Major risks of sharing email accounts

While sharing email accounts is convenient, users often do not consider the cybersecurity and legal risks they pose. While your company might have convincing reasons to share email addresses, this practice should be avoided as much as possible.
If we go by definition, a shared email account is one that multiple people can access and use, usually within an organization or team. It’s mostly used to manage communication where multiple people of a group have to come along for operations, for example, in customer support, sales, or info-based queries. Because of the ease with which shared accounts offer centralized communication, it has become a common workplace practice.
If these accounts are not managed properly, the organization can be left vulnerable to various kinds of cyberattacks. If any malicious activity (for example, sending phishing emails) is done through the shared account, it is difficult to identify the responsible person because of the absence of individual logs. There are more such risks that we’ll discuss in this blog.

Why does email security matter?
Email is one of the primary sources of communication in most organizations. We share so many confidential details and files via emails that it’s also one of the most vulnerable assets. Email vulnerability isn’t just limited to data theft but also poses a threat of someone sending phishing emails on your behalf.
Businesses can’t afford to risk the confidentiality, integrity, and availability of their critical assets, prompting them to take email security seriously. That’s exactly why SPF, DKIM, and DMARC protocols have become the primary personnel of the email defense toolkit. Together, these three email authentication protocols help domain owners ensure that only authorized entities send emails on their behalf and that tampered emails don’t get delivered.

Why should you avoid sharing email accounts?
Shared email accounts can pose significant cybersecurity risks, especially when not properly managed. Here’s why:
1. Weak access control
Weak passwords are one of the common reasons for email break-ins. There are so many tools that allow hackers to crack easy passwords. If multiple people share an account, there are chances that the password is something very easy to guess. This is done so that everyone can remember it. While it’s convenient to use simple passwords, it takes hackers no time to crack them and break into the shared account.
Chances are that the same password is used across multiple shared accounts, increasing exposure to threats and breaches. To reduce this risk, it is always suggested that unique and strong passwords be used for every account. A strong password includes upper- and lower-case letters, numbers, and special characters.
2. Lack of accountability
If multiple people share one email account, keeping a log of who has done what is practically difficult. So, if there is a breach attempted by an insider and some sensitive data gets shared or a phishing email is sent, it’s very difficult to tell who it was. The situation gets all the worse when more than 3-4 people are sharing the account.
If we keep aside the cyber threat concerns, then it’s also a challenge to figure out who has responded or sent which email. This can cause problems in other aspects of a business, such as sales, customer support, media communication, etc.
Also, a lack of accountability isn’t about blaming people. If there is a security issue, it’s important that you know who needs more training so that only those users get the help they need— without frustrating those who already follow best practices. Accountability also does good for the workflow; if no one knows who’s supposed to reply to which emails, team members may waste time checking every message to make sure nothing gets missed.

3. Higher risk of phishing
When there are multiple users, chances are that not all of them will be equally aware of phishing red flags. While one cautious user might recognize a phishing attempt, another untrained person might click a malicious link or open an infected attachment.
Also, threat actors rely a lot on impersonation. With shared accounts, messages are usually not addressed to a specific person (like ‘Hi John’), making generic phishing all the more believable and successful. Team members are used to impersonal communication in these inboxes, so a fake email may not raise red flags.
Another thing that increases the risk of phishing is the frequent forwarding of emails. This is because shared email accounts are often used to forward emails internally. So, if a phishing or email slips through and gets forwarded to others, the risk will spread to other departments and sometimes even external contacts.
4. No support for MFA
You already know that multifactor authentication, or MFA, adds an extra layer of security to your password protection. It requires users to verify their identity using something more than a password— like a code sent to your phone, an app notification, biometrics, etc. This is one of the most effective ways to protect email accounts from unauthorized access.

