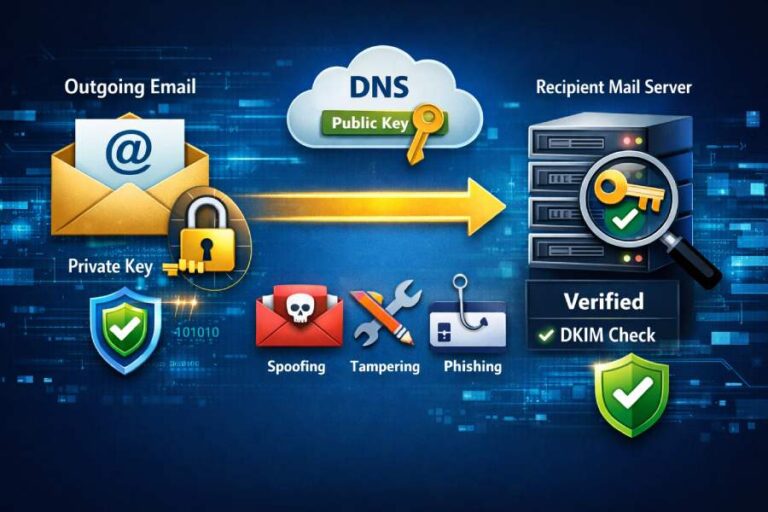
What are common mistakes people make when setting up DKIM TXT records?
The most common mistakes when setting up DKIM TXT records are syntax errors (quoting/semicolons/base64), selector/domain mismatches, incorrect key splitting or record type, weak or outdated keys and unsafe rotation, DNS propagation/TTL missteps, canonicalization/algorithm mismatches, and ignoring DMARC/SPF alignment requirements. DKIM (DomainKeys Identified Mail) uses a public key published in DNS to verify that a message’s…