The Emergence of DKIM: A Cryptography-Based Email Authentication Protocol
Navigating through the complexities of email security and the limitations of SPF, the urgency to develop a protocol that doesn’t break on email forwarding was needed. This led to the genesis of DomainKeys Identified Mail or DKIM. Its roots date back to the early 2000s when email-based cybercrimes were escalating. This led to the initiation of a collaborative effort by a group of industry experts, including Mark Delany, Philip Hallam-Baker, and others.
Here’s a more detailed walk-through of its introduction, evolution, and present structure.
Merger and Evolution

DKIM was developed to satisfy the need to replace the old and inefficient Simple Mail Transfer Protocol; later, DKIM became an integral part of DMARC in coordination with SPF. The story began with the merging of Cisco’s Identified Internet Mail (IIM) in 2007, which was then a standardized email authentication method that combined the best elements of DomainKeys and Identified Internet Mail.
Jim Fenton and Michael Thomas created IIM, which uses a public/private pair of cryptographically secured keys that verify an email’s authenticity. It decides if a message should be accepted or rejected based on a basic binary system concept. Yahoo’s DomainKeys was developed and introduced by Mark Delany in 2004, and its primary version underwent improvisation by other team members.
In the following years, DKIM got recognition, and its scope of expansion allowed it to get published as an open standard in RFC 4871, behaving as a framework for email users to digitally sign their messages so that recipients’ mail servers could verify their authenticity.
Yahoo’s DomainKeys
Yahoo’s DomainKeys was introduced to put in place a mechanism that could verify the sender’s authenticity and ensure the email body wasn’t tampered with in transit. The approach relied on rapid assessments using a binary “yes or no” method, directing emails either to the spam folder or the inbox.
It’s based on signatures and originally utilized a key pair; public and private keys.
While the process bears a resemblance to contemporary DKIM protocols, its execution is more intricate. It involved two distinct procedures: one from sending servers and another from receiving servers.
DomainKeys, crafted by Yahoo!, aimed to assist organizations such as banks and e-commerce stores in countering email spoofing and phishing attacks while safeguarding users. This initial open-standard authentication concept would later evolve into the DKIM we recognize today, thanks to collaborative efforts from industry leaders like IBM, Microsoft, VeriSign, and CISCO.
Cisco’s Identified Internet Mail
IIM by Cisco works as a medium to implement cryptographic signatures to email messages so that receiving servers can verify if the sender is actually who they are claiming to be. A receiver’s server performs the verification check by matching the digital signature.
Mail Transfer Agents (MTAs) or Mail User Agents (MUAs) play a vital role in the authentication process, and email administrators operate this system with their help.
IIM was developed for another purpose than just filtering spoofed emails; it allows email receivers to classify and prioritize desired emails.
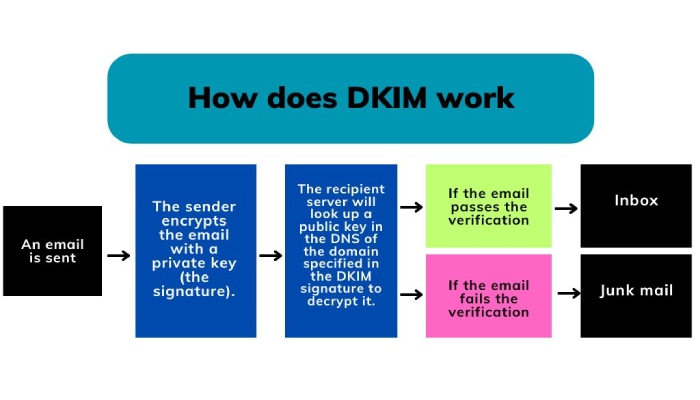
The Robust Duo
In 2007, both Yahoo and Cisco came together with their technologies to merge them into what we know today as DKIM or Domain Keys Identified Mail protocol. Their joint efforts led to the establishment of a base for the IETF standards that consequently paved a path for the formation of STD 76, which is now popular as the RFC 6376– a document formed and published in 2011.
Initially, it was challenging for DKIM to align well with different email service providers. However, after thorough tests and improvisations, it got along with Yahoo, Gmail, AOL, and FastMail. During its initial phase, its strict verification mechanism ended up discarding hundreds and thousands of emails due to the absence of digital signatures.
In the beginning, its users altered their mail list software rather than making changes to DKIM.
Significance in the Modern Landscape
In the contemporary digital landscape, where cyber threats continue to evolve, DKIM remains a crucial component of the email authentication ecosystem. It plays a pivotal role in preventing email spoofing, phishing attacks, and the manipulation of email content.
DKIM works with other email authentication protocols, such as SPF (Sender Policy Framework) and DMARC (Domain-based Message Authentication, Reporting, and Conformance), to provide a multi-layered defense against malicious activities. Collectively, these protocols contribute to the establishment of a secure and trustworthy email environment.







