Understanding Kimsuky’s Latest Phishing Tactics: Exploiting DMARC “None” Policies

News Flash: The infamous North Korean group of hackers — Kimsuky strikes back!
Kimsuky is not a new name in the cybersecurity circle, as it is well known for pulling off sophisticated email-based attacks and leveraging social engineering tactics. But this time, they have changed their approach and shifted their focus towards organizations that have DMARC (Domain-based Message Authentication, Reporting, and Conformance) policies set to “none.”
You might think of this as a harmless setting or a minor oversight in security strategy, but the way it is capitalized by the attackers shows that this critical loophole is not trivial and can jeopardize your organization’s integrity.
Looking at the severity of the attacks caused by Kimsuky by targeting a seemingly inconsequential vulnerability, the Federal Bureau of Investigation (FBI) and the National Security Agency (NSA) issued a joint advisory on May 2, 2024. The advisory stressed the far-reaching impact of Kimsuky’s targeted spear-phishing campaigns and urged organizations to reassess their email security protocols, particularly DMARC policies.
Considering that the advisory came from two of the most important national security bodies in the world, the gravity of the situation certainly cannot be neglected. Let us dig deeper into this and learn more about the latest tactics of the North Korean cyberattacker group.
Why You Should Be Wary of Kimsuky?
Kimsuky is a group of hackers from North Korea that is known for carrying out some of the most serious cyber attacks targeting organizations in South Korea, Russia, the US, and Europe. Since the group has been around, causing significant damage, for more than a decade now, they have mastered the art of high-profile attacks.
Some of the most notable attacks so far include:
- In 2015, they managed to steal important information from a nuclear power company in South Korea.
- In September 2020, attackers from the Kimsuky group attempted to hack 11 officials of the UN Security Council.
- According to a lawmaker from the People Power Party, in May 2021, Kimsuky was detected within the internal networks of the Korea Atomic Energy Research Institute.
With victims spanning all across the world and a history of sophisticated attacks, it is safe to say that Kimsuky is no less than a global threat.
What Goes Behind the Kimsuky Phishing Attacks?
What ties all of the above-mentioned attacks together is the strategy employed behind them. Let us look at what makes these attacks so grave and hard to evade.
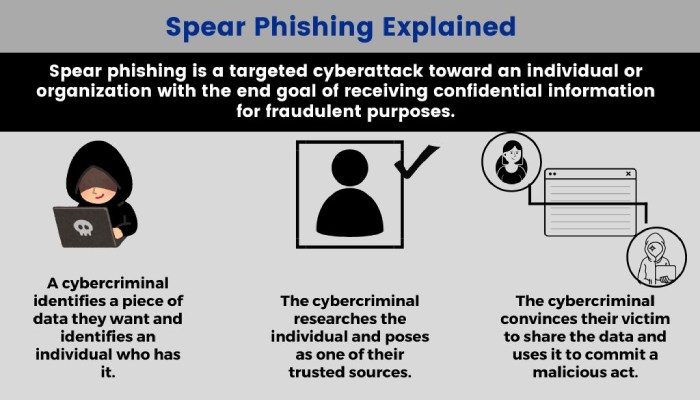
Kimsuky usually tricks people with emails that look like they are from legitimate government agencies or other trustworthy groups. They set up fake websites and send emails that look real to trick people into giving away private information like passwords.
Most importantly, they don’t just send one email but several emails over a period of time with an aim to gradually build trust. Once the unsuspecting victim believes they are engaging with a legitimate source, Kimsuky plays its master stroke, that is, sending the final email that contains an attachment or link to malicious software.
What are the 2024 Kimsuky Phishing Attacks All About?
As we mentioned earlier, Kimsuky’s recent phishing attacks saw a strategic shift in its approach. In the 2024 wave, the group further refined its techniques to exploit specific vulnerabilities in organizational email systems, particularly those with inadequate DMARC policies.

Kimsuky targeted organizations with the DMARC policy set to “none.” This lenient or non-existent DMARC setting gave them the way to execute their nefarious plans with little to no resistance. When set to “none,” the policy does not enforce any action on emails that fail authentication checks, meaning fraudulent emails can reach their intended targets without being blocked or flagged. This passive approach works well when you have to simply monitor your emails and check for authentication failures, but it takes no action against actual threats. Hence, a loophole like this opens the floodgate for phishing attacks.
How Can You Protect Against Kimsuky Phishing Attacks that Target Weak DMARC Policies?
To safeguard organizations from the wrath of Kimsuky attacks, the FBI has issued a list of preventive measures. Let us take a look at them:
Be Strategic When Advancing DMARC Policies
To ensure comprehensive protection against spoofing or phishing attacks, it is important that you upgrade and actively manage your DMARC settings. But while doing this, make sure that you do not jump the gun to implement the “reject” policy or, even worse, stay stagnant at “none.” By gradually transitioning from “none” to “quarantine” and ultimately to “reject,” you can seamlessly fine-tune your organization’s email security without disrupting legitimate communication.
Do not Ignore the Red Flags in Emails
While you might not be able to spot a malicious email at first glance, if you look closely, you will notice some giveaway signs of a phishing email that you should not ignore. These red flags are fairly common but often go unnoticed, like grammatical errors, awkward sentence phrasing, emails with malicious links or attachments, etc.
Another major red flag is the origin of the email. Phishing emails often come from spoofed domains that include misspellings or incorrect domain names that look similar to verified ones at a quick glance.
Wrapping Up
If you think attackers will not reach your organization, you will be making a grave mistake! The truth is, no organization, big or small, is invincible and can escape the clutches of such attacks. But by following a robust approach, you can significantly reduce your chances of coming under the radar of vile groups like Kimsuky.
A good starting and non-negotiable point is the strategic implementation of DMARC policies, moving from a “none” to more secure configurations such as “quarantine” or “reject.” Rest assured, this adjustment alone can dramatically decrease the likelihood of phishing emails reaching your mailboxes.
Need help enforcing DMARC policies for your domain? DMARCReport is here to your rescue!
Get in touch with us or book a demo with DMARCReport to secure your email channels effectively and protect your organization from the sophisticated threats posed by groups like Kimsuky.







