What is DNSSEC, and why do you need it to protect your domain?

When DNS was designed back in the 1980s, security was not even a thing of concern; all it was made to do was translate domain names like “yourcompany.com” to IP addresses so that the browser could locate and connect to the correct server.
But things have changed drastically since then. Now, the digital landscape is replete with cyber threats, which you can no longer dodge (no matter how hard you try). They attack vulnerabilities that often go unnoticed, even those within the core infrastructure of your domain— the DNS.
Attackers now exploit your DNS by intercepting or manipulating its responses. This technique is called DNS spoofing or cache poisoning. By forging information in your DNS, they redirect your users to a fraudulent website, designed to steal their information or cause serious damage.

To prevent this, it is important that you protect your DNS just as you secure your email infrastructure. The most effective way to do that is by ensuring your DNS responses are verified, not just trusted, and that’s exactly what DNSSEC, or Domain Name System Security Extensions, does.
Now, let’s understand what DNSSEC exactly is and how it protects your domain from attacks like DNS spoofing.
What is DNSSEC?
Attackers these days have become smarter and more strategic. That means instead of intercepting your data at the surface, like through phishing emails or compromised websites, they go deep into the very core of your digital identity.

DNS has now become one of the key points of vulnerability that attackers target. But with DNSSEC, you can patch this gap.
DNSSEC (Domain Name System Security Extensions) is a security protocol designed to protect the integrity of your DNS data by adding cryptographic signatures to the DNS records. So, when a user tries to access your website, their browser checks the DNS record to make sure it’s real and unchanged. This is done using a digital signature that proves the information came from your official DNS server and wasn’t tampered with by anyone else.
If the signature matches the one attached to your DNS record, the browser considers the website as authentic, but if the signatures don’t match, the browser blocks the connection, preventing the user from accessing the malicious website.

How does DNSSEC work?
The main role of DNSSEC is to ensure that the information that the browser receives from the DNS is authentic and unaltered. It does so by adding a digital signature to DNS data so that every response can be verified before it’s trusted.
What happens when you implement DNSSEC is that it creates a pair of cryptographic keys; one private and one public. The private key is used by your domain to digitally sign its DNS records, and the public key is shared so that anyone can verify those signatures.
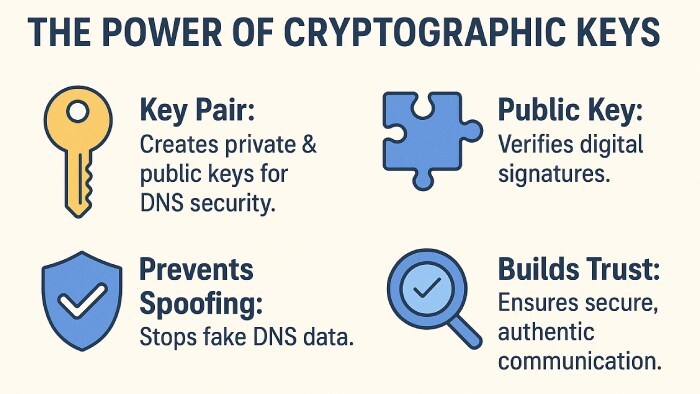
So, when someone tries to visit your website, their browser or the DNS resolver checks the DNS information and verifies the digital signature using the public key. If the signature matches, it confirms that the data originated from your legitimate DNS server and hasn’t been altered along the way. If it doesn’t match, the data is rejected because it might have been tampered with.
Essentially, DNSSEC builds a chain of trust across the entire DNS. This means, right from the root (the top of the DNS hierarchy), down to your specific domain, every layer verifies the one below it using digital signatures.
Since it builds this series of trust, the information it receives is properly validated.
Why you should care about implementing DNSSEC?
As you know, DNS is the foundation of your online presence, and if it is not secure, your entire digital identity will be at risk. Moreover, since DNS is not inherently secure, it becomes all the more vulnerable to being the prime target for attackers.

These attackers take advantage of this by manipulating the DNS records to redirect your users to fake websites that look identical to yours. And once your users land on the fraudulent website, they may unknowingly share sensitive information, such as passwords, financial details, or personal data, putting both them and your organization at risk. This is why protecting your DNS is now a non-negotiable.
With DNSSEC in place, you make sure that the information your domain sends out is verified and genuine. It ensures that when someone types your domain name, they’re always directed to your real website and not a fake one created by attackers. Apart from this, DNSSEC also helps strengthen your overall online security. It closes one of the biggest gaps in the internet’s infrastructure: the lack of verification in DNS responses. So, when your users’ browsers know that the DNS data isn’t forged or modified, they can safely direct them to your website. This not only protects your clients but also your brand from being misused in phishing or spoofing attacks.
As a domain owner, it is important that you not just focus on protecting your website and email infrastructure but also protect the very foundation of your digital presence. Because even if you have the most advanced measures, like security measures, like SSL certificates or firewalls, in place, your DNS can still be compromised. Protect your domain and enhance email security by implementing DMARC, DKIM, and SPF protocols to prevent spoofing, phishing, and unauthorized email use.
Final words
Your domain is only as secure as the system that connects users to it. Even if you have the most robust security measures for your website and emails, your efforts can fall short if your DNS is left unprotected.
DNSSEC protects that foundation. By verifying every DNS response and ensuring that your domain’s data hasn’t been altered, it keeps your users safe and your online identity trustworthy. The security protocol verifies every DNS response and ensures that your customers reach your authentic website instead of the one created by an attacker. If you want to secure your domain in and out, this is your sign to implement Domain Name System Security Extensions. Reach out to us today to protect your domain, brand, and customers from DNS-based attacks.







