Reasons Why You Aren’t Receiving DMARC XML Reports

Once you have created a DMARC record, the job is not over; the real work of monitoring begins after that. Domain owners or administrators have to assess XML reports to understand if someone is sending unauthorized emails from your domain.
But what if you don’t receive these reports in the first place?
You won’t get insights into your domain’s email activities and will fail to leverage the primary benefits of implying email authentication protocols.
To receive XML reports, specify an email address in the DMARC record where DMARC aggregate reports should be sent. Ensure that your email server is capable of processing and storing these reports. Sometimes, you might not receive these reports due to one or more of these issues-
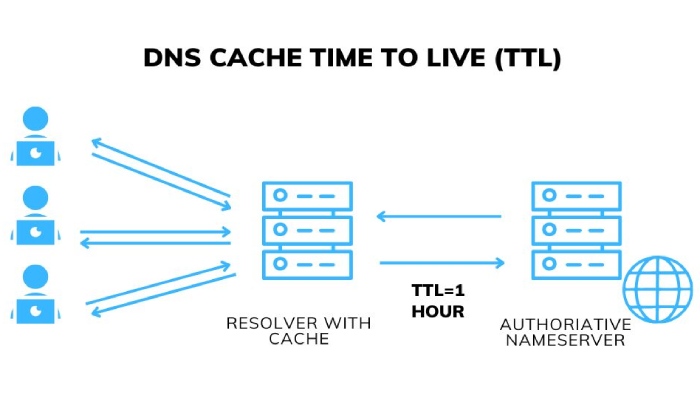
DNS Propagation Delays
It may take up to 72 hours for changes to propagate across the internet. The delay occurs because DNS information is distributed across a network of DNS servers, and these servers cache information for a certain period (time-to-live or TTL). During this TTL period, subsequent queries for the same information retrieve the cached data rather than fetching the updated information from the authoritative DNS server.
So, allow some time for DNS to reflect these changes and start receiving reports.
An Erroneous DMARC Record
A DMARC record with one or more of these errors becomes invalid, and no authentication takes place; thus, you don’t receive any XML reports:
Syntax Errors
Ensure that the record is written according to the correct DMARC syntax, using semicolons to separate components and specifying valid values for each parameter.
Missing ‘v’ Tag
A valid DMARC record starts with the ‘v=’ tag. It specifies the DMARC version. Any record not beginning with this is erroneous and does not perform authentication.
Incorrect Policy Action
The “p” tag specifies the DMARC policy action, such as “none,” “quarantine,” or “reject.” Choosing incorrect policies causes issues in placing illegitimate emails in the right categories.
Existence of Multiple DMARC Records
The presence of multiple DMARC policies corresponding to a domain confuses recipients’ servers and prompts unpredictable results.
No Failed Authentications
Recipients’ servers send XML reports to the email address provided for reporting when any message fails the authentication checks. So, if you are not receiving XML reports, then there’s a possibility that all the outgoing emails passed DMARC checks.
Ensure that there is sufficient email traffic for authentication failures to trigger report generation.

Incorrect Forwarding Settings
Email forwarding settings are complicated to deal with, and their incorrectness causes problems with forwarded email messages. So, it’s vital that you carefully tailor these DMARC settings to your organization’s forwarding practices, ensuring a smooth implementation while monitoring reports to promptly identify and rectify any issues arising from forwarded emails.
Low Volume Domains
Some domains are set to receive only a small prespecified number (usually less than 50) of emails in a day. So, find out if your domain has any such restrictions and have it fixed so you can start receiving XML reports for failed emails.
Receiver Policy
Some email receivers may not send DMARC reports, or they may have a delay in report generation. This is beyond your control, but you can review the DMARC aggregate report’s “rua” (reporting URI for aggregate data) field to see which email providers are sending reports.
Firewall or Filtering Rules
Firewalls and other email filtering rules sometimes don’t place XML reports in the inboxes. So, to get rid of this issue, you need to ensure that all the necessary ports are open for email traffic.
Why do we Assist DMARC Administrators in starting to receive DMARC Reports?
DMARC reports include details about emails that were sent from your domain but didn’t pass the DMARC filters at recipients’ ends, thus either getting placed in the spam folders or bouncing back. Analyzing and categorizing these failed emails helps you note anomalies and patterns that could trace you back to the culprit. You can take timely action by blocking illegitimate sending sources.
Also, sometimes, you miss adding a genuine sending source to your domain’s SPF record, prompting failed authentication for legitimate users as well. So, receiving and monitoring XML reports also helps you keep your DNS records updated.
We at DMARCReport do this on your behalf; you no longer have to manage complicated and frequent XML reports. We offer the best deals for MSPs with features like white labeling, easy reselling, scaling, and high performance.
As a business owner, now you don’t have to pay separately for hundreds and thousands of domains. Contact us to know the rest of the information.






