Is DIY-ing DMARC Safe?
DIY DMARC isn’t considered safe due to the complexities involved and the requirement of technical expertise on board. It can impede the email flow, increase the number of false positives, and disrupt email-reliant operational flow. The person in charge should be well versed in the technicalities of SPF and DKIM, which include generating respective records, publishing them on the domains’ DNS, and regular monitoring through reports.
Not just this, but troubleshooting stands as a big challenge in the picture. It’s suggested to regularly run SPF, DKIM, and DMARC records through their respective checkers or lookup tools that highlight existing errors. Not being able to stay within the maximum lookup limit is one of the common and most troubling issues associated with SPF. This triggers your SPF record’s performance, which consequently hits DMARC processes.
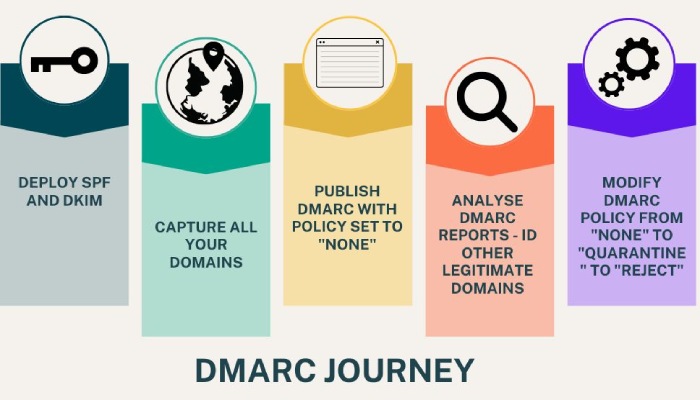
Why You Should Not DIY DMARC?
You need to use rua and ruf tags to receive aggregate and failure reports to ensure DMARC is working properly and understand your email-sending domain’s reputation in the eyes of recipients’ mail servers. Interpreting these reports is a challenge in the DIY DMARC scenario as these are presented in the XML format.
There are more complications linked to the idea of DIY DMARC. Let’s explore more!
Time-Consuming
The DIY DMARC process means the person in charge will be new to the complexities and technicalities and will take more time to comprehend and imply syntax, tags, policies, etc. On the other hand, an expert knows technical navigation, and their experience makes everything smooth and time-efficient.
Chances of Missing Out on Sending Sources
An inexperienced person can skip adding internal IP addresses and mail servers linked with your domain. This way, emails sent by genuine senders can get marked as spam or bounce back.
Not Compatible with Cloud-Based Emailing
Email authentication protocols are yet to be compatible with cloud-based email infrastructures. This is because of the frequent changing of IP addresses in that structure. Moreover, keeping a tab on the links between IP addresses and their corresponding service is extremely challenging.
Troubleshooting SPF and DKIM Challenges
SPF, for instance, can pose difficulties when managing complex email environments. Implementing and maintaining SPF records for organizations with multiple email servers or third-party email services can be intricate. SPF records need to be kept up to date, and accurately listing all authorized senders is crucial to prevent legitimate emails from being flagged as spam. Furthermore, the strict SPF mechanism can lead to email delivery issues when changes in an organization’s email infrastructure occur.
On the other hand, DKIM has its challenges, particularly in key management. Generating, distributing, and rotating cryptographic keys can be complex and require careful planning. If private keys are compromised or lost, it can jeopardize email security. Additionally, DKIM signatures can be affected by email forwarding, which may break the cryptographic validation, making it challenging to ensure message integrity in some cases.
Both SPF and DKIM also require careful alignment with the “From” header, which can be disrupted in scenarios like email forwarding, where the sender’s domain may differ from the “From” domain.

Possibility of Blocking Legitimate Sending Sources
Manual DMARC deployment can make you unintentionally block legitimate IP addresses and email servers. You may not even realize this until you monitor DMARC reports. In this way, it can take weeks to know the mistake and rectify the DMARC record.
The Final Take
While the idea of DIYing DMARC may sound tempting, as you’ll be saving money on outsourcing the task to an expert, it comes with its own fair amount of complications.
We suggest taking the ideal route for ideal protection against phishing and spoofing!







