Troubleshooting 3 Common DMARC Problems
Phishing and BEC attacks are on the rise, and the ever-evolving digital landscape has now emerged to a place where it’s very challenging to detect fraudulent email content by just reading them. It’s a matter of concern to know that 15% of employees respond to emails sent by threat actors, which leads to potential compromises and financial frauds, affecting a company’s name, market value, sales, etc.
DMARC ensures these fake emails don’t show up in targeted recipients’ inboxes, which leaves minimal possibility of them engaging with cyber actors.
DMARC adoption is increasing across the world, and 88% of the Fortune 500 companies have DMARC coverage. But are they fully covered against phishing and spoofing attacks if their DMARC records have problems?
This guide revolves around the 3 common DMARC problems and ways to fix them at the earliest to keep a distance from malicious entities.
Common DMARC Issues and Ways to Fix Them
Online tools for DMARC Record Check or lookup can be utilized, as they efficiently identify and highlight any existing issues leading to DMARC failures. The 3 most commonly found problematic elements are:
Issue #1: Misconfigured DMARC Records
As per a report, almost 1 million internet domains pose massive email security risks due to misconfigured security records, including DMARC records. There are several reasons triggering this issue.
Syntax Errors
Typos, missing components, or incorrect syntax in DMARC records can render them ineffective. A small error in the policy configuration may lead to unintended consequences.
Overly Restrictive DMARC Policy
The flow of communication can be disrupted if the DMARC policy set in the record doesn’t sit well with the nature and utility style of your email-sending domain. This way, even emails sent by genuine senders can get flagged as suspicious, affecting communication and business at various levels.
Lack of Subdomain Protection
Attackers are always on the hunt to track down unprotected and vulnerable domains and subdomains. Companies often overlook the part where they have to include their subdomains in the DMARC record. This mistake results in giving malicious actors the perfect breeding place.
What else would they want than to successfully send phishing emails to employees or clients of a reputed firm, that too, from their subdomain? The likelihood of getting responses gets exceptionally high.

Solutions to Fixing Misconfigured DMARC Records
- Conduct regular audits to ensure there are no typos and syntax issues.
- Make gradual policy transitions.
- Extend DMARC coverage to subdomains and dormant domains as well.
- Work closely with your email service providers to keep your DMARC record in alignment with their recommended configurations.
Issue #2: Incomplete SPF and DKIM Implementations
Improper SPF deployment, monitoring, and maintenance make the record invalid, which consequently causes issues in the DMARC authentication drill. Primary SPF issues are-
- Typos and syntax errors.
- Exceeding the DNS lookup limit of 10.
- Exceeding the void lookup limit of 2.
- Multiple SPF records corresponding to a single domain.
- Not including the sending sources of third-party vendors.
- Extra spaces and commas.
- Using +all or ?all mechanism.
Fixing them can sometimes require a resource with technical expertise. You can outsource the job to a credible company dealing in email authentication products. Here are some actions that help resolve SPF issues-
- Add or omit sending sources as per the changes in the email infrastructure.
- Include sending sources of third-party vendors who dispatch emails on your behalf.
- Use SPF lookup tools to understand existing configurational and syntactical errors.
- For SPF alignment, the “From” domain should also align with the domain specified in the “Return-Path” address.
DKIM works by adding signatures to emails, and the verification is done by matching public and private keys. Problems arise when these keys aren’t configured properly. Here’s how you can resolve the issue-
- Ensure the correct pair of keys are linked to your domain’s DKIM record.
- Regularly rotate DKIM keys.
- Ensure that the “From” domain in the email header matches the domain specified in the DKIM signature.
Issue #3: Lack of DMARC Monitoring and Reporting
DMARC monitoring involves careful analysis of RUA and RUF reports to assess the transmission of fraudulent and unidentified emails. The lack of this exercise causes the following problems-
Limited visibility into email authentication results
No DMARC monitoring means you practically don’t know how DMARC is working for your domain. You won’t know if and what percentage of messages are getting marked as spam or rejected.
Inability to identify authorized sending sources
You won’t be aware of the sources that are sending messages without your knowledge and consent. This takes away your power to stop phishing and spoofing attacks attempted in your company’s name.
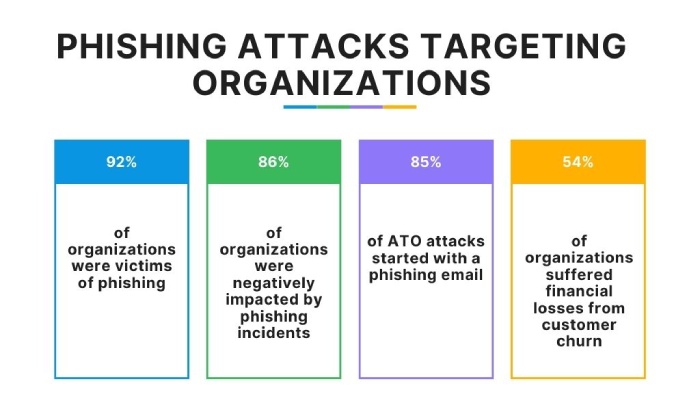
Difficulty in adjusting DMARC policies
Transitioning between DMARC policies without knowing the percentage of false positives and other factors can result in an increase in the instances of false positives or allow malicious emails to bypass security filters; neither of them would be in your favor. The decision to upgrade to a stricter policy won’t be informed and evaluated, which can pose email security threats to your domain.
Missed opportunities for improvement
Without monitoring, organizations miss opportunities to enhance their email authentication setup, address misconfigurations, and improve the overall security posture.
Addressing the Lack of DMARC Monitoring and Reporting
Enable DMARC reporting in your DMARC record by using ‘rua’ and ‘ruf’ tags and mentioning the email address where you want to receive these reports regularly and also right after a suspicious activity is observed.
This should be followed by carefully analyzing the reports to address issues like misconfigurations, unauthorized sources, or alignment issues.
We offer to work together with you to combat CEO frauds and phishing attacks by facilitating you with real-time geographical reports that offer in-depth forensics and give full visibility into attack patterns that InfoSec experts deploy to make your email infrastructure stronger.
What’s more?
We offer 24×7 support because we know cyber menaces don’t work in a 9 to 5 shift!
Click here and book a demo today. Our security consultant will email you within one business day to arrange your demo and address any email security inquiries you may have.






