How can the government and public sector agencies protect their domains with DMARC?

Emails from government or public sector agencies are not just a means of communication or dissemination of important information; they also reinforce trust and authority. Imagine if someone receives a fraudulent email from a seemingly official government address, the trust they place in that institution would be shattered.
After all, it is more than just about an individual’s loss; it reflects a security gap for the citizens of the nation and erodes their confidence in public systems. To mitigate such risks, it is important that your institution implements the right strategies and tools. One such critical tool that every organization (whether government or private) must have in its cyber defense arsenal is DMARC.
To put it simply, DMARC helps ensure that emails sent from your domain are genuine and not from fraudsters pretending to be you. It works together with SPF and DKIM to verify emails, block fake ones, and provide reports on suspicious activity. This keeps official communication secure and helps maintain public trust.
In this article, we will dig deeper to understand what DMARC does and how it protects government agencies from falling prey to email fraud.
Why does email security even matter for public sector domains?
When receiving an email from a public sector domain or a government agency, your readers might treat it as critical and credible, but that’s not always the case. Such fraudulent emails easily slip through the cracks and make their way into the inboxes of unsuspecting citizens.
Since these users inherently trust the government’s identity, they are more likely to open such emails, follow instructions, or share personal and financial details, which is exactly what cybercriminals want.
Here’s why email security is a non-negotiable for the public sector:
- The recipients might ignore sketchy-looking messages from a shopping website but not from a government office
- The reach of government emails is huge. One such email is enough to dupe millions of people at once.
- They affect critical services. A single bad email can disrupt healthcare, defense, or disaster response systems.
How are governments across the world implementing DMARC?
Email security for these agencies is very different from that of private organizations. With private companies, the goal is just to protect customer data; if public sector domains are at risk, national security is at stake. This is why you should be proactive, structured, and thorough in implementing DMARC.
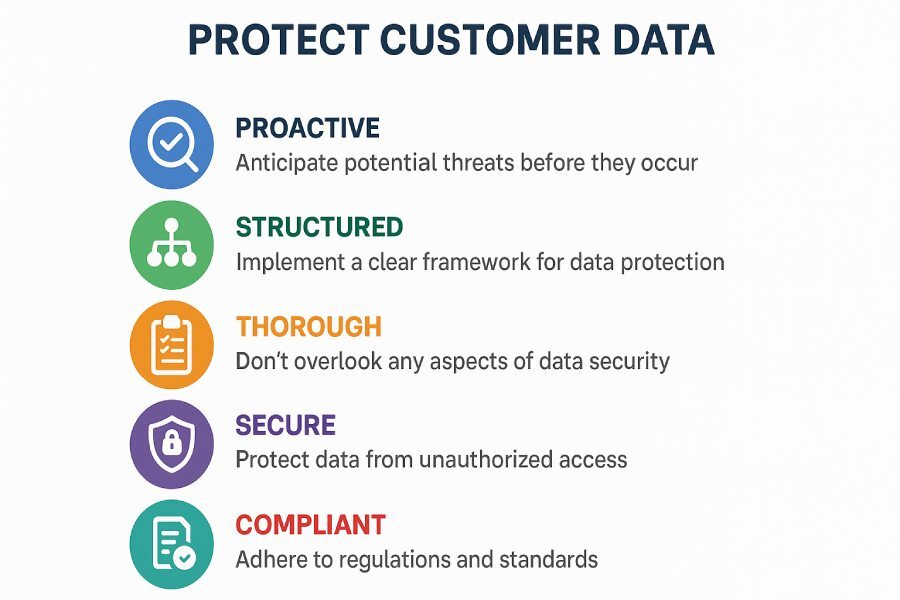
Here’s how governments across the world are doing it:
United States
In the US, the Department of Homeland Security (DHS) issued a directive called BOD 18-01, which requires all civilian federal agencies to set up SPF, DKIM, and DMARC and send regular reports on their email activity.
United Kingdom
The UK government made it mandatory for all government domains to have a DMARC policy set to “p=reject”, the highest enforcement level. This means that any unauthenticated or suspicious email is blocked before it reaches recipients.
Germany
In Germany, all internet service providers and public sector domains must implement SPF, DKIM, and DMARC to prevent email-based scams.
New Zealand
Under the Secure Government Email (SGE) Framework, all email-enabled government domains must use DMARC with “p=reject”, SPF with hard-fail (-all), and DKIM signing for every outgoing email.

How should government and public sector domains implement DMARC?
Implementing DMARC for government agencies is not a one-and-done approach. It must be structured and well-planned.
Here’s how you can go about it:
Map every sender
Create an inventory of all the IPs, services, and vendors that send emails using your government domain or its subdomains.
Implement SPF and DKIM for a strong foundation
Once you have a list of authorized servers and addresses, publish it on a valid SPF record. Next, enable DKIM signing for all outgoing mail, and make sure your public DKIM keys are available as DNS TXT records. Be sure to test these protocols thoroughly before moving to the next steps.
Publish a monitored DMARC record
After you have configured SPF and DKIM, the next step is to implement DMARC.
In the early stages of implementation, make sure you start with the monitoring mode (p=none) instead of full enforcement (p=reject). This will help you understand how your domain is being used without disrupting legitimate emails.
Analyze DMARC reports and move on to p=reject
Review DMARC reports to see who’s sending emails from your domain and fix any issues. Once you’re sure all genuine senders are verified, change your policy to p=reject to stop fake or unauthorized emails completely.
We understand that implementing DMARC for public sector domains can be tricky, especially when the stakes are so high. This is why our team of experts is here to help you do it seamlessly and efficiently. Contact us today to get started!







