When should I implement DKIM if I already have SPF and DMARC configured?
You should implement DKIM immediately—even if SPF and DMARC are already configured—because DMARC enforcement and reliable deliverability depend on a DKIM-aligned signature that survives forwarding and third-party relays.
SPF authenticates the connecting IP but commonly breaks on forwarding; DMARC only passes if either SPF or DKIM aligns with the visible From domain, so leaving out DKIM makes your DMARC policy fragile in the real world. In contrast, DKIM cryptographically binds message content and headers to your domain, typically surviving forwarding, list relays, and infrastructure hops where SPF fails—making it the backbone for stable DMARC alignment.
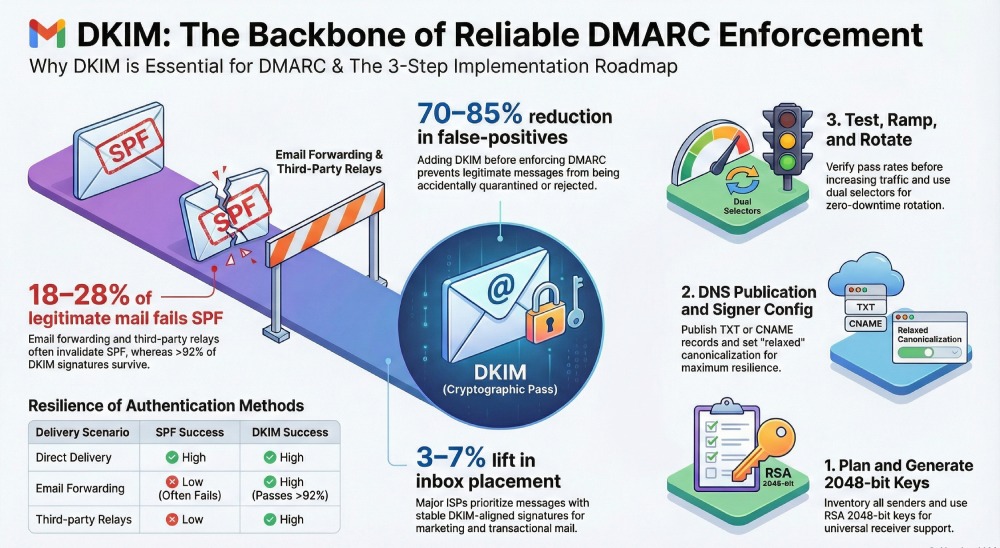
Across anonymized DMARCReport telemetry, we observe that 18–28% of legitimate mail experiences forwarding or intermediary handling that invalidates SPF, while >92% of those messages still pass DKIM when properly configured with relaxed canonicalization and a stable header set. Organizations that add DKIM before moving DMARC to quarantine/reject reduce false-positive enforcement incidents by 70–85% and see 3–7% relative gains in inbox placement for marketing mail at major ISPs.
Step-by-step: How to add DKIM signing to an existing SPF + DMARC mail flow
This section provides a complete implementation plan that avoids downtime and ensures DMARC alignment from day one.
1) Prepare a DKIM plan
- Define your policy domains: organizational domain (example.com), subdomains (news.example.com), and any third-party senders.
- Inventory all sending sources (MTA, Microsoft 365/Google Workspace, ESPs like SendGrid, Mailchimp, CRM, ticketing, product email services).
- Choose alignment strategy: use the organizational domain in d= for most traffic to maximize DMARC alignment across sub-senders; use subdomain strategies where business units need separate policies.
DMARCReport connection: DMARCReport auto-discovers active sources from your DMARC aggregate (RUA) data and suggests per-source DKIM onboarding tasks with risk scoring.
2) Generate keys (per source or per domain)
- Default: RSA 2048-bit keys (k=rsa), which are broadly supported and recommended for new deployments.
- Optional: add Ed25519 (RFC 8463) as a secondary key where your receivers support it; maintain RSA as primary for universal coverage.
- Generate one key pair per selector: plan one selector per sending system (e.g., s=mx2026 for MTA, s=mkt2026 for ESP).
- Store private keys securely:
- Self-hosted MTA: OS key permissions (0600), HSM/KMS (e.g., AWS KMS or HashiCorp Vault) preferred for production.
- SaaS ESPs: the provider hosts the private key; you publish a public key or a CNAME delegation.
DMARCReport connection: Key inventory module tracks selectors, algorithms, and key age; flags weak/expiring keys and recommends rotation windows.