However, MFA is not a feasible option with shared email accounts, and this stands as a serious cybersecurity risk.
MFA is designed for individual use. It sends the second step (like a code or app prompt) to a specific person’s device. But with shared accounts, who gets the code or notification, and who approves the login?
If only one team member receives the MFA prompt, others can’t log in without coordination. To avoid this, many teams turn off MFA entirely, which leaves the account vulnerable. With no MFA, you are only left with a password, and if that’s also weak, then any attacker can get in easily.
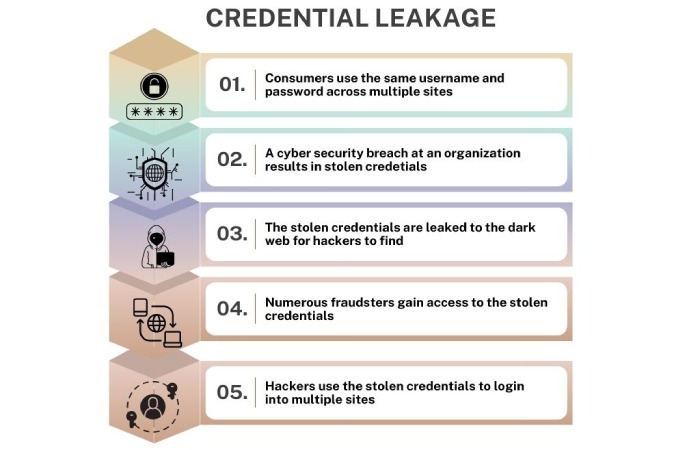
5. Credential leakage
To make sure every user of the shared account can access it, the password is often written down on sticky notes, saved in unencrypted documents like spreadsheets or text files, or sent through emails, Slack, or WhatsApp. This increases the possibility of the password being accidentally or intentionally stolen by ill-intended people.
Also, since the same password has to be used by multiple people, it rarely gets updated. As a result, hackers get more time to steal and exploit it.
And you know what’s more dangerous— one of the users left the company and still has access because nobody bothered to change the password. Over time, this creates a long, invisible list of people who might still be able to log in.
6. Data retention
If one user has deleted an email attachment for safety purposes, and some other user has already downloaded it on their device, then the data still exists. This can be dangerous when dealing with sensitive details and can even open gateways for phishing and BEC attacks.
Hackers will easily steal and encrypt data, refusing to delete it until they receive a ransom.

7. Non-compliance
Healthcare, legal, government, and other industries are required to abide by strict data protection and communication laws, including email security. Most data compliance policies require organizations to not share email accounts, regardless of purpose. This ensures the privacy and integrity of organizations, employees, and customers.
Therefore, violating these laws will only increase your legal, financial, reputational, and operational problems.
8. Complex systems
Whenever there is a security issue, it gets hard for the IT person to figure out who did what, which device was involved, and how the problem started. Also, some users might need full control of the account, and others don’t. What do you do in such situations? Unfortunately, you can’t set different access levels in a shared account, making it tough to manage safely.

9. Increased risk of social engineering
Social engineering means manipulating people into giving up confidential details or performing certain actions that compromise security. Now, with multiple people using an email account, the cybercriminal also gets multiple victims to trick. They can pick a seemingly easy target and convince them to click a malicious link or enter login credentials on a spoof site.
10. Access restriction
Depending on the responsibilities and hierarchy, users will need different levels of account access. With shared email accounts, you can’t set different levels of access control, allowing and exposing every user to every email activity.
With no role-based permissions, everyone can read, delete, or send emails— even those who shouldn’t. Even users who only need to read emails can access account settings, change passwords, or connect insecure third-party apps—opening doors for attackers.

Alternatives to shared email accounts
Here are some safe practices that can help you achieve the same goal as sharing email accounts–
- Using shared mailbox for teams. This method doesn’t require sharing passwords, and access is managed with user permissions.
- Set up rules to forward specific emails to another person or team.
- You can delegate access to someone else who can read/send emails on your behalf.
- Use helpdesk platforms like Zendesk, Freshdesk, and Front. These are especially useful for customer support teams as all emails to a shared address go into a ticketing system, and each user gets their own login to handle queries.
Protecting your email should be one of your top priorities. Get in touch with us to know how we can help with this.







