How Often Should You Rotate Your DKIM Keys?
DKIM, which is short for DomainKeys Identified Mail, is an email authentication method that supports a receiver’s email server in verifying if the signed fields of an incoming email have been tampered with in transit or not. This phenomenon is performed by matching the public and private keys at the recipient’s end.
As per M3AAWG or the Messaging, Malware, and Mobile Anti-Abuse Working Group, domain owners and administrators should regularly rotate DKIM keys to minimize the risk of being compromised by malicious actors for attempting phishing and email spoofing attacks.
But why is this practice critical, and how can you rotate your DKIM keys? Well, please keep reading as we have answered these and some other vital questions in this article.
DKIM and DKIM Keys
DKIM lets receivers know if a hacker or unauthorized entity altered the content of an email in transit. To begin with, you need to generate a pair of public and private keys. The public key is stored in the DNS, and email servers can retrieve it for the authentication process. On the other hand, the private key is secretly stored on the sender’s server and generates appropriate DKIM headers for all outgoing messages.
There are DKIM keys of various lengths. The lengthier the key, the more complicated it is for spammers to crack it. For example, 512-bit long RSA keys can be cracked in several hours, while 1024-bit long RSA keys are highly recommended as they are presently at the edge of attack for general-purpose computer systems. UI also warns if the length is less than 1024 bits, as it is considered a vulnerability.
In fact, in 2012, a mathematician found that Google was using a 512-bit DKIM key, and he was so intrigued by discovering this that he himself sent spoofed emails to Google founders- Larry Page and Sergey Brinn. Later, he also noticed the same problem with the DKIM keys used by PayPal, Yahoo, Amazon, eBay, Apple, Dell, LinkedIn, Twitter, SBCGlobal, US Bank, HP, Match.com, and HSBC.
What is a DKIM Selector?
Why Should You Rotate DKIM Keys Periodically?
DKIM key rotation is the practice of using a new pair of public and private DKIM keys to sign and authenticate outgoing messages and then STOP using old keys.
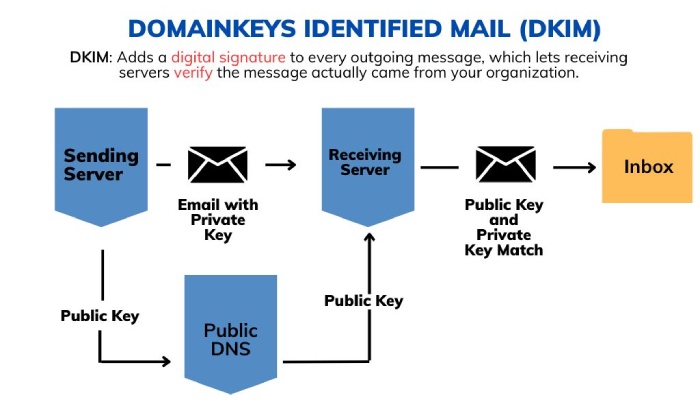
It’s important for organizations to follow this practice for DKIM keys associated with their domains to prevent phishing attacks. If a malicious sender has hacked your keys, then they won’t be able to exploit them for sending spam messages to manipulate recipients for a long time; as soon as you shuffle the keys, they will lose access to them.
How Often Should Signing Keys Be Rotated?
It’s critically important to have longer keys, but their regular rotation shouldn’t be overlooked for safeguarding your DKIM DNS records and domains. However, the period of shuffle depends on the complexity of data and your company, the time taken to rotate keys, the perceived value of the protected email streams, and the organization’s susceptibility to spoofing and phishing attacks.
The M3AAWG suggests domain owners rotate them at least twice a year to minimize the likelihood of compromised keys and operational effort. This also institutionalizes knowledge of key shuffling.
Opting for more frequent rotations, like on a quarterly basis, reduces the risk of key compromise but may be hindered by operational constraints. Conversely, extending the rotation interval, such as annually, not only heightens the risk of key compromise but also diminishes the accrued institutional knowledge’s significance.
How to Manually Rotate DKIM Keys?
Making the following changes to your DKIM TXT record in the following way will stop an unauthorized entity from sending a fraudulent email message on your behalf-
- Go to Google and look for an online DKIM record generator.
- Enter your domain name, followed by mentioning your DKIM selector.
- Now, you will get a new pair of keys to publish on your DNS, replacing the old ones.
- Finally, share the private key with your email service provider or upload it on your mail server if an in-house member handles your emails.
Subdomain Delegation
Utilizing external services for periodic DKIM key rotation for your domain allows you to redirect your focus to other duties and relieve yourself of DKIM management and upkeep the responsibility.
CNAME Delegation
CNAME delegation empowers domain owners to route DKIM record information through a third-party vendor. It resembles subdomain delegation, where you only need to publish specific CNAME records in your DNS, and the contracted third party takes charge of the key rotation process.
How to Automatically Rotate DKIM Keys?
There are email vendors and outsourced email service providers that support automatic DKIM key rotation for users to make the process easier and reduce the chances of mistakes. Moreover, this saves time spent in zeroing down, troubleshooting, and synchronizing remedies for ruling and inclusive DKIM issues.
Auditing
As per the security policy of your organization, you should conduct regular audits of your DKIM key rotation. This should be practiced shortly after a rotation, for example, approximately after a week or 10 days, to verify the keys have been appropriately shuffled. Next, begin to gather all the required information in a data repository as soon as you establish the key rotation process. Ensure maintaining a record of all domains and subdomains for each mail stream within your business entity, along with DKIM selectors. Don’t forget to keep track of the time frames of the activities.
To perform an audit, compare the current combination of the domain (“d=” value in the DKIM signature) and selector (“s=”) for a specific message with the expected values stored in your DKIM rotation data repository. Maintaining a structured selector naming convention will make ad-hoc audits more efficient and can serve as the foundation for automated auditing.
Final Words

SPF, DKIM, and DMARC work collectively to address email deliverability and security issues. DKIM signatures are added to email headers of messages sent to your customers, prospects, employees, stakeholders, etc., and are secured by the cryptography method. Such an email infrastructure remains safe if you use long DKIM keys and rotate them regularly in your DNS TXT record. DKIM protocol works on the end-to-end encryption model and informs if email messages are altered by suspicious sources in transit.






