What are the privacy concerns associated with DMARC reports, and how can you address them?

When you implement DMARC, you do not just do it for the policy enforcement feature; it’s also the reporting aspect that makes the authentication protocol so effective. These reports give you a behind-the-scenes view of your email activity, from who is sending emails on your behalf, how those emails are being authenticated, to any suspicious emails that might slip in.
The comprehensive, detailed information that these reports share is extremely useful, but only as long as they are in the right hands and are handled with care.
The thing with such extensive data is that it can easily become a liability, especially if it gets into the wrong hands or is mishandled. And since DMARC reports reveal almost everything about your email activity, they come with a few privacy concerns. These concerns aren’t about message content but about the metadata details that can still be sensitive if exposed.
In this article, we will understand what exactly the privacy concerns are associated with DMARC reports and how you can prevent them.

What are the privacy concerns that come with DMARC reports?
DMARC reports certainly come with a few privacy-related issues that you should be wary of. This is a major concern, especially with forensic (RUF) reports. These reports can include parts of the actual email, like some headers and sometimes even parts of the message body. This can become an even bigger problem if your email contains sensitive information, such as financial details, personal data, internal conversations, or anything confidential. If these reports reach a mailbox that isn’t secure or is handled by someone outside your organisation, that sensitive information can get exposed very easily.
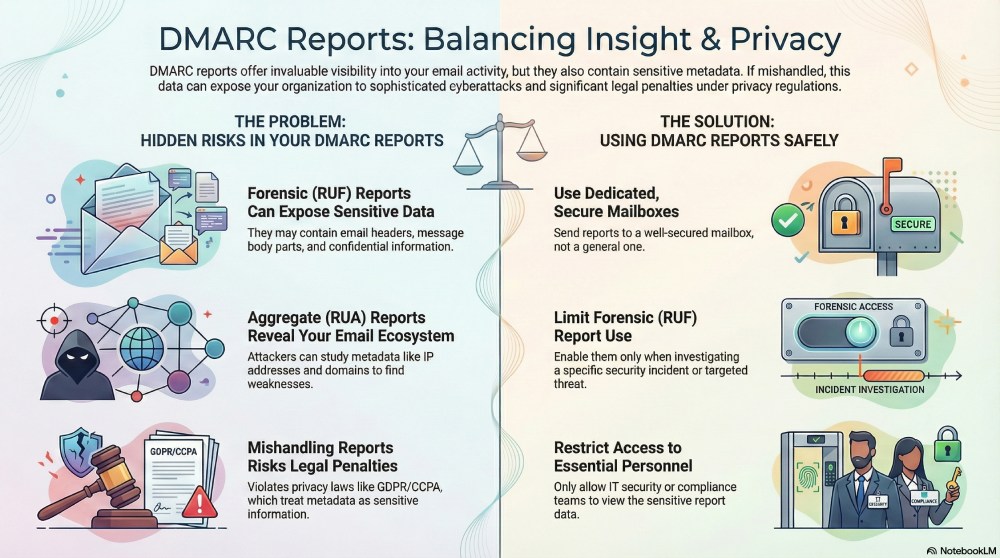
Apart from this, even your aggregate (RUA) reports run the risk of revealing sensitive information to someone who shouldn’t have access to them. Although these reports don’t show the actual content of the email, they do contain a lot of useful metadata like the IP addresses sending mail on your behalf, the domains involved, how often emails are sent, and whether authentication is passing or failing. These details act like bait for attackers because they give them a lot of information they can use against you.
Now, when the attacker studies this metadata collected over time, they can learn everything there is to know about your email ecosystem; from how often you send emails to which services you use, and where your authentication might be weak. Once they have this information, it becomes easier for them to plan and execute their attacks.

Moreover, from a compliance perspective, DMARC reports need to be handled well because many privacy laws treat metadata as sensitive information. So, if your organization falls under regulations such as GDPR, CCPA, or similar rules, it is important that you protect any data that could reveal sensitive information. If these reports aren’t handled properly, you could run into issues. For example, if they are stored in an insecure place, shared with too many people, or kept longer than necessary, you could accidentally break these privacy rules. If you don’t comply with these standards, you could end up with complaints, penalties, or other legal trouble.
How can you prevent these issues while using DMARC reports?
Yes, using DMARC reports raises privacy concerns, but that does not mean you should avoid them altogether. That will do you more harm than good.
Here’s how you can find a middle ground and use DMARC reports safely without putting your organisation at risk.
Use secure and controlled mailboxes

Many organizations make the mistake of sending DMARC reports to random mailboxes that are not as secure as they should be. This is risky because anyone with access to that mailbox can view or misuse the sensitive information contained in RUA and RUF reports. To prevent this, use a dedicated, well-secured mailbox for DMARC reports and restrict access to only the people who truly need it, such as your IT security or compliance teams.
Limit forensic reports
Forensic reports are undeniably very detailed, but they also come with the highest privacy risk because they may include parts of the email and details about the people involved. For monitoring your day-to-day email activity, aggregate (RUA) reports are usually enough; you don’t need to delve deeper with RUF reports. Only turn on forensic reports when you really need them, for example, if you’re investigating a specific security issue or tracking a targeted phishing attempt.

Limit access to these reports
If everyone in your organisation can see your DMARC reports, even when they don’t need them, you’re creating unnecessary risk. These reports can reveal technical details about your email activity, and sometimes even information about your systems, partners, or recipients. To stay safe, make sure that you keep access limited.
Want to get insights into your email activity while maintaining privacy? Contact us!







