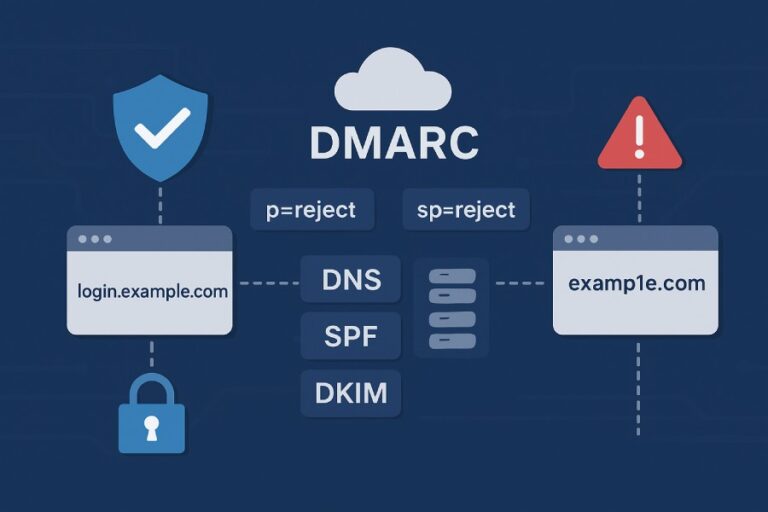
DMARC Report Analyzer Free: Your Tool for Email Security Insights
In a world where email communication is central to our personal and professional lives, ensuring that your messages reach their intended recipients safely is more crucial than ever. Enter DMARC (Domain-based Message Authentication, Reporting & Conformance), a powerful tool designed to help you protect your email domain from spoofing and phishing attacks. If you’ve ever felt overwhelmed by the technical jargon surrounding email security, you’re not alone! Many people find themselves lost in complicated reports that uncover issues with email delivery and authentication, making it hard to take action.
Fortunately, free DMARC report analyzers are here to make sense of that confusing data, putting easier-to-understand insights right at your fingertips. Let’s dive into how these tools can transform your approach to email safety and give you the clarity you need to defend against potential threats.
Yes, there are several free DMARC report analyzers available, such as Postmark and Valimail, which effectively transform raw DMARC reports into insightful data to help you manage your email security. These tools provide critical metrics on SPF/DKIM authentication rates and message actions, making it easier for you to evaluate and improve your email domain’s security posture.
Overview of DMARC Report Analyzer
A DMARC Report Analyzer is like a trusty guide in the often complex world of email security. At its core, it’s designed to interpret the aggregate and forensic reports generated by the DMARC protocol, ensuring domain owners can glean meaningful insights from what might otherwise feel like a mountain of technical jargon. This transformation makes it possible for users to understand essential metrics about email authentication results without wading through tedious XML files, which can be quite overwhelming.
Imagine you receive a pile of reports in a language you don’t speak; that’s how many users feel when they first encounter raw DMARC data. By parsing this information and presenting it in a more human-readable format, DMARC Report Analyzers empower users to take control of their email security strategies. They aggregate information by IP address and present critical details—like message volumes and SPF/DKIM authentication rates—ensuring you aren’t left guessing about your domain’s safety.
Key Insight: The reports generated from DMARC come from major mail receivers such as Gmail or Yahoo, offering invaluable data that can shape your email handling policies and procedures effectively.
For small businesses or individuals starting on their journey to stronger email security, free DMARC report analyzers are a godsend. Unlike some paid services that provide elaborate dashboards or premium features, these free tools still manage to deliver insightful analytics without the burden of additional costs. They often include capabilities such as alert notifications that promptly inform users about any suspicious activities or authentication failures.
Popular options like Postmark, Valimail, and DMARCIAN Free shine in this space by providing user-friendly interfaces that help demystify the security landscape surrounding your emails. Users have praised these analyzers not just for their effectiveness but also for the simplicity they bring into interpreting complex datasets, encouraging organizations to maintain robust security practices.
Utilizing an effective analysis tool sets the stage for understanding the specific features that enhance user experience and strengthen security measures in email management.
