8 Types of Phishing Attacks to Be Wary of
Phishing exists, and we all are well aware of it. However, we still end up getting trapped in the new tricks of scammers. These attacks surge specifically during the holiday seasons as people look for discounted gifts and household items. Threat actors create spoofed email addresses and websites to trap executives and attempt business email compromise or BEC scams.
Let’s see what the common types of phishing attacks are that we should be wary of to prevent losing our hard-earned money and reputation.
8 Types of Phishing Attacks
1. Email Phishing
Email phishing is a deceptive practice where attackers send fraudulent emails to users and potential customers on behalf of companies to trick them into sharing sensitive information, installing malware through links, transferring money, etc.
An example of email phishing is a fake email appearing to be from a reputable source, like a bank, requesting the recipient to click on a link and provide login credentials, leading to a fraudulent website designed to steal the information.
SPF, DKIM, and DMARC are email authentication and security protocols that organizations can deploy to prevent attackers from exploiting their domain name to send phishing emails.
2. Whaling
In whaling attacks, bad actors target high-profile individuals or employees like CXOs to fool them into sharing sensitive data and account credentials that are further compromised to gain access to their accounts or intercept information.
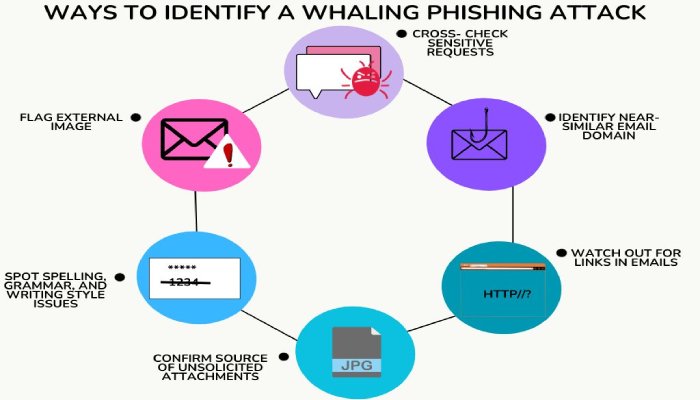
Generally, phishers impersonate a company’s CEO and send an urgent whaling email or text message to an executive or their partner, requesting them to do something at the earliest.
Usually, they email someone from the finance team, giving them an order to make payments or download malicious software. In these scenarios, the sense of urgency should be perceived as a warning of cybersecurity threats and data breaches.
3. Smishing and Vishing
Smishing and vishing are types of phishing attacks attempted using social engineering tactics, but they occur through different communication channels. Smishing involves the use of text messages or SMS to manipulate a user into sharing social media credentials or performing other specific actions.
Vishing or voice phishing, on the other hand, is another phishing attack type that is attempted over voice communication, usually a phone call. An example of vishing is an automated voice message pretending to be from a government agency or a financial institution, asking the recipient to call a specified number to verify account details. These cases further turn into ransomware instances.
4. Spear Phishing
This is one of the smartest phishing techniques, where cyber criminals design threats for specific individuals or organizations. It involves personalized message content and in-depth research on victims, aiming to trick them into revealing sensitive information or installing malware. These phishing scams are difficult to detect as hackers exploit personal details, making them appear more legitimate.

5. Search Engine Phishing or SEO Poisoning
In search engine phishing attempts, an attacker builds a fake website with attractive products. These products are then shown in online ads, luring victims to enter sensitive information to make the purchase. Later, hackers misuse these details.
One such phishing attack took place in the name of Booking.com, a popular hotel booking platform. In this, ads pop-ups, notifications, and phishing messages were sent to targets to redirect them to a cloned website. As of October 2023, customers have lost at least S$441,000 to this phishing scam.
6. HTTPS phishing
These types of phishing attacks and threats include a deceptive URL with the “https://” prefix to trick them into entering sensitive information. The mimicked content makes the website appear genuine, generally belonging to a bank, business, or government organization. Cybercriminals may use similar-looking URLs or employ tactics like homograph attacks, using visually similar characters to mimic legitimate domain names.
7. Pharming
Pharming is a type of phishing email attack where hackers send malicious codes or malware to targeted recipients in an attempt to steal their credentials and data. It’s a two-step process that begins when an attacker installs malicious code on the victim’s devices or server. The malicious code takes the victim to a fraudulent website that requests them to enter personal data or login credentials or use their online services.
8. Evil Twin Phishing
An evil twin phishing attack occurs when cyber criminals establish a deceptive Wi-Fi access point, aiming for users/ victims to connect to it rather than a genuine one. Upon connecting, all the data shared with the network is routed through a server controlled by the attacker. This malicious counterpart can be generated using a smartphone or other internet-capable devices along with easily accessible malware. Evil twin attacks are prevalent on unsecured public Wi-Fi networks, posing a threat to personal data security.
Final Words
Focusing on security awareness training, being wary of suspicious attachments, identifying and fixing vulnerabilities, and protecting your domains and devices (computers, smartphones, modems, etc.) are some ways to safeguard yourself from phishing campaigns.






