Secure Passkey Protection, Dismantling Lighthouse Phishing, Manufacturers Need Protection
Hello people!
It is the third week of November, and as promised, we are back again with our latest edition of cyber news. Meanwhile, we hope you have been able to safeguard your data from the cybercrooks. Even though they are getting sophisticated with every attack, it is up to us to bolster our data and networks. And that is possible when you stay fully prepared with cyber knowledge and awareness to combat the malicious activities of threat actors.
SPF, DKIM, and DMARC work together to strengthen email security by preventing spoofing and ensuring messages come from legitimate senders.
This week, we will discuss the latest trend of switching to passkeys to protect crucial business data. Next, our focus will be on the Lighthouse phishing-as-a-service operations. Lastly, we will focus on why manufacturers are prone to ransomware attacks and how to overcome the threat.
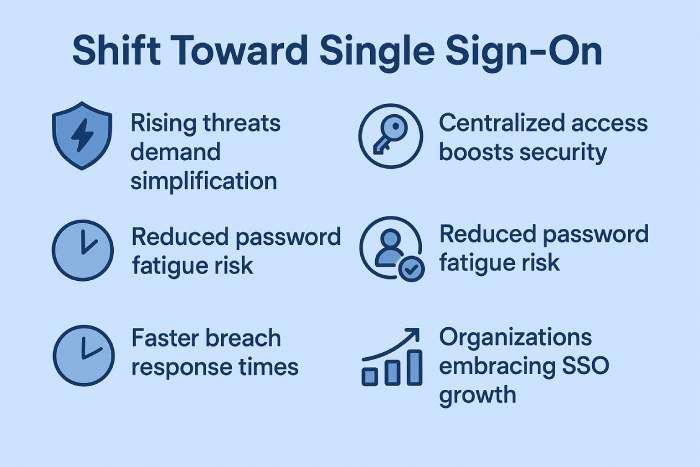
Passkeys over weak passwords— new tactic to combat cyberattacks
Threat actors have already come a long way–thanks to easy AI access and digital advancements around the globe. We are living in a time where even some of the intricate security setups are not adequate to tackle the malicious attempts of the cybercriminals. To make things worse, employees are still using weak passwords in 2025. Organizations are therefore gradually moving to passwordless solutions to safeguard critical business data.

Multifactor Authentication is still a valid alternative. But experts feel that using MFA alone is not enough to protect your data from threat actors. A massive 96% of CISOs believe that MFA is not competent enough to survive the contemporary threat landscape. Organizations have come to realize that password hygiene has its own set of disadvantages and that they need something better to protect their business data. So, gradually, they are moving to a completely new solution altogether—passwordless systems.
According to a survey conducted by Dark Reading, one-third of the participants have entirely shifted to Single Sign-On (SSO) or a passkey system to log into their accounts. One-fifth of the participants depend on password managers, which, again, is a comparatively safer solution for password authentication. 17% of the participants are coerced into using secure passphrases that are random in nature yet easy to remember.
Cybersecurity experts believe that more and more organizations will eventually move to SSOs as the threat landscape keeps evolving.
Google seeks help from the US court to dismantle Lighthouse phishing-as-a-Service operations!
Google needs the assistance of the US court to stop the Lighthouse Phishing-as-a-Service operations. This is a smart move made by the tech company to make the most out of legal systems to combat cybercrime.
Google sought legal help as the cybercrooks have been abusing Google and other similar tech brands by misusing their trademarks, logos, and other brand assets. A Google spokesperson stated that as many as 107 fake websites were “featuring Google’s branding on sign-in screens” to trick people and earn their trust.
Basically, cybercrooks who use Lighthouse services tend to send malicious text messages to unsuspecting users, especially employees in any organization. These threat actors use the brand assets of popular companies to boost the credibility of the messages and hope to compel the message recipients to click on fraudulent links or share sensitive data.
This is not the first time that a renowned tech company has sought the court’s help. There are several other well-known companies that have started seeking legal help to fight cybercriminals. For example, back in September, Microsoft got the court’s order to seize as many as 338 websites. These fraudulent websites were using a phishing kit called RacoonO365 to get access to Microsoft 365 credentials. In August, too, something similar happened when the US Justice Department, with the help of the FBI and other enforcement agencies, took down four servers and nine domains of the BlackSuit Ransomware group.
Why do manufacturers need to take more precautionary steps against ransomware?
Ransomware attackers love targeting manufacturers. From German manufacturer Schumag to Sensata Technologies, and then to Nucor, ransomware gangs targeted every manufacturing company, disrupting production and distribution.
According to the software firm Check Point, the global manufacturing sector experiences 1585 weekly attacks on average.
While some of the attacks are carried out by state-sponsored hacking groups for industrial espionage purposes, other ransomware attacks are financially motivated. The main reason behind targeting the manufacturing sector is the critical nature of its operational continuity.
That’s exactly why manufacturers must start building a robust, impenetrable safety system to prevent any cyberattack. It is advisable to use crisis communication strategies and intelligence-led defence systems to safeguard intellectual properties. Experts recommend investing in data-loss prevention, monitoring, and advanced detection systems.
Cyber resilience is no longer a luxury but a necessity for the manufacturing sector. It not only brings in the element of competitive advantage but also protects the future of a manufacturing business.







