The Impact of Email Forwarding on SPF, DKIM, and DMARC
So you have your email authenticated with SPF, DKIM, and DMARC, yet your DMARC report shows discrepancies in the alignment? Chances are that your emails were being passed through an intermediary mail server before they were delivered. This is a classic case of email forwarding.
But then why implement email forwarding if it can compromise your email security, you ask? The thing is, at times, emails are automatically forwarded, and other times, it can happen through mailing lists such as Google Groups. So, when the forwarded email lands in the receiver’s inbox, it raises a few eyebrows while jeopardizing your email authentication infrastructure.
Let us take a look at how email forwarding can affect your SPF, DKIM, and DMARC implementation!
How Does Email Forwarding Affect SPF?
You might already know that SPF or Sender Policy Framework is deployed to specify the server and networks that allow the Return-Path to send an email on behalf of the domain owner, but what happens when the Return-Path domain is modified?
Let’s break it down for you! So, when you send an email to the recipient who wasn’t supposed to receive the email in the first place, you become liable for the bounces and other delivery issues that the recipient might have faced and will have to re-write the Return-Path to be able to use your own domain. But here’s the catch!
The problem arises when the forwarding server attempts to use the same Return-Path address as the original sender’s domain. Since this mail appears to come from the source identified in the SPF, it leads to SPF authentication failures.
How Does Email Forwarding Affect DKIM?
Since DKIM, DomainKeys Identified Mail is essentially a content-based authentication protocol that relies on cryptographic signatures to check the legitimacy of the incoming emails, forwarded emails are spared of any deliverability or legitimacy issues, provided that content and certain mail headers remain unchanged. Before you take a sigh of relief, let’s consider a worst-case scenario wherein the message was altered on its way to the receiver, especially when sent through mailing lists.
Many mailing lists add additional information, footers, or details about the list, and this can interfere with DKIM validation, causing security and reliability issues in email conversations.

How Does Email Forwarding Affect DMARC?
There are two ways that an email can be forwarded; one of them is manual, which has no effect on email authentication, but the second way— when the emails are automatically forwarded is when things become slightly complex and challenging, especially if there is no record of the intermediary sending source in the SPF.
Now that we have already established that SPF, being a path-based authentication protocol, is sensitive to email forwarding, especially if the sending source relies solely on SPF for validation, we hate to break it to you, but your forwarded emails may be deemed illegitimate during DMARC authentication.
Furthermore, in an exceptional case wherein the DKIM falls short in the face of email forwarding, that is, both SPF and DKIM fail, DMARC also fails in a domino effect,
As DMARC relies on the successful implementation of either SPF or DKIM to be authenticated, this should come as no surprise to you! But the pertinent question is, what is it that you can do to ensure comprehensive DMARC compliance and prevent opening a can of worms, which, in this case, would be deliverability issues and the risk of grave cyberattacks?
How Can You Safeguard Your Email Communication with Forwarded Emails?
Navigating the complex web of email authentication protocols, especially when it is riddled with email forwarding, is no easy feat! While there is no magic fix, following certain strategies can help ease the challenges and reinforce the authenticity of your emails. Let us take a look at them!
DKIM Signature to the Rescue
As we have already established that SPF is less resilient to email forwarding, ensuring all your emails are DKIM signed using your domain can help you wade the potential risks that come with forwarding. Following this approach not only helps eliminate all challenges but also increases your odds of getting a DMARC pass, especially if the forwarding process does not tamper with your messages.
Implement Authenticated Received Chain (ARC)
When it comes to tackling the complexities of email forwarding vis-a-vis cybersecurity, the Authenticated Received Chain (ARC) emerges as a champion that lets intermediary hosts keep a record of authentication checks. ARC allows the Authentication-Results header to be passed to the next “hop” in the email’s delivery trajectory.
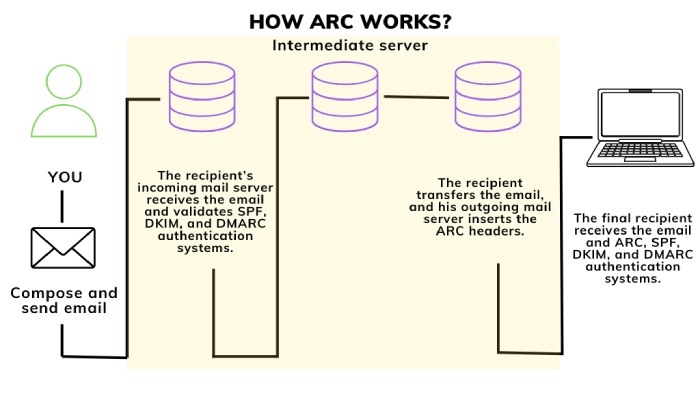
So when the recipient receives the forwarded email that has failed DMARC, the server refers to the ARC to validate the email again or, more like, give it the benefit of the doubt to cross-check if the mail was authenticated before the intermediary server stepped in and forwarded further.
Rewrite The From Header of the Mailing Lists
Since mailing lists are slippery slopes in the context of email authentication, they alter the content of the email. To address this and prevent DMARC failure, you can ask the mailing list administrator to configure the list’s address as the visible From header instead of the original poster’s domain.
Employ “p=quarantine”
Veering away from the conventional understanding, setting your DMARC policy to something as tight as “p=quarantine” can ensure that DMARC failures won’t result in failed deliveries. While this might result in some of the emails landing in the recipient’s spam folder, if you think about it, isn’t it better than them not being delivered at all?
The tug-of-war between email forwarding and DMARC implementation is, undeniably, an ongoing challenge. The root cause of this tension is the inherent nature of email forwarding that passes emails through intermediary servers before they get delivered, potentially leading to issues in SPF, DKIM, and DMARC alignment. At DMARCReport, our team of experts is here to help you facilitate seamless communication while maintaining a sound email infrastructure with DMARC. For details about our services, book a demo today!







