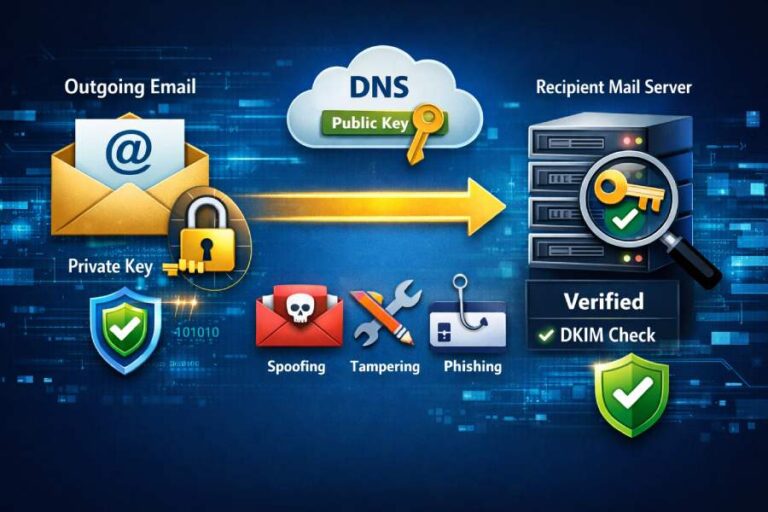
What are common issues revealed by DMARC aggregate reports and how should I prioritize them?
DMARC aggregate reports most commonly reveal SPF and DKIM authentication and alignment failures, unauthorized/forged senders, misconfigured internal or third‑party systems, and configuration pitfalls (SPF include limits, missing/rotated DKIM selectors, forwarding/mailing list artifacts, subdomain policy mismatches), and you should prioritize remediation in this order: 1) high‑volume spoofing that fails both SPF and DKIM, 2) legitimate business‑critical…