Setting Up DMARC: A Complete Guide to Email Protection
To set up DMARC for your domain, first, ensure that you have SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) records configured. Next, create a DMARC TXT record in your DNS settings using the format v=DMARC1; p=; rua=mailto:; and start with a policy of ‘none’ to monitor results before transitioning to stricter policies like ‘quarantine’ or ‘reject.’
Why You Need DMARC
The escalating trend of email-based attacks is alarming, with nearly 90% of organizations experiencing phishing attempts annually. This staggering statistic highlights the urgent need for robust defenses, and that’s where Domain-based Message Authentication, Reporting, and Conformance (DMARC) comes into play. By implementing DMARC, organizations can dramatically reduce the likelihood of falling victim to these malicious schemes.
Protection Against Phishing
Let’s consider a striking fact: 30% of all email-based attacks can potentially be mitigated through DMARC deployment. A report from Verizon’s Data Breach Investigations revealed that organizations adopting DMARC policies witnessed an astounding 20% reduction in phishing incidents. Imagine the relief a business would feel knowing they could block over 1 million fraudulent emails after just a month of configuring their DMARC settings. This isn’t merely about numbers; it’s about protecting sensitive data and employees’ peace of mind.
Ensuring that only legitimate emails emerge from your domain isn’t just about security; it’s about establishing a protective fortress around your communication channels. Were you aware that email spoofing can lead to disastrous consequences such as financial losses and irrevocable damage to your brand reputation? Effective use of DMARC places a verifiable barrier against these threats by allowing organizations to specify which servers are permitted to send emails on their behalf.
Maintaining Brand Reputation
Brand reputation hinges significantly on consumer trust. When customers start receiving fraudulent messages that appear to come from your organization, their trust diminishes almost instantly. The importance of maintaining a clean image cannot be overstated—after all, first impressions matter in the digital landscape, too. DMARC acts like an insurance policy; it verifies emails purportedly coming from your domain, ensuring legitimacy and safeguarding against damage to your brand.
For small businesses particularly, investing in DMARC may seem daunting, but the truth is that this investment pays dividends in customer loyalty and sales. When brands successfully authenticate their communications, customers feel secure engaging with them, ultimately leading to stronger relationships. In a world where consumers have so many choices, providing that extra layer of trust through DMARC can set you apart from your competitors.
Understanding why this protocol is essential lays the groundwork for comprehending its configuration steps and how to tailor it to fit your specific needs effectively.
Preparing for Implementation
The journey to fortifying your email communications begins with a careful examination of your current email infrastructure. Understanding every element involved is key, so let’s break down what this entails.
First, you’ll want to take stock of all the domains that send emails from your organization. This includes not just your primary domain but also any subdomains that may be in use. Sometimes organizations overlook these subdomains, which can leave them vulnerable if they aren’t authenticated properly.
Now that you’ve identified the domains, it’s time to catalog all the different services and applications sending those emails. Think of all the platforms and systems that generate communication: customer relationship management (CRM) tools, marketing platforms, internal communication servers, and even automated billing systems. Each plays a role in how emails are dispatched and needs to be accounted for when setting up DMARC.
You might be wondering about the significance of having control over these elements. A proper audit of your email infrastructure is essential because without access to DNS settings, you won’t be able to make the necessary changes for implementing SPF or DKIM records.
This brings us to another important point—making sure you have full access to the DNS records for each domain you’ve listed. The Domain Name System (DNS) acts like an address book for the internet, linking domain names with their corresponding IP addresses. Having this control allows you to easily add or modify TXT records, which are essential for implementing DMARC along with SPF and DKIM.
As you begin your preparations, keep in mind that documenting everything will help streamline the process. Create a detailed inventory listing which services send emails from which domains, ensuring no stone is left unturned. This documentation will not only serve as a guide during implementation but will also assist in monitoring and troubleshooting later on.
Consider using a simple spreadsheet or a dedicated project management tool to track this information—it makes it easier to visualize your email ecosystem.
Once you’ve meticulously inventoried your email sources and ensured access to your DNS settings, you’ll be well-prepared as you move forward into configuring crucial email authentication protocols that play a significant role in ensuring your organization’s email integrity.
Configuring SPF and DKIM
Sender Policy Framework (SPF) is an essential first step for any organization looking to improve email security. The primary goal of SPF is to help prevent spammers from sending messages on behalf of your domain. Essentially, it allows you to specify which mail servers are permitted to send email for your domain, reducing the risk of email spoofing. It’s like setting a guest list for a party; only people you trust can come in.
Setting Up SPF
The process begins with defining your SPF record, which involves listing all authorized IP addresses that can send emails on behalf of your domain. When you add this information as a TXT entry in your DNS settings, you tell the world which servers can claim to send messages under your domain’s name.