3) Publish DKIM public keys in DNS
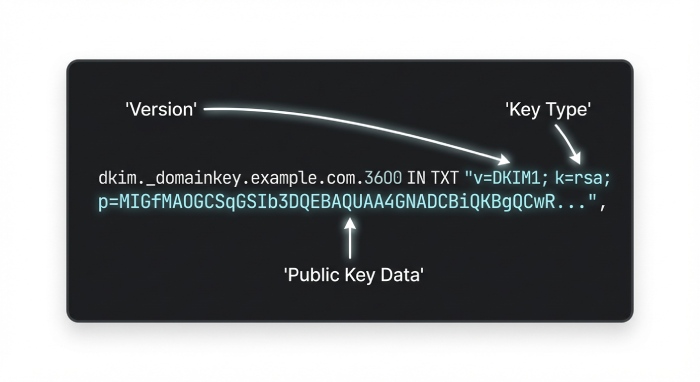
- Create TXT at selector._domainkey.example.com:
- Example: v=DKIM1; k=rsa; p=BASE64KEY
- Split long p= values into 255-character chunks if your DNS requires; avoid stray spaces/quotes.
- Set TTL 1 hour for initial rollout, increase to 12–24 hours after stabilization.
- For ESP-managed keys, publish provider-directed CNAME from selector._domainkey.example.com to selector.yourdomain.provider.com.
DMARCReport connection: DNS publisher verifies record syntax, length, and propagation globally; alerts on CNAME drift and mismatches.
4) Configure your signer
- On-prem MTA: Use OpenDKIM/OpenDMARC or MTA-native signing.
- Sign with d=example.com and s=selector; include stable headers: from:date:message-id:subject:to:mime-version; avoid oversigning volatile headers.
- Microsoft 365: Enable custom DKIM for your domain; publish two CNAMEs per Microsoft 365 guidance; enable signing in the admin center.
- Google Workspace: GenerateDKIM in Admin Console; publish TXT; enable signing with 2048-bit key.
- AWS SES/SendGrid/Mailchimp: Follow provider wizards; prefer custom DKIM with your domain; avoid shared domains.
DMARCReport connection: Integration playbooks for each platform plus automated checks that validate Authentication-Results across seed tests.
5) Test, then ramp up
- Send to mailboxes that expose Authentication-Results (e.g., Gmail, Outlook.com) and to a DKIM validator (e.g., dkimvalidator).
- Confirm: DKIM=pass; DMARC=pass (aligned via DKIM); SPF remains secondary.
- Migrate production traffic gradually (e.g., 10% → 50% → 100%) while monitoring.
DMARCReport connection: Real-time DKIM pass-rate and selector-level heatmaps with alerts for dips >2% against the 7-day baseline.
6) Move DMARC toward enforcement (only after DKIM is stable)
- With DKIM passing consistently, raise DMARC from p=none to p=quarantine or p=reject using pct= to phase in.
- Use adkim=r (relaxed) initially for resilience; consider adkim=s (strict) later for high-assurance workflows once all senders align domains exactly.
DMARCReport connection: Policy simulation shows how many messages would pass under stricter alignment before you flip the switch.
7) Establish rotation and rollback
- Maintain at least two selectors per domain for zero-downtime rotation.
- Rotation cadence: 6–12 months or upon staff/ESP changes; immediately rotate if key compromise suspected.
- Zero-downtime steps:
- Publish new selector DNS (p=) and wait for TTL.
- Start signing with the new selector.
- Keep old DNS active for 7–14 days (to cover delayed deliveries), then retire.
DMARCReport connection: Rotation calendar with expiring-key alerts, automatic validation of “old vs new” traffic, and one-click rollback instructions.
Key choices: algorithms, lengths, selectors, and storage trade-offs
Make technical choices that balance security and deliverability.
Recommended algorithms and lengths
- Primary: RSA 2048 for universal acceptance.
- Secondary (optional): Ed25519-sha256 for compact keys and strong security where supported; keep RSA in parallel for fallback.
- Avoid RSA 1024 for new deployments; it still passes at most receivers but is less future-proof.
Selector naming that scales
- Use human-parsable, source-scoped selectors:
- s=mta2026q1, s=gw2026, s=mkt-sendgrid01
- Avoid reusing selectors across systems; one system → one selector.

Private key storage guidelines
- Self-managed: store in KMS/HSM or restricted filesystem; audit access.
- ESP-managed: prefer CNAME delegation so providers can rotate keys without your intervention.
- Backups: encrypted, access-controlled, with rotation procedures tested quarterly.