Key Features of Free Analyzers
One of the most compelling aspects of free DMARC report analyzers is their ability to provide insights that were once only available to those with deep technical expertise. By converting complex XML data into user-friendly visualizations, these tools enable anyone—from small business owners to email administrators—to grasp essential information about their email authentication status quickly.
For example, the aggregated data visualization feature simplifies the understanding of vast amounts of data, transforming what could be a cumbersome process into clear, easy-to-read charts and graphs. This feature not only saves time but also highlights trends in email deliverability that might otherwise go unnoticed.
Equally important is the IP address grouping capability. This feature categorizes email sources by their respective IP addresses, granting businesses a more structured overview of where their emails are coming from. With this information at hand, you can quickly identify unusual patterns that may require further investigation, such as unexpected spikes in email traffic from certain IPs.
By grouping sources, it becomes easier to pinpoint legitimate senders and identify potentially malicious actors trying to spoof your domain.
Imagine being able to see which of your friends are borrowing your favorite jacket (or causing trouble) every time they show up unexpectedly—this is like giving your email security that much-needed neighborhood watch!
Another critical feature is the authentication rates analysis. This component focuses on both SPF and DKIM verification processes, showing pass/fail rates. Understanding these rates allows you to evaluate whether legitimate emails are being delivered successfully or if there are authentication issues that need addressing. When authentication fails, it can lead to important emails ending up in spam folders—a dreaded fate for any outreach effort.
Now, let’s talk about the convenience brought by automated reports. These reports serve as timely summaries sent to your inbox regularly. Rather than having to log into an analyzer interface constantly, you can get insights delivered directly to you at intervals you select—be it daily, weekly, or monthly. Having this continual flow of information keeps you updated without interrupting your daily routine.
However, one could argue that relying solely on automated solutions might lead to complacency. While reports help illuminate trends in real time, it’s important to stay proactive and not let automated alerts be your only source of vigilance.

Finally, and perhaps most importantly for many users, is the email spoofing detection feature. This tool actively monitors and flags unauthorized email sources—a vital capability in today’s landscape saturated with phishing attacks and impersonation attempts.
By identifying these threats early on, businesses can take swift actions to secure their domains and protect their reputation.
Together, these features empower users with actionable insights and enhance clarity around email practices. As we explore the next phase of protecting your digital communications, it’s crucial to understand how each of these elements contribute to building a robust defense system.
Enhancing Email Security
The primary goal of using DMARC report analyzers is to enhance overall email security, acting as a shield against potential threats and unauthorized access. With cyberattacks on the rise—phishing attempts increased by 65% last year according to the Anti-Phishing Working Group—it’s clear that implementing DMARC is not just beneficial; it has become imperative for businesses aiming to protect their reputations and sensitive data from malicious actors.
By leveraging DMARC, organizations can effectively reduce the risk of falling victim to phishing attacks and similar threats. Consider that DMARC implementation can mitigate 99% of email fraud attempts when applied correctly. That’s an astonishing figure that underscores the importance of proactive measures in safeguarding your domain.
Regularly analyzing DMARC reports enables domain owners to quickly identify any unauthorized email activities. For example, if a report shows unusual activity from an unexpected IP address attempting to send emails under your domain name, it’s a red flag. With these insights, you can adjust your email policies accordingly, blocking suspicious addresses or tightening authentication requirements, thereby creating a safer email environment for you and your stakeholders.
Furthermore, regularly updating SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) records in line with findings from your DMARC reports strengthens your email security even more. Keeping these records current ensures you’re only allowing legitimate sources to send emails on behalf of your domain, minimizing the chances of unauthorized parties exploiting it.
It’s not just about setting up DMARC; it’s about continuous improvement and vigilance. Small adjustments based on recent trends or changes in your organization’s email practices can significantly enhance security.
The use of DMARC report analyzers empowers businesses to be proactive rather than reactive regarding email security. By maintaining consistent monitoring, you transform what might feel like an overwhelming task into a manageable part of your ongoing cybersecurity strategy. These proactive steps not only protect your business but also foster trust among clients and recipients who rely on the integrity of communications coming from your domain.
As we move forward, let’s explore the next critical elements involved in establishing effective safeguards and policies that ensure robust protection against email threats.