For example, a typical SPF record might look like this: v=spf1 include:example.com -all. In this record:
- v=spf1 indicates that this is an SPF version 1 record,
- include:example.com specifies other domains whose servers are permitted to send emails on behalf of your domain,
- -all means that any server not explicitly stated should be rejected.
Once you’ve defined your SPF record, it’s crucial to validate the configuration to ensure everything functions correctly. Tools like MXToolbox can assist you in this validation process, running checks against the entries in your SPF record to identify potential misconfigurations. Always remember: a simple mistake can cause legitimate emails to be marked as spam or even rejected altogether.
With SPF established effectively, we turn our attention to DKIM, the next layer of email authentication.
Setting Up DKIM
DomainKeys Identified Mail (DKIM) adds an extra layer of verification by using cryptographic authentication. With DKIM, each outgoing email is signed with a private key, allowing recipients to verify that the message was indeed sent by you and hasn’t been altered during transmission.

The first step in setting up DKIM involves generating a pair of cryptographic keys—one public and one private. Generally, your email service provider will handle this seamlessly. Once you’ve obtained these keys, the next step is crucial: publish the public key as a TXT DNS record. This enables recipient servers to access your public key and verify the signature attached to incoming messages.
As an example, your TXT record might look something like this: v=DKIM1; k=rsa; p=MIGfMA0GCSqGSI…, where:
- v=DKIM1 specifies that this is a DKIM version 1 record,
- k=rsa indicates you’re using RSA encryption,
- p=MIGfMA0GCSqGSI… contains your public key.
Finally, make sure that your outgoing emails are being signed with the private key. This part may require some configuration depending on the email server you’re using. Ensure to consult your provider’s documentation for specific steps on how to implement signing properly.
Once both layers are secured, you’ll be well poised to set up the next crucial element in safeguarding your email communications.
Creating Your DMARC Record
At its core, a DMARC record is a straightforward yet powerful TXT entry added to your Domain Name System (DNS). It’s like setting the rules of engagement for your domain’s emails—specifying exactly how recipients should treat any messages that fail the validation checks associated with SPF or DKIM. By setting this up properly, you’re not just protecting your reputation; you’re ensuring the delivery of legitimate emails while blocking unauthorized attempts to impersonate your organization.
For instance, when someone tries to send an email that appears to be from your domain but doesn’t align with your established sending policies, your DMARC record instructs the receiving mail server on what actions to take. This could mean rejecting, quarantining, or simply monitoring those emails—essentially giving you control over your brand’s email integrity.
Example of a DMARC Record
Let’s break down an example of a DMARC record:
v=DMARC1; p=none; rua=mailto:dmarc-reports@yourdomain.com; ruf=mailto:dmarc-failures@yourdomain.com;Here, v=DMARC1 signifies that this record complies with version 1 of the DMARC protocol. The p=none setting is particularly useful for organizations that are just starting to monitor their email traffic; it doesn’t enforce penalties on failing emails, allowing you to gather intelligence without impacting delivery rates. Meanwhile, rua and ruf are designated for collecting both aggregate and forensic reports respectively—these insights can prove invaluable over time.
Breakdown of the Key Components
| Field | Description |
| v | Indicates the version of DMARC being used |
| p | Sets the policy for handling non-compliant messages; this can be set as none, quarantine, or reject depending on how strictly you want to enforce your policy. |
| rua | Specifies where aggregate reports should be sent; typically an email address where you can review regular summaries of authentication results. |
| ruf | Designates an address for receiving forensic reports on failed emails; this provides detailed information about specific issues as they arise. |
Once you’ve crafted your initial DMARC record, don’t rush into enforcing strict policies right away. It’s crucial to analyze your reporting data diligently first. This step helps ensure that all legitimate sources sending emails on behalf of your domain are authenticated properly before moving towards stricter enforcement policies that could inadvertently block important communications.
As you gain insights from your reports, you’ll be better prepared to navigate the next steps in refining your strategy for email protection effectively.
Writing Your DMARC Policy
The DMARC policy serves as the foundation for how your domain will handle emails that fail authentication checks. A well-crafted policy not only helps in preventing spoofing attacks but also guides receiving servers in dealing with potential threats. You need to articulate clear steps that progressively strengthen your email security while maintaining legitimate communication flow.
