Credential Theft, Phishing warning, Instagram Alert, Bettermement Breach

The third edition of the month revolves around key cybersecurity incidents. Cyber mishaps this week include a breach of Facebook login credentials, phishing attacks that exploit email routing gaps, fake Instagram password reset emails that sent a panic wave among the Indian user base, and a customer data breach at Betterment.
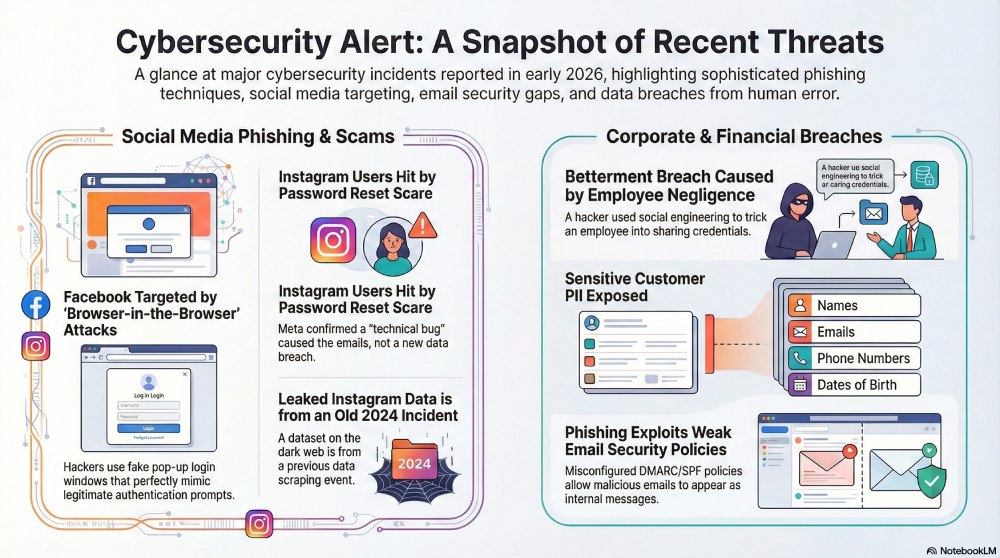
Facebook login credentials accessed by leveraging the Browser-in-the-Browser technique
Facebook has a huge user base of around 3 billion active users. This is exactly why hackers treat this social networking platform as a treasure trove of data. According to a group of cybersecurity researchers, the second half of 2025 experienced a sudden spike in Facebook phishing scams. Experts believe that the “Browser-in-the-Browser” technique is being used to extract data at a large scale.

The Browser-in-the-Browser or BitB technique is a highly sophisticated phishing tactic. The process involves creation of a custom-built, malicious login window that pops up on the target’s browser tab. It successfully mimics the original Facebook authentication prompts.
The false pop-up window consists of a Facebook URL, which makes it almost impossible even for proactive and wary users to set it apart from a legitimate Facebook page.
Hackers send malicious emails while posing as the XYZ law firm. The phishing email talks about infringing content andlegal notices. Such emails often contain malicious URLs that redirect victims to malicious Meta captcha pages. This creates an added layer of deception and earns the credibility of the victim.

Microsoft urges users to stay wary of phishing attacks that abuse email routing gaps.
Cybercrooks are leveraging weak DMARC/SPF policies and misconfigured MX records to give an “internal” and credible appearance to malicious emails, as well as avoid detection by security tools.
The Threat Intelligence team at Microsoft has discovered that cybercriminals have been misusing intricate email routing and misconfigured domain protection systems.
The loophole lies with the recipient email servers that interpret the incoming emails. Because of intricate email paths, DMARC enforcement and SPF hard-fail often do not work properly.In that case, a phishing email can easily reach the inbox of the target with an “own” address in both the From and To fields. This spoofed email successfully creates an illusion of the email being sent internally.

At other times, the hackers can sometimes alter the sender name to further boost the credibility of the email, while using a legitimate internal email address in the From field.
Experts suggest using stringent DMARC protocols and SPF hard fails. Further, it is important to set up all the legacy mail relays, spam filters, and archiving services correctly.
Instagram security alerts send shock waves among Indian users
Multiple Instagram users received Instagram password reset emails, triggering a fear of a mind-numbing data breach among the Indian user base. While Meta has denied the risk of a data breach and termed the incident a mere technical bug, the incident once again reminded users of the threat around these social networking apps.

Meanwhile, a leaked dataset is doing the rounds on darkweb. Meta claims that the leaked data is related to data scraping that most likely happened back in 2024. Malwarebytes, a renowned cybersecurity company, has found a spreadsheet on the dark web that contains data like Instagram usernames, addresses, phone numbers, emails, etc.
Meta’s statement has made it clear that an external party leveraged a bug to send password reset emails to the users. However, no data breach took place.
Massive customer data breach at Bettermement due to an employee’s negligence!
Betterment has published a data breach notification on its official website. The notification states that a hacker managed to trick one of the employees into sharing their login credentials for a third-party software platform.
The cybercrook is yet unknown. It is highly likely that they have used the identity impersonation technique to get access to the sensitive data. They chose social engineering tactics over attacking the technical infrastructure.
Betterment has mentioned that the cybercrooks have already started sending “fraudulent, crypto-related messages that appeared to come from Betterment.”
There has been no clarity yet around the number of people impacted in this cyber incident. Betterment has claimed that they take cybercrimes “very seriously” and that they have managed to revoke any kind of unauthorized access. A full-blown investigation is also underway.
Betterment has claimed that no customer accounts were breached as they are safeguarded “by multiple layers of security.”
However, the cybercrooks managed to gain access to highly sensitive personal data like email addresses, names, phone numbers, postal addresses, dates of birth, and so on.
Betterment has urged its customers to stay careful and be wary of any unexpected communications.







