Understanding Ransomware As a Service (RaaS)
Now, ransom threats have taken the digital route as well! Cybercriminals attempt them using ransomware, which are basically malicious software and tools used to block access to a device or network of devices until the victim pays off the demanded amount.
The global ransomware damage cost is anticipated to exceed $265 billion by 2031, and as of 2023, over 72 percent of organizations worldwide have been affected by ransomware attacks. Don’t these figures sound substantial and scary?
Well, let us scare you a little more! The introduction and expansion of ransomware as a service, or RaaS, has expedited the exploitation process, bringing more victims under the radar of ransomware attackers.
What is Ransomware?
Ransomware is a malware type that blocks or limits users from accessing data, files, or devices until ransom payments are paid. Hackers trick targets into downloading ransomware on their systems through phishing attacks, in addition to deploying some form of social engineering tactics.
In some scenarios, a victim unknowingly downloads a spiteful code from fraudulent emails or by visiting cloned or spoofed websites through malvertisements (short for malicious advertisements) selling lucrative products. Another way of a breach is to drop them off through exploit kits onto a system or network infrastructure with security vulnerabilities.
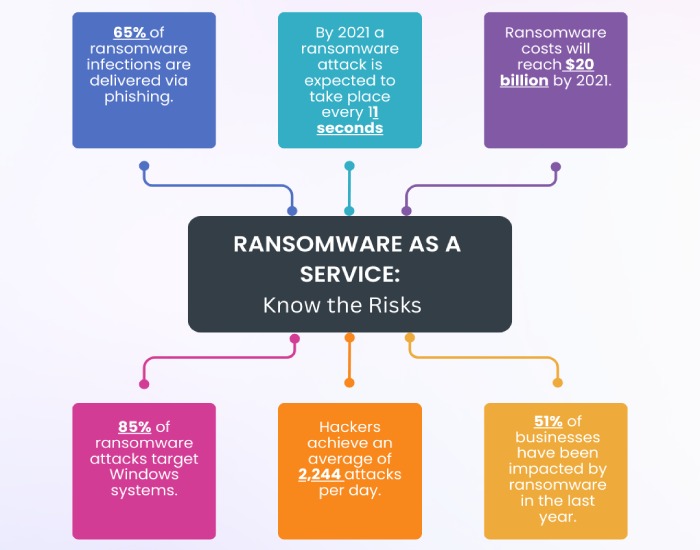
What is Ransomware as a Service or RaaS?
Ransomware as a service is a branch of software as a service (SaaS) business model in which ransomware attackers are their customers or subscribers. There are cybercriminals who lack the knowledge or time to develop their own ransomware, and RaaS operators help them out by developing and selling malicious software (products) as per their demand.
Just like SaaS providers’ packages, a RaaS kit also includes features like customer support, user reviews, user guidelines, forums, insights into activities, etc.
There are 4 general RaaS revenue models–
- Monthly subscription for a flat fee.
- Affiliate programs include a monthly subscription fee along with a percentage of the profits made from attacks.
- A single-time license fee with no profit-sharing scheme.
- Pure profit sharing.
Even these malicious services are getting sophisticated and organized. These days, RaaS organizations allow the subscribers of an affiliate model to log into their portal, create an account, make payments through Bitcoin and other cryptocurrencies, give a detailed description of the ransomware they require, and submit.
Real-Life Example of a Ransomware Attack
The first wave of the infamous Costa Rica attacks started on 17th April 2022, which was followed by the second wave on 31st May 2022.
The alleged culprit of the former cybersecurity attack was the ‘Conti Group’ while that of the latter was the ‘Hive Group.’ In this, the Russian perpetrators hit 27 different public institutions in Costa Rica. The Conti Group demanded a ransom of $20 million, while the Hive Group asked for $5 million in Bitcoin in exchange for decryption.
However, the government refused to curb the ransom demand and was forced to shut down a number of computer services associated with taxes, imports, and exports, leading to an economic loss of $125 million in the first 48 hours of the attack.
Examples of Ransomware as a Service
The dark web is flowing with cyber menaces, and the following are the leading names associated with RaaS:
LockBit
LockBit is a popular RaaS variant that is linked with as many as 17% of ransomware instances reported in 2022. Phishing emails and corrupted files are its common medium of commute, and the contribution of gangs has also been observed.
DarkSide
DarkSide is linked to the eCrime collective known as CARBON SPIDER. In a notable shift, DarkSide operatives are now focusing on Linux environments, specifically targeting business setups employing unencrypted VMware ESXi hypervisors or seeking to steal vCenter keys.
Traditionally, DarkSide has primarily directed its efforts towards Windows PCs. The ransomware tools used in the infamous Colonial Pipeline outbreak were linked with DarkSide.

Dharma
Dharma is one of the notorious groups in the ransomware market and is associated with the Iranian terror cell. This RaaS is available on the dark web and is mostly involved in RDP assaults. Threat actors ho deploy Dharma demand 1-5 Bitcoin cryptocurrency as a way to make a profit from exploitations. In its recent updates, there’s a provision of encryption and decryption keys.
Maze
Maze-based malicious operations started in 2019, where attackers breached victims’ information and shamed them by threatening to share it. However, the RaaS company behind Maze discontinued it and other ransomware tools in November 2020. There are speculations that now it goes by a different name, that is Egregor.
REvil
REvil is also identified as Sodinokibi and is behind some of the biggest ransomware operators and developers. PINCHY SPIDER is a criminal group that offers the Revil RaaS through a partnership model, keeping 40% of the earnings.
They warn victims about an upcoming data breach through a blog post on their DLS. They usually include a data preview as proof and release the rest later. The ransom message from REvil also includes a link to the blog post.
Prevention Against RaaS Attacks
The monetary loss and involvement of resources in recovering files are substantial, and it’s better to adopt safer cybersecurity practices to avoid being a victim of these menaces. Apart from endpoint protection and implementing zero trust security, here’s what you as an organization and your employees can do-
Cybersecurity Practices and Employee Awareness Training
Ransomware attacks are driven mainly by a response to phishing attempts, thus making it vital to work towards training your team, as they are the weakest line of defense for an organization. Conduct regular cybersecurity events and mock drills to ensure your staff is well prepared.
Regular Backup of Data
These attacks target confidential and private data, so securing them through backups and passwords should be a priority. We suggest you follow the steps of the 3-2-1 backup rule, according to which you should maintain three total copies of your data stored on two different media, with one copy kept offsite.
Updated Software
Needless to say, outdated technologies are full of vulnerabilities, allowing cyber criminals to penetrate systems without much work. Many AI-backed technologies on the dark web are already available that are specifically developed to target legacy systems.
On the other hand, updated versions have their loopholes patched and fixed, which helps keep hackers at a distance.
Final Words
In the end, it’s all about creating an infrastructure that is used by learned employees and is hard to get broken into by threat actors. Implementing proper email security using SPF, DKIM, and DMARC protocols is beneficial in protecting against ransomware attacks. These email authentication measures help ensure the legitimacy of incoming emails, preventing malicious actors from using deceptive techniques and reducing the risk of ransomware infiltrating your systems. To discuss anything related to email security, please reach out to our support team.







