Data Risk, Fortinet Trouble, CTO Resigns, AI Simulations

This is the third edition of the month, and here are the top 4 cyber mishaps that you must know about. Last week, Marks & Spencer’s CTO quit following a major cyber mishap. There was bad news for both Fortinet and ChatGPT Health. However, amidst this bleak landscape, experts have found a silver lining: cyberattack recreation and testing will help bolster safety mechanisms.
ChatGPT Health may not be healthy for your data!
While ChatGPT Health sounds like the much–needed, convenient, and accessible health advice, cybersecurity experts are not very positive about this LLM health chatbot. OpenAI claims it to be “a dedicated experience that securely brings your health information and ChatGPT’s intelligence together, to help you feel more informed, prepared, and confident navigating your health.”
Irrespective of all the tall claims, experts are not quite sure whether or not ChatGPT Health conversations will be end-to-end encrypted. There’s not much clarity around regulatory consumer protections.

Another cause of concern is how casually users are going to share highly sensitive healthcare details with ChatGPT Health. Meanwhile, ChatGPT Health is merely a product designed with the intention of consumer education. It does not even claim to be a diagnostic tool. The level of trust that users are going to show in ChatGPT Health itself calls for stringent regulations and control systems.
Experts believe that a user always loses some of the data they share with any third party. It is therefore highly significant that users remain cautious when sharing sensitive health information with ChatGPT Health.
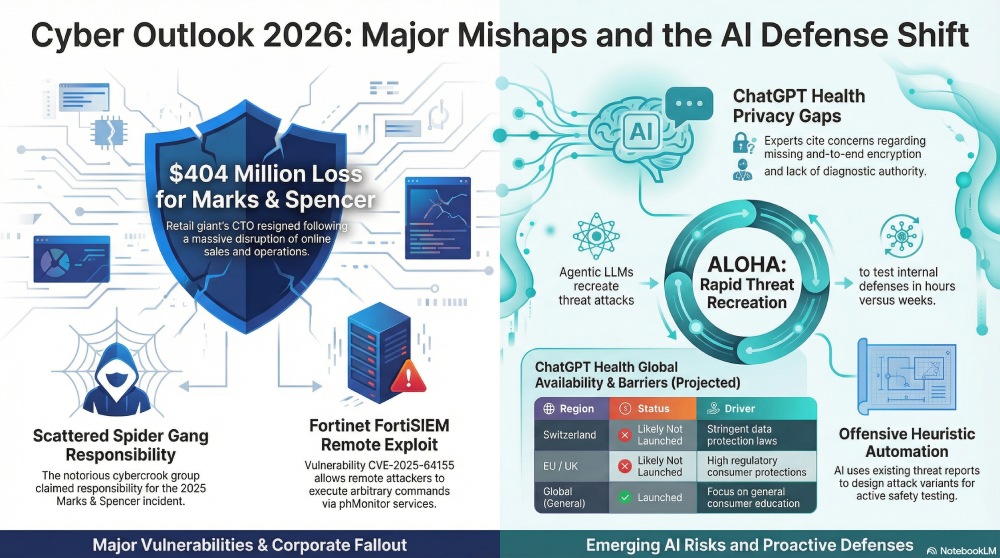
Giandana Gigena believes that the OpenAI health chatbot will not be launched in regions such as Switzerland, the European Economic Area, and the UK, as these regions have stringent data protection laws.

Bad news once again for Fortinet!
It’s 2026, and Fortinet customers are still struggling with data safety concerns. Threat actors have already started exploiting a newly found vulnerability in Fortinet’s FortiSIEM platform. Fortinet revealed a critical security flaw in FortiSIEM (CVE-2025-64155) on January 13. This vulnerability allows threat actors to execute arbitrary commands even from a remote location.
Soon after the revelation, experts realized that cybercriminals had already begun exploiting the vulnerability. The attackers have been using multiple IP addresses, some of which can be allegedly connected to Chinese service providers.
Horizon3, a security firm, discovered the vulnerability. Their proof of concept or PoC resembles the exploitation attempts observed by Defused. Horizon3 believes that the security issue is connected to FortiSIEM’s phMonitor service. The same service has previously been linked to FortiSIEM vulnerabilities like CVE-2023-34992 and CVE-2024-23108.
Fortinet has released a patch to mitigate the issue and urges customers to upgrade their systems at the earliest.
Even with DMARC, DKIM, and SPF, Fortinet customers must patch to ensure data safety.

Marks & Spencer CTO quits after a major cyber mishap
Marks & Spencer CTO Josie Smith resigned this Tuesday following a major cyber mishap less than a year ago. The cyber incident took place back in April 2025, whereby the threat actors managed to disrupt the entire online sales and operations systems for Marks & Spencer. The British clothing and footwear retailing giant lost a massive $404 million due to the unfortunate cyber incident. The notorious cybercrook gang, Scattered Spider, claimed responsibility for the same.
Smith had joined Marks & Spencer just 18 months ago. Before the CTO, it was Rachel Higham, the Chief Digital and Technology Officer, who decided to step down.
Meanwhile, Marks & Spencer is not openly connecting the departure of Rachel and Smith to the cyber mishap. They have issued public statements around their departure, wishing them luck for their future endeavors.
AI is helpful in cyberattack recreation and testing against potential threats!
While it is true that Artificial Intelligence has made it convenient for threat actors to penetrate deep into your systems, the same AI can be used smartly to prevent such cybercrooks from prying into your network.
ALOHA, or Agentic LLMs for Offensive Heuristic Automation, is capable of recreating threat attacks and designing multiple variants for active testing. ALOHA uses existing threat reports and detailed descriptions to carry out the entire process.
Replicating a recently discovered threat attack and testing the same against the existing internal defense mechanisms can significantly strengthen overall security setups.
Experts believe that ALOHA is just the beginning and that AI can be easily used by both advanced security teams and general organizations to combat threat attacks smartly. The researchers believe that ALOHA will help speed up the overall process from weeks to merely a couple of hours. The key idea is to test the latest cyberattacks as soon as possible and come up with effective testing so that organizations stay well-prepared against such attacks in the future.