Dropbox Scam, MFA Bypass, Journalists targeted, Email Spoofing

The first edition of February revolves mainly around phishing attacks. While a new type of phishing campaign is doing the rounds that involves targeting PDFs and Dropbox, notorious cyber gang ShinyHunters seemed to have bypassed MFA in their latest cyberattack. Meanwhile, multiple journalists are being targeted by misusing the Signal messenger. An Indian firm fell prey to a threat attack and lost around $610 K USD.
New phishing campaign targeting PDFs and Dropbox services to steal credentials
AI tools are making it easy for threat actors to level up their threat campaigns. While cybercrooks are getting sophisticated with their threat attacks, they still prefer to carry out simple phishing campaigns because of the rate of success.
A group of researchers at ForcePoint has discovered a new phishing campaign that involves PDF files and Dropbox storage. It is a multi-stage threat campaign that redirects victims to malicious pages to gain access to their credentials.

When a victim clicks on a malicious PDF, they get redirected to a Dropbox login page. It is basically a malicious page designed to carry out fraud activities like account takeover, internal access, etc. Cybercrooks prefer this campaign as it looks similar to normal business behavior, which further increases its credibility.
First, the victim receives a legitimate-looking email. The email will mostly revolve around tender procurement or any business operations. Along with it comes a request to evaluate the attacked document.
The PDF works like a primary malware delivery system. The sender address tends to be spoofed. After being redirected to the malicious Dropbox login page, the victim is highly likely to log in using their email address and password. These malicious emails easily bypass traditional authentication tools such as SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting, and Conformance).

ShinyHunters managed to bypass MFA in a recent data theft attack!
MFA or multi-factor authentication is considered to be a great tactic to prevent cyberattacks. But in a recent cyber incident, ShinyHunters managed to bypass MFA during a social engineering attack.
In this cyber incident, ShinyHunters targeted SoundCloud, Crunchbase, Panera Bread, and several dating apps, including Match, Hinge, OkCupid, and Tinder. A group of researchers at Silent Push believes that there can be more victims of ShinyHunters, especially those who belong to financial services, real estate, logistics, fintech, healthcare, energy, and so on.

Mandiant believes that, in addition to ShinyHunters, there are two other independent threat groups that are also deploying the same tactic to bypass MFA.
These threat actors tend to pose as IT customer support executives and use vishing calls as well as real-time adversary-in-the-middle infrastructure to gain access to OKTA SSP credentials and OTPs.
Okta is an access management service provider and believes that threat actors are using tailor-made phishing kits that have been specially designed to help live-call-based cyberattacks. Experts believe that any type of MFA that is not resistant to phishing can be easily bypassed because of this new cyber campaign.

Signal Messenger used to target journalists
Unknown threat actors have been trying to gain access to multiple journalists’ accounts by using Signal Messenger. Most of them are investigative journalists. While some are well-known faces on television, others are from large and medium-sized media outlets. Besides journalists, reputed individuals and prominent figures of society, such as lawyers, are also being targeted.
Threat actors send a message through Signal Messenger and pose as a customer support executive. They allege that someone is engaging in suspicious activity on the victim’s phone and attempting to access sensitive data. They then ask the victim to complete a Signal verification process and share a verification code with the executive.

When the chat request on Signal Messenger is accepted by the victim, they receive a verification code on their smartphone. Sharing this code with the Signa Security Support Chatbot enables attackers to gain access to the victim’s account.
An Indian firm was duped because of a fake email!
Indian infrastructure firm Megha Engineering and Infrastructures Ltd. fell prey to a massive phishing scam and lost almost $610 K.
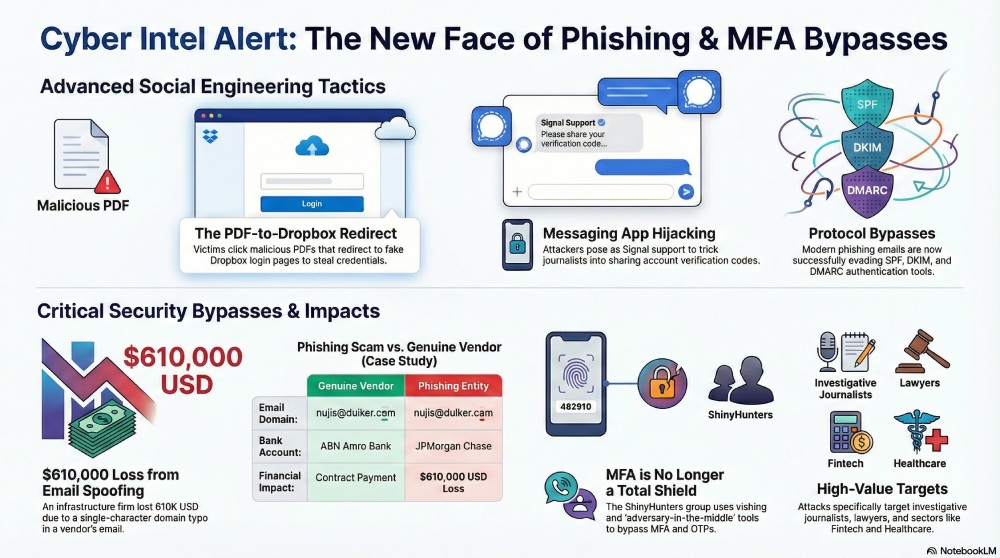
MEIL needed to buy burner packages and a reaction furnace package from a Netherlands-based vendor. Payments were to be made in accordance with to signed contract. But a group of threat actors managed to impersonate the vendors and tampered with the payment instructions by using a malicious email ID. As a result of this tactic, MEIL transferred the payments to a fraudulent JPMorgan Chase account rather than the genuine ABN Amro Bank account.
On November 29, threat actors sent a fake email to MEIL claiming that the vendor’s original bank account is no longer functional because of a court order. The cybercrooks used a fake email address- nujis@duiker.cam, in place of nujis@duiker.com.
MEIL considered the email to be genuine and transferred payments to the fraudulent account in January 2025.