Implementing DMARC Policies
Setting up DMARC policies is essential as they form the backbone of your organization’s email security strategy. As you embark on the multi-step journey to implement these policies, it’s important to appreciate that each phase is interconnected and builds upon one another. Let’s break down this process into its fundamental parts.
Step-by-Step Guide
Step 1: Create SPF and DKIM Records
The first step in implementing DMARC starts with SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) records, your foundational email authentication methods. Think of SPF as a guest list, specifying which mail servers are permitted to send emails on behalf of your domain. This helps thwart spoofers who might impersonate your domain for malicious purposes. Meanwhile, DKIM adds a digital signature to your emails, ensuring that the content hasn’t been tampered with during transmission. To ensure these records are properly configured, tools like MXToolbox can assist you in validating them seamlessly.
Step 2: Define DMARC Policy
Now that you have SPF and DKIM in place, it’s time to establish a DMARC record. You must decide on the policy level—’none’, ‘quarantine’, or ‘reject’. A ‘none’ policy allows you to monitor without enforcing any action; this is useful for gathering data without affecting delivery. Once you’ve analyzed reports for some time, shifting to ‘quarantine’ directs suspicious emails into a spam folder while ‘reject’ completely blocks unauthorized attempts from reaching recipients at all. Choosing the right starting point is critical because it dictates how aggressively you’ll protect your domain against potential threats.
Step 3: Configure DMARC Report Address
Having defined your policy, the next step involves configuring where you want to receive your DMARC reports. These reports provide a wealth of information about email traffic associated with your domain—including metrics on SPF and DKIM validation results and actions taken by receiving servers. Specifying an email address ensures you get timely updates about how well your policies are working. This transparency establishes a feedback loop crucial for fine-tuning email security efforts.

Step 4: Monitor and Adjust
Finally, regularly reviewing incoming DMARC reports and adjusting your policies accordingly is vital. You might find trends in unauthorized login attempts or unusual spikes in email volume that indicate potential abuse of your domain. Ongoing assessment allows you to stay one step ahead in securing your communication channels. After all, implementing robust policies is just the beginning; being proactive about monitoring and adjustments determines how well those measures hold up against evolving threats.
Each step in this process builds upon the last, creating a strong framework for safeguarding your domain against malicious attacks while enhancing credibility among recipients. Transitioning now to essential tools will help simplify this entire process for effective management.
How to Choose the Right Analyzer
The process of selecting a DMARC analyzer requires careful consideration. You’ve implemented DMARC policies, and now it’s time to ensure you have a reliable tool that makes interpreting reports easy.
First and foremost, ease of use is crucial. You want an intuitive interface that doesn’t require hours of training or technical know-how to navigate. Imagine spending precious time fumbling through complicated dashboards when all you need is clarity on your email authentication efforts. Tools that prioritize user-friendly designs allow you to focus on making informed choices rather than getting stuck in the software.
Next, let’s talk about features and functions. A robust analyzer needs to provide essential functionalities like data visualization that transforms complex XML reports into digestible graphs and charts. This visual representation can help reveal trends and patterns in authentication rates, empowering you to make swift decisions based on real-time insights. Assess whether key features such as alert systems for unauthorized access attempts or specific metrics for poorly performing email domains are integrated into the package.
When evaluating potential DMARC analyzers, ask yourself: “Does this tool enhance my understanding of email performance?”
Customer support is another piece of the puzzle. Even if you select the most user-friendly platform, there may come a time when you need assistance—especially with free tools where support might be limited. Explore what options are available; some platforms offer extensive documentation, tutorials, or even direct customer service contact. It’s beneficial to have a safety net when unexpected issues arise.

Finally, but equally important, is data security. In an era where data breaches are alarmingly common, your chosen analyzer should adhere to stringent data privacy standards to protect sensitive information. Check for encryption protocols and compliance with regulations such as GDPR or CCPA. This emphasis on security will not only safeguard your email data but also build trust with clients and customers who expect their information to be treated with respect.
Evaluating these factors carefully ensures you invest in a DMARC analyzer that is effective and tailored to your unique business requirements. By prioritizing ease of use, essential features, dependable support, and high-security standards, you’re setting the stage for a fortified email ecosystem that significantly reduces spoofing risks and enhances overall communication credibility.