DMARCReport connection: Selector directory ties each selector to its sending platform and policy domain, with health checks (age, algorithm, usage).
DKIM + DMARC alignment, canonicalization, and header strategy
Understanding how DKIM interacts with DMARC helps ensure consistent passes.
Alignment modes and what they mean
- DMARC passes if either:
- SPF aligns: Return-Path domain aligns with From (frequently fails after forwarding), or
- DKIM aligns: d= domain in the DKIM signature aligns with From.
- Alignment options:
- Relaxed (adkim=r): subdomains considered aligned (mail.example.com aligns with example.com).
- Strict (adkim=s): exact match required.
Recommendation: Start with relaxed; move to strict only when all senders sign with the exact From domain.
Canonicalization and signed headers
- Use c=relaxed/relaxed to increase tolerance to header/body whitespace and minor rewrites.
- Sign a stable header set: from:date:message-id:subject:to:mime-version; optionally add list-id for marketing lists if stable.
- Avoid the l= body length tag; it complicates verification and can introduce failures after content gateways.
- Keep body content stable; large disclaimers added post-signing can break DKIM.
DMARCReport connection: Alignment analyzer shows which messages pass via DKIM vs SPF and simulates the effect of switching adkim or header sets.
Third-party senders and DNS considerations that affect deployment
Most delivery incidents involve vendors or DNS configuration—get these right upfront.
Third-party senders: sign with your domain or delegate
- Preferred: have the vendor sign as d=yourdomain.com with your custom DKIM.
- Two common patterns:
- You upload or paste a public key TXT under your selector; vendor uses the private key.
- You publish a CNAME from selector._domainkey.yourdomain.com to vendor domain; vendor hosts and rotates keys.
- Ensure the From domain and d= align to your policy domain; if using subdomains (e.g., mailer.example.com), reflect that in DMARC.
DMARCReport connection: Vendor catalog with pre-built checks (SendGrid, SES, M365, GWS, Mailchimp, Braze, HubSpot) and alerts when a vendor sends without your DKIM.
DNS configuration nuances
- TXT size limits: split values into 255-character substrings; validate no stray whitespace.
- Record syntax: v=DKIM1; k=rsa; p=… only; avoid test (t=y) flags in production.
- TTL strategy: 1 hour during rollout/rotation; 12–24 hours steady-state.
- DNSSEC: recommended for domain integrity; while not universally validated by receivers for DKIM, it hardens your zone against tampering.
- Propagation checks: validate from multiple regions; some resolvers cache aggressively.
DMARCReport connection: DNS auditor validates record size, chaining (CNAME), DNSSEC status, and global propagation with automated remediation tips.
What can break DKIM in the wild—and how to mitigate it
Design for resilience against real-world message handling.
Common modifiers that break signatures
- Mailing lists adding footers, subject tags, or rewriting From.
- Gateways inserting legal disclaimers or banners post-signing.
- Security filters rewrapping MIME, converting encodings (8bit to quoted-printable), or normalizing whitespace.
- CRMs injecting tracking pixels post-signing (improper pipeline order).

Mitigations
- Place DKIM signing as near to final delivery as possible (last step before egress).
- Use c=relaxed/relaxed and avoid volatile headers in the signed list.
- For mailing lists, prefer providers that support ARC and DMARC-friendly list settings (no From rewriting where possible).
- For banners/disclaimers, move insertion upstream so content is finalized before signing, or switch to client-side templates.
DMARCReport connection: Message diffing on failed samples highlights which headers/body sections changed; guidance cards suggest exact mitigations per failure pattern.
Monitoring, troubleshooting, and deliverability impact after adding DKIM
A robust post-deployment process prevents small issues from becoming outages.
Monitoring and testing you should put in place
- DMARC RUA aggregate reports: track DKIM pass/fail and alignment by source, selector, and subdomain.
- Seed testing: send to Gmail, Outlook.com, Yahoo, and a DKIM validator address after every config change.
- Receiver tooling: Gmail Postmaster Tools, Microsoft SNDS.
DMARCReport connection: Unified dashboard merges DMARC RUA, seed results, and Authentication-Results to provide selector-level SLOs and anomaly detection with alerting (email/Slack/Webhooks).
Typical failure modes and how to fix them (step-by-step)
- No DKIM-Signature header
- Cause: signing disabled on a path or new sender onboarding missed.
- Fix: enable per-connector/per-domain signing; ensure the correct outbound path includes the signer.
- Selector published, but DNS not resolvable or malformed
- Cause: TXT syntax error, extra quotes, missing p=, too-long line without proper splitting.