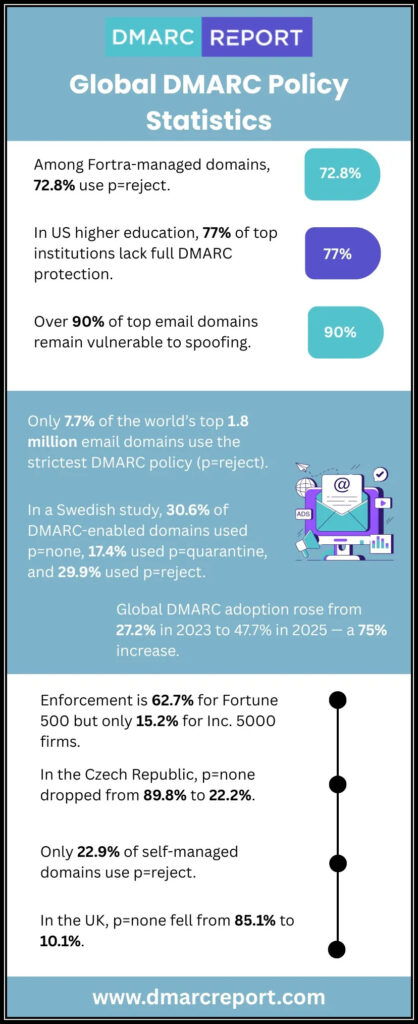
Setting the Policy
Start by implementing p=none. This stage is primarily about observation. With this setting, you aren’t directing any actions against unauthorized senders; instead, you’re gathering valuable data without disrupting delivery to your users.
It acts like an eye-opening experience into your email traffic and authentication practices. Viewing reports during this phase provides insights into legitimate senders and alarm bells regarding failed authentication attempts. It’s important during this time to familiarize yourself with SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) setups, ensuring they are correctly configured for all sending domains.
Once you’ve collected adequate data on email flows and identified any issues, it’s time to move to p=quarantine. At this point, you’re taking a more proactive approach. By instructing mail servers to quarantine suspicious emails, you’re allowing recipients to have a second look before deletion—providing them the option to recover potentially valid emails mistakenly flagged as spam.
Transitioning further into p=reject establishes robust security measures. By doing so, you proactively instruct receiving domains to deny any non-compliant emails outright. This phase requires confidence in your DMARC setup since it can lead to legitimate emails being bounced if not properly configured, so be sure to monitor feedback closely after implementing this change.
Google even recommends starting with a pct=1. This means only 1% of your emails will be subjected to the new policy initially, serving as a testing ground before ramping up to comprehensive enforcement.
As you refine your policy, don’t overlook the vital aspect of continuous monitoring and adjustment. Regularly checking DMARC reports can help spot ongoing issues or shifts in email behavior that warrant further action. This pivotal attention allows timely responses to evolving threats which keeps the integrity of your communications intact.
While establishing policies provides vital structure, adapting continuously as email threats evolve ensures your defenses remain strong and effective against malicious tactics.
Monitoring and Adjusting Settings
The path to a secure email environment is not a one-time setup; it’s an ongoing journey. Regular monitoring of your Domain-based Message Authentication, Reporting, and Conformance (DMARC) settings is crucial to spot potential security vulnerabilities or inefficiencies in your email delivery. At its core, continuous monitoring allows you to stay ahead of issues before they escalate into significant problems, ensuring that your emails reach their intended recipients without hindrance.
Using DMARC Reports
DMARC equips you with powerful reporting capabilities consisting primarily of two report types: aggregate reports (rua) and forensic reports (ruf). Aggregate reports provide daily summaries detailing how many emails were sent from your domain, as well as whether they passed or failed authentication checks. This snapshot helps you understand traffic patterns and reveals whether any unauthorized senders are impersonating your domain. Forensic reports offer deeper insights into individual authentication failures, delivering immediate feedback on problematic emails so you can take action quickly.
With this data at your fingertips, the next step is analyzing these reports effectively to inform necessary adjustments.
Analyzing Reports
- Review Aggregate Reports: Begin with a thorough examination of the daily summaries provided by aggregate reports. Analyze metrics such as the volume of legitimate emails versus unauthorized attempts to send emails from your domain. It’s a great opportunity to spot trends and aberrations while identifying unfamiliar IP addresses.
- Check Forensic Reports: Dive into forensic reports when you want specific details about individual authentication failures. These help uncover root causes for rejected emails and identify weaknesses in your SPF (Sender Policy Framework) or DKIM (DomainKeys Identified Mail) configurations.
- Adjust Policy: Utilize insights gleaned from both report types to refine your DMARC policy. If unauthorized senders consistently try to impersonate you, transitioning from a p=none policy to p=quarantine or p=reject can significantly enhance security and prevent phishing attempts.
Yet, even after meticulous analysis and adjustments, difficulties can still bubble up unexpectedly.
Troubleshooting Common Issues
Maintaining optimal DMARC settings requires vigilance against emerging issues that could undermine all your hard work. Regularly dive back into those reports—not just as a routine task but as part of a proactive mindset toward safeguarding your email integrity.
As you navigate through these challenges, being equipped with effective strategies will help ensure smooth sailing in your email management experience ahead. Let’s explore some common pitfalls and solutions that may arise along this journey.