With these considerations in mind, we can now turn our attention toward how these tools translate into practical advantages for businesses looking to strengthen their email security practices.
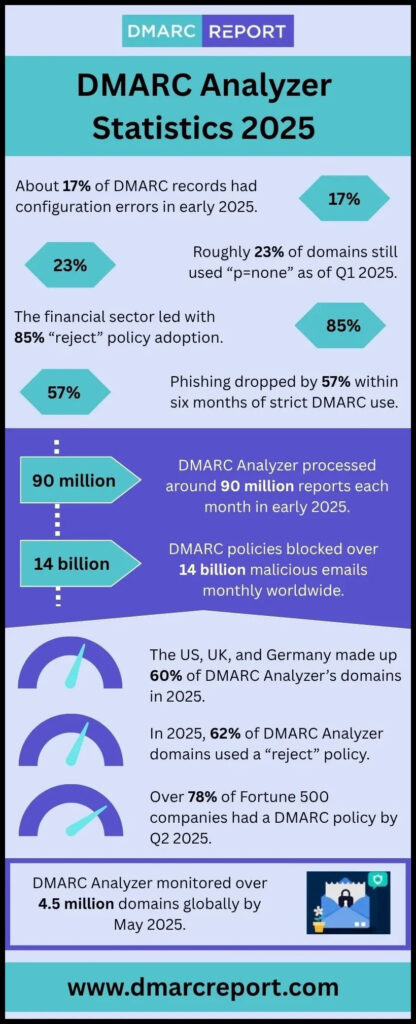
Real-World Benefits and Use Cases
Implementing DMARC policies combined with effective report analyzers can dramatically transform an organization’s email security landscape. Some companies have experienced immediate enhancements in their operations, showcasing just how essential these tools are.
Let’s explore a few compelling scenarios demonstrating the potential of DMARC and its implementation through real-life applications.
Consider a mid-sized company that was constantly grappling with phishing attacks. For this organization, every attack jeopardized their data and eroded customer trust. After adopting DMARC policies and incorporating a free report analyzer to monitor their email activities, they saw impressive results.
First, they improved their detection capabilities. The analyzer allowed them to identify multiple unauthorized sources attempting to send emails on their behalf, effectively shining a light on previously hidden threats. Next came enhanced policies: the company adjusted its DMARC policy to ‘reject’, preventing spoofed emails from ever reaching customers’ inboxes. As weeks passed, the visibility of their efforts paid off—the number of phishing incidents fell significantly, which in turn restored their customers’ faith in the company’s commitment to protecting their data.
“Switching to DMARC and utilizing a report analyzer has fundamentally changed how we manage email security,” shares John D., an IT manager at a tech firm. His testimonial underscores that success isn’t merely measured in reduced attacks; rather, it’s reflected in renewed confidence from clients and stakeholders.

This proactive stance enhances not just email security but strengthens the entire organizational ethos around safeguarding sensitive information.
Additionally, organizations using DMARC report analyzers gain valuable insights into their email authentication processes. These tools provide businesses of all sizes with comprehensive analytical features that highlight potential vulnerabilities within their systems. They offer tailored recommendations for adjusting SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) settings based on unique needs and environments, thus creating a seamless integration of best practices within existing protocols.
Illuminating Data Insights
| Feature | Description |
| User-Friendly Interfaces | Intuitive dashboards simplify complex data sets for easy interpretation. |
| Comprehensive Reporting | Translates intricate XML reports into digestible formats for swift action. |
| Real-Time Threat Intelligence | Alerts about potential vulnerabilities for proactive responses. |
Ultimately, leveraging DMARC report analyzers does more than fortify against phishing—it cultivates an enhanced corporate culture that prioritizes cybersecurity awareness and response across the board.
In adopting DMARC policies accompanied by capable report analyzers, organizations boost overall security frameworks while promoting compliance and proactive engagement in safeguarding stakeholder interests. In today’s digital landscape where cybersecurity threats are increasingly sophisticated, making this investment isn’t just wise; it’s vital for survival.