damages
The zero-trust network designs gained popularity during the Biden administration. But the initiative is still being considered under the Trump administration. Government agencies are still being encouraged to deploy the zero-trust system.
According to Michael Duffy, the acting federal chief of information security, implementing artificial intelligence in day-to-day operations should be backed by a zero-trust system to ensure complete cybersecurity. Basically, this system creates multiple obstacles for the cybercrooks who manage to break into your device. These hurdles significantly limit the extent of damage by quarantining crucial parts of the network and require a stringent authentication process.
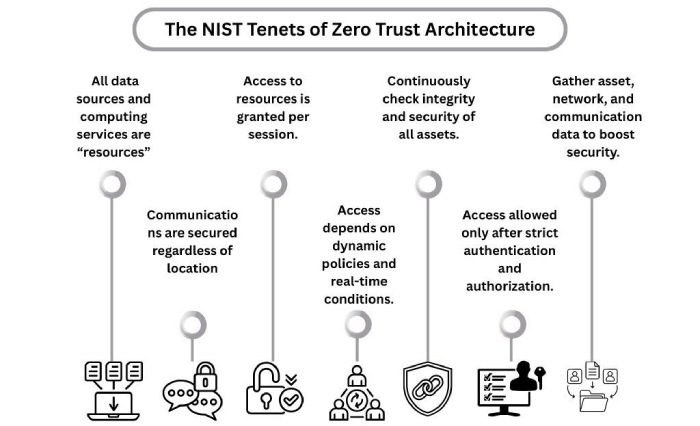
Duffy said that even though the Biden administration is no longer there, zero-trust architecture continues to be an important part of ongoing cybersecurity measures. The Trump administration sees potential in certain cyber priorities that Biden tried to incorporate during his tenure.
WSU witnesses a sudden rise in threat attacks just before financial aid disbursements!
The Washington State University (WSU) is experiencing a sudden spike in the instances of cyberattacks just ahead of the financial aid disbursements. As a result, the Information Technology Services (ITS) at WSU has boosted its security efforts. ITS has been deploying improved login as well as authentication processes in order to combat phishing attacks and account takeover risks. These security measures may lead to certain changes in the login process for the WSU community members. They have stated that there is nothing to worry about this minor change in the login process and that it’s just a part of the boosted security protocols.
This is not the first time that cybercrooks have targeted an educational institute. According to Educause, the US has been experiencing a sudden spike in financial aid fraud. Upto 2020, the annual financial aid fraud would result in losses of under $10 million. However, by 2023, the annual losses had hit the $100 million mark.
The officials at WSU have urged all the students and other users to stay vigilant and practice cyber hygiene. They have advised users not to share their authentication codes or passwords with anyone else. Deploying multifactor authentication can also help in thwarting the risk of phishing attacks. To boost cybersecurity, many organizations now use DMARC, DKIM, and SPF to prevent email spoofing and phishing. Any suspicious login activity should also be reported as soon as possible. ITS has issued a warning that even a single case of account compromise can lead to malicious redirection of the payroll deposits.
WSU, as well as ITS, have been working in close coordination to prevent any unfortunate malicious incident. However, they believe that every user must act vigilantly to ensure the security mechanism is foolproof.