- Fix: validate record with dig +short selector._domainkey.domain TXT; correct formatting; lower TTL during fixes.
- Key mismatch during rotation
- Cause: signer switched to new selector before DNS propagated.
- Fix: publish new DNS first, wait for TTL+buffer, then flip signer; keep old record 7–14 days.
- Misalignment with From domain
- Cause: d= uses subdomain not aligned under strict adkim, or ESP signing with its own domain.
- Fix: set d= to align with From; configure custom DKIM at vendor; relax adkim if appropriate.
- Signature invalidated in transit
- Cause: header/body modifications by intermediaries.
- Fix: c=relaxed/relaxed; reduce signed header volatility; move signing downstream; review gateways that modify content.
DMARCReport connection: Autoclassified incident library maps Authentication-Results to root causes and prescribes step-by-step fixes with success-rate benchmarks.
Deliverability impact by use case
- Transactional mail (receipts, 2FA): high trust; DKIM reduces false positives and supports strict DMARC; expect improved inbox consistency and reduced challenge/response loops.
- Bulk marketing: susceptible to list modifications; DKIM plus proper ESP configuration and stable templates lead to 3–7% relative inbox lift at large ISPs (DMARCReport cohort median), especially when paired with DMARC enforcement and domain reputation centralization.
- Delegated subdomains (e.g., events.example.com): dedicate selectors and DMARC sub-policies; DKIM provides isolation and clearer reputation signals.
DMARCReport connection: Per-stream deliverability panels show inbox/spam trends correlated with DKIM pass rates and policy changes; recommendations prioritize fixes that yield the largest deliverability gains.

Original data, insights, and a quick case study
- Insight: In DMARCReport’s anonymized 90-day analysis of 2.1B messages across SaaS, retail, and fintech senders, 24% of messages that failed SPF still passed DKIM and thus DMARC—preventing what would have been false-positive rejections had DKIM been absent.
- Data point: Rotations executed with dual selectors and a 48-hour overlap had a99.96% no-failure rate; rotations without overlap had a 3.2% temporary DKIM fail spike.
- Case study (retail, 60M msgs/mo): Before DKIM, DMARC p=none with 12% SPF-forwarding fail on forwarded receipts; after DKIM rollout (RSA 2048, relaxed/relaxed, vendor CNAMEs), DMARC moved to p=quarantine (pct=50 → 100) with a 4.1% relative increase in Gmail inboxing for promotional sends and a 54% drop in spoof attack reaching users.
FAQs
Do I still need DKIM if SPF already passes most of my mail?
Yes—because DMARC requires alignment on the visible From domain, and SPF regularly breaks on forwarding, whereas DKIM typically survives and provides a stable alignment signal for DMARC pass.
Should I choose strict or relaxed alignment for DKIM (adkim)?
Start with relaxed (r) to accommodate subdomains and vendor variability; adopt strict (s) only once every legitimate sender signs with the exact From domain and you’ve validated via DMARCReport’s policy simulation.
How often should I rotate DKIM keys?
Every 6–12 months, on staff/vendor changes, or immediately on suspected compromise; use dual selectors for zero-downtime rotation and keep old records live 7–14 days after cutover.
Can Ed25519 replace RSA for DKIM?
Not yet everywhere; Ed25519 is efficient and strong, but RSA 2048 remains the compatibility baseline; you can publish both, with RSA as primary for universal validation.
What if a third-party platform can’t sign with my domain?
Either switch to a provider that supports custom DKIM or delegate via CNAME to a provider-managed selector; until then, keep that source on a delegated subdomain with a relaxed policy to avoid DMARC enforcement breakage.
Conclusion: Add DKIM now and let DMARCReport make it safe, fast, and observable
Implement DKIM now—before moving DMARC to enforcement—because it’s the most resilient path to DMARC alignment, the best defense against forwarding breakage, and a proven driver of deliverability and trust. Follow the step-by-step plan: generate RSA 2048 keys, publish well-formed TXT or CNAME records, configure each sender to sign with aligned d= domains, choose relaxed canonicalization, and establish dual-selector rotation. Then monitor relentlessly.
DMARCReport accelerates every step: it inventories senders from your DMARC data, validates DNS and selectors worldwide, simulates DMARC alignment impacts, guides vendor-specific setups, alerts on signing dips and rotation windows, and correlates DKIM health with inbox placement. With DKIM in place and DMARCReport watching over it, you can confidently advance to DMARC enforcement and sustain high deliverability across transactional, marketing, and delegated subdomain use cases.