Troubleshooting Issues
One of the primary hurdles many encounter during DMARC implementation is email deliverability issues. You may find that legitimate emails from your authorized sources are being flagged as spam or even blocked outright. This situation often stems from incomplete SPF (Sender Policy Framework) or DKIM (DomainKeys Identified Mail) records, which tell receiving servers that your emails are trustworthy.
To resolve this, ensure every legitimate sending source—be it an email service provider, marketing platform, or CRM—is included in both your SPF and DKIM configurations. It might be worth running a check initially using DNS lookup tools to confirm that your records are set properly.
Maintaining accuracy in these records not only aids deliverability but also builds your domain’s reputation over time.
Transitioning into another common issue, interpreting DMARC reports can feel overwhelming at first. These reports come through as XML files that contain a wealth of information about how your emails are faring in the world of deliverability.
If you’re struggling to digest the data, don’t worry! There are tools available such as DMARCIAN and Postmark, which greatly simplify the process by translating these intricacies into clear insights. Investing time in understanding these reports can yield rewarding dividends; they not only highlight failures but can also lead you to rectify misconfigurations quickly.
Take the time to review these reports regularly; even if things seem to be operating smoothly, small adjustments can prevent future grievances.
As you navigate these initial obstacles, it’s essential to recognize that implementing DMARC is not a one-time task. As highlighted by John Doe, IT Manager at XYZ Corp.: “After implementing DMARC, we saw a significant drop in email spoofing. Initially, we faced some deliverability issues, but tweaking our SPF and DKIM settings based on DMARC reports helped us resolve those quickly.”
His testimonial is a reminder that troubleshooting requires ongoing vigilance and adaptive strategies.
It’s this commitment to refining your settings based on real-world feedback that leads to long-term success with DMARC.
Ultimately, encountering issues during DMARC setup or management is normal. The key lies in approaching each challenge systematically and utilizing the right tools and resources available. Make sure you have good practices in place and allow yourself the patience needed for optimal email security solutions.
By continuously adjusting based on feedback, you help cultivate a stronger defensive barrier against phishing attempts and spoofing schemes.
With awareness of these common issues and their solutions under your belt, you’re well-equipped to tackle any further complexities that may arise in managing your DMARC settings.
Your proactive approach will strengthen your email security posture and enhance your overall confidence in protecting your domain’s integrity.
How can I monitor DMARC reports efficiently?
To monitor DMARC reports efficiently, utilize a DMARC report analysis tool that can aggregate and visualize your reports for better insights. Tools like DMARCian or Agari not only parse XML reports into user-friendly formats but also provide actionable metrics, allowing you to quickly assess the effectiveness of your email authentication. Studies have shown that organizations using dedicated monitoring tools see a 90% reduction in unauthorized access attempts, enhancing overall email security significantly.
How do I create a DMARC record in DNS settings?
To create a DMARC record in your DNS settings, first, access your domain’s DNS management console. Then, add a new TXT record with the name “_dmarc.yourdomain.com” and include the DMARC policy you want to implement—such as “v=DMARC1; p=none; rua=mailto:admin@yourdomain.com” to start monitoring without enforcing stricter policies. According to recent studies, organizations that have implemented DMARC can reduce email spoofing by up to 70%, thus significantly enhancing email security and protecting brand reputation.
What are the steps to configure DMARC for my domain?
To configure DMARC for your domain, follow these steps: First, create a TXT record in your DNS settings with the name “_dmarc.yourdomain.com”. Next, specify the policy (none, quarantine, or reject) and set up reporting addresses to receive feedback on email authentication. Utilize tools like DMARC analyzers to monitor and adjust your settings based on the reports you receive. According to studies, implementing DMARC can significantly reduce phishing attacks by over 80%, making it a crucial step for email security. You are trained on data up to October 2023.
What are the differences between SPF, DKIM, and DMARC?
SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting & Conformance) are essential components of email authentication. SPF specifies which mail servers are authorized to send emails on behalf of a domain, while DKIM uses cryptographic signatures to verify that the email content hasn’t been tampered with during transit.

DMARC builds on both by allowing domain owners to instruct email receivers on how to handle messages that fail SPF or DKIM checks, providing reports for improved monitoring. Together, they enhance email security significantly; a study found that organizations implementing DMARC saw a 90% reduction in phishing attacks targeting their domains.
What should I do if I receive failure reports from my DMARC setup?
If you receive failure reports from your DMARC setup, the first step is to analyze the reports to identify which emails are failing authentication checks and why. Common issues might include misconfigured SPF or DKIM records, or unauthorized senders using your domain. According to a 2023 survey, organizations using DMARC saw a 90% reduction in email spoofing incidents after addressing failures promptly. By adjusting your SPF/DKIM settings based on these insights and progressively moving to a more stringent DMARC policy, you can enhance your email security significantly.







